A formerly undocumented remote obtain trojan (RAT) prepared in the Go programming language has been spotted disproportionately targeting entities in Italy, Spain, and the U.K.
Identified as Nerbian RAT by business security company Proofpoint, the novel malware leverages COVID-19-themed lures to propagate as section of a low quantity email-borne phishing campaign that commenced on April 26, 2022.
“The freshly identified Nerbian RAT leverages numerous anti-examination factors spread across quite a few levels, including several open-source libraries,” Proofpoint scientists stated in a report shared with The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“It is composed in operating technique (OS) agnostic Go programming language, compiled for 64-bit programs, and leverages numerous encryption routines to even further evade network evaluation.”
The messages, amounting to less than 100 in quantity, purport to be from the Entire world Health and fitness Group about protection actions relevant to COVID-19, urging probable victims to open a macro-laced Microsoft Word doc to obtain the “newest well being suggestions.”
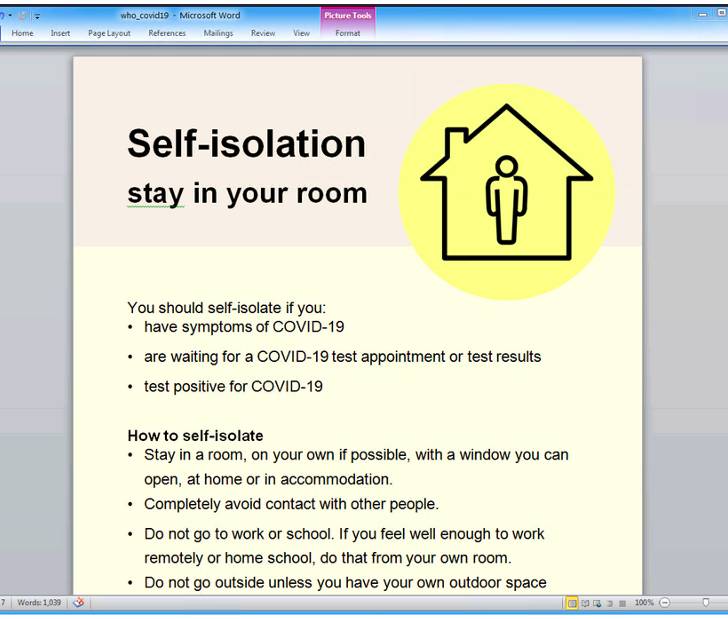
Enabling the macros shows COVID-19 direction, which includes ways for self-isolation, although in the track record, the embedded macro triggers an an infection chain that delivers a payload referred to as “UpdateUAV.exe”, which acts as dropper for Nerbian RAT (“MoUsoCore.exe”) from a remote server.
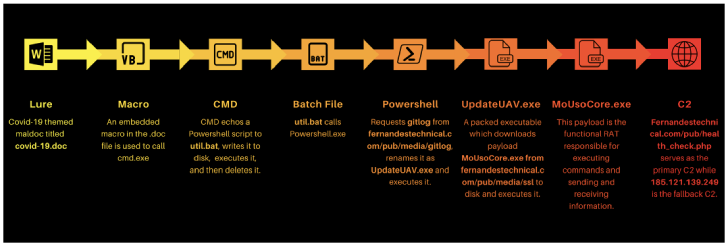
The dropper also would make use of the open-supply Chacal “anti-VM framework” to make reverse engineering challenging, working with it to carry out anti-reversing checks and terminating itself must it face any debuggers or memory evaluation applications.
The distant accessibility trojan, for its section, is outfitted to log keystrokes, capture screenshots, and execute arbitrary instructions, just before exfiltrating the final results back again to the server.
Although both of those the dropper and the RAT are stated to have been created by the exact writer, the id of the menace actor remains unfamiliar as however.
Moreover, Proofpoint cautioned that the dropper could be personalized to deliver distinctive payloads in future attacks, despite the fact that in its recent form, it can only retrieve the Nerbian RAT.
“Malware authors proceed to work at the intersection of open-resource functionality and prison prospect,” Sherrod DeGrippo, vice president of risk analysis and detection at Proofpoint, stated in a statement.
Identified this posting exciting? Abide by THN on Fb, Twitter and LinkedIn to browse much more special written content we submit.
Some areas of this write-up are sourced from:
thehackernews.com


![[white paper] social engineering: what you need to know to](https://thecybersecurity.news/data/2022/05/White-Paper-Social-Engineering-What-You-Need-to-Know-to-80x80.jpg) [White Paper] Social Engineering: What You Need to Know to Stay Resilient
[White Paper] Social Engineering: What You Need to Know to Stay Resilient