A new details wiper malware known as CryWiper has been uncovered focusing on Russian authorities organizations, like mayor’s workplaces and courts.
“While it disguises itself as a ransomware and extorts cash from the victim for ‘decrypting’ knowledge, [it] does not essentially encrypt, but purposefully destroys info in the impacted method,” Kaspersky researchers Fedor Sinitsyn and Janis Zinchenko reported in a generate-up.
Added specifics of the attacks were shared by the Russian-language information publication Izvestia. The intrusions have not been attributed to a particular adversarial group so considerably.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

A C++-based malware, CryWiper is configured to build persistence by using a scheduled process and talk with a command-and-command (C2) server to initiate the malicious action.
Aside from terminating procedures linked to database and email servers, the malware is geared up with capabilities to delete shadow copies of information and modify the Windows Registry to reduce RDP connections in a possible endeavor to impede incident reaction efforts.
As the past phase, the wiper corrupts all documents with the exception of those people with “.exe,” “.dll,” “lnk,” “.sys,” and “.msi” extensions, when also skipping unique directories, together with C:Windows, Boot, and tmp, which could or else render the machine inoperable.
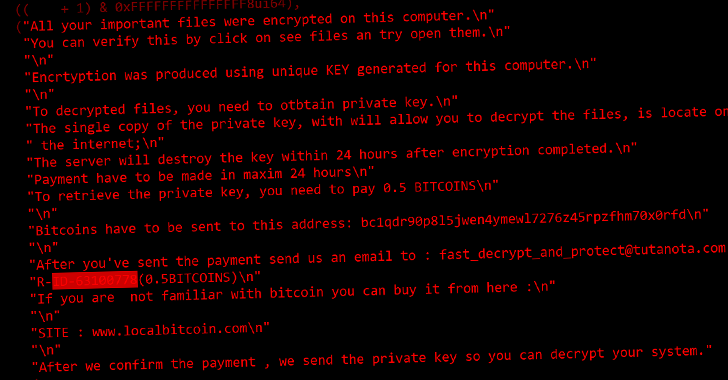
The files overwritten with rubbish info are subsequently appended with an extension called “.CRY,” adhering to which a ransom notice is dropped to give the effect that it can be a ransomware software, urging the sufferer to pay back .5 Bitcoin to get well obtain.
“The activity of CryWiper as soon as yet again exhibits that the payment of the ransom does not promise the recovery of data files,” the scientists reported, stating the malware “intentionally destroys the contents of files.”
CryWiper is the next retaliatory wiper malware pressure aimed at Russia just after RURansom, a .NET-dependent wiper that was uncovered concentrating on entities in the region previously this March.
The ongoing conflict between Russia and Ukraine has concerned the deployment of various wipers, with the latter hit with a wide selection of malware these types of as WhisperGate, HermeticWiper, AcidRain, IsaacWiper, CaddyWiper, Industroyer2, and DoubleZero.
“Wipers can be successful regardless of the technological capabilities of the attacker, as even the simplest wiper can wreak havoc on influenced devices,” Trellix researcher Max Kersten stated in an evaluation of harmful malware previous thirty day period.
“The required time to make these types of a piece of malware is reduced, primarily when in contrast to complex espionage backdoors and the typically-accompanying vulnerabilities that are applied. The return of expenditure require not be large in individuals instances, whilst it is not likely that a couple of wipers are to wreak that much havoc in and of on their own.”
Located this post exciting? Follow us on Twitter and LinkedIn to read far more exclusive content we submit.
Some sections of this short article are sourced from:
thehackernews.com

 When Being Attractive Gets Risky – How Does Your Attack Surface Look to an Attacker?
When Being Attractive Gets Risky – How Does Your Attack Surface Look to an Attacker?