An ongoing espionage campaign operated by the Russia-linked Gamaredon group is concentrating on employees of Ukrainian governing administration, protection, and regulation enforcement companies with a piece of customized-built data stealing malware.
“The adversary is making use of phishing documents made up of lures connected to the Russian invasion of Ukraine,” Cisco Talos researchers Asheer Malhotra and Guilherme Venere explained in a technological generate-up shared with The Hacker News. “LNK data files, PowerShell, and VBScript enable initial accessibility, when destructive binaries are deployed in the write-up-infection section.”
Energetic given that 2013, Gamaredon – also regarded as Actinium, Armageddon, Primitive Bear, Shuckworm, and Trident Ursa – has been joined to quite a few attacks aimed at Ukrainian entities in the aftermath of Russia’s military services invasion of Ukraine in late February 2022.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The focused phishing operation, observed as not too long ago as August 2022, also follows related intrusions uncovered by Symantec previous thirty day period involving the use of malware these types of as Giddome and Pterodo. The principal aim of these attacks is to create very long-term entry for espionage and knowledge theft.
It involves leveraging decoy Microsoft Word documents containing lures connected to the Russian invasion of Ukraine distributed by means of email messages to infect targets. When opened, macros concealed inside remote templates are executed to retrieve RAR made up of LNK data files.
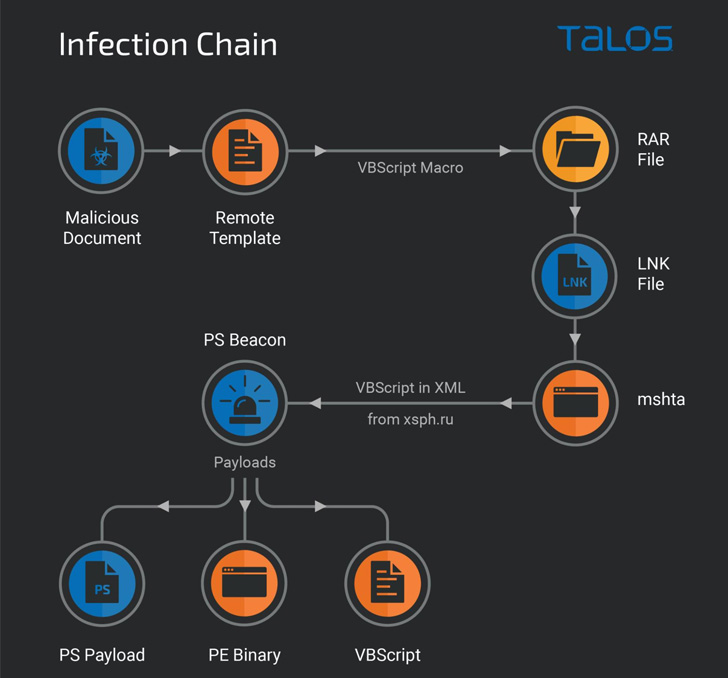
The LNK information seemingly reference intelligence briefings similar to the Russian invasion of Ukraine to trick unsuspecting victims into opening the shortcuts, ensuing in the execution of a PowerShell beacon script that ultimately paves the way for following-phase payloads.
This incorporates another PowerShell script that is made use of to give persistent access to compromised process and deliver extra malware, including a new malware capable of plundering files (.doc, .docx, .xls, .rtf, .odt, .txt, .jpg, .jpeg, .pdf, .ps1, .rar, .zip, .7z, and .mdb) from the device as effectively as any removable travel connected to it.

“The infostealer is a dual-intent malware that features abilities for exfiltrating distinct file varieties and deploying supplemental binary and script-based mostly payloads on an contaminated endpoint,” the researchers reported, introducing it may well be a part of the Giddome backdoor loved ones.
The findings occur at a time cyberattacks keep on to be an vital portion of contemporary hybrid war approach amidst the conflict between Russia and Ukraine. Before this thirty day period, Google’s Menace Investigation Team (TAG) disclosed as numerous as 5 diverse campaigns mounted by a team with backlinks to the Conti cybercrime cartel.
Discovered this post exciting? Follow THN on Facebook, Twitter and LinkedIn to go through a lot more exceptional material we article.
Some elements of this article are sourced from:
thehackernews.com


 5 Ways to Mitigate Your New Insider Threats in the Great Resignation
5 Ways to Mitigate Your New Insider Threats in the Great Resignation