The Russia-linked menace actor regarded as APT29 focused European diplomatic missions and Ministries of Foreign Affairs as element of a series of spear-phishing campaigns mounted in Oct and November 2021.
In accordance to ESET’s T3 2021 Menace Report shared with The Hacker News, the intrusions paved the way for the deployment of Cobalt Strike Beacon on compromised systems, adopted by leveraging the foothold to drop supplemental malware for gathering facts about the hosts and other machines in the exact network.
Also tracked underneath the names The Dukes, Cozy Bear, and Nobelium, the innovative persistent threat group is an infamous cyber-espionage group that has been energetic for extra than a decade, with its attacks focusing on Europe and the U.S., before it obtained prevalent notice for the supply‐chain compromise of SolarWinds, major to additional bacterial infections in numerous downstream entities, together with U.S. authorities companies in 2020.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
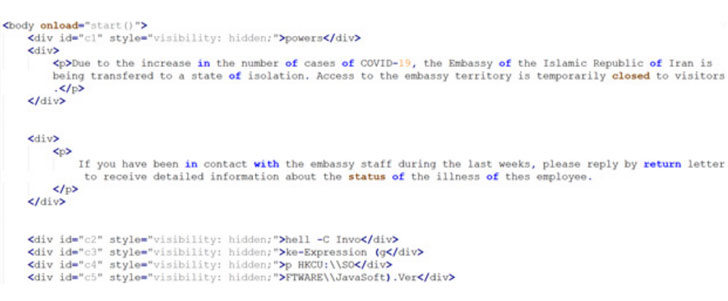
The spear-phishing attacks commenced with a COVID-19-themed phishing email impersonating the Iranian Ministry of Foreign Affairs and made up of an HTML attachment that, when opened, prompts the recipients to open up or help you save what seems to be an ISO disk impression file (“Covid.iso”).
Really should the sufferer decide to open or download the file,” a small piece of JavaScript decodes the ISO file, which is embedded immediately in the HTML attachment.” The disk graphic file, in change, incorporates an HTML software that’s executed utilizing mshta.exe to operate a piece of PowerShell code that in the end hundreds the Cobalt Strike Beacon onto the contaminated process.
ESET also characterised APT29’s reliance on HTML and ISO disk images (or VHDX files) as an evasion approach orchestrated especially to evade Mark of the Web (MOTW) protections, a security attribute introduced by Microsoft to ascertain the origin of a file.
“An ISO disk image won’t propagate the so-referred to as Mark of the Web to the information within the disk image,” the researchers mentioned. “As this sort of, and even if the ISO were being downloaded from the internet, no warning would be dis- performed to the sufferer when the HTA is opened.”
On efficiently attaining first accessibility, the menace actor delivered a assortment of off-the-shelf instruments to query the target’s Lively Listing (AdFind), execute instructions on a remote machine using SMB protocol (Sharp-SMBExec), have out reconnaissance (SharpView), and even an exploit for a Windows privilege escalation flaw (CVE-2021-36934) to have out follow-on attacks.
“Latest months have demonstrated that The Dukes are a major menace to western organizations, in particular in the diplomatic sector,” the scientists famous. “They are quite persistent, have great operational security, and they know how to produce convincing phishing messages.”
Discovered this report appealing? Adhere to THN on Fb, Twitter and LinkedIn to study much more distinctive written content we write-up.
Some parts of this post are sourced from:
thehackernews.com




 Home Workers More Likely to Be Concerned About Security
Home Workers More Likely to Be Concerned About Security