The second technology model of Belkin’s Wemo Mini Intelligent Plug has been identified to consist of a buffer overflow vulnerability that could be weaponized by a danger actor to inject arbitrary instructions remotely.
The issue, assigned the identifier CVE-2023-27217, was found and claimed to Belkin on January 9, 2023, by Israeli IoT security enterprise Sternum, which reverse-engineered the gadget and acquired firmware access.
Wemo Mini Smart Plug V2 (F7C063) presents handy distant regulate, making it possible for end users to convert electronic units on or off making use of a companion app put in on a smartphone or pill.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The coronary heart of the difficulty lies in a aspect that can make it feasible to rename the clever plug to a additional “FriendlyName.” The default title assigned is “Wemo mini 6E9.”
“The name size is restricted to 30 figures or less, but this rule is only enforced by the app alone,” security researchers Amit Serper and Reuven Yakar said in a report shared with The Hacker Information, incorporating the validation was not applied by the firmware code.
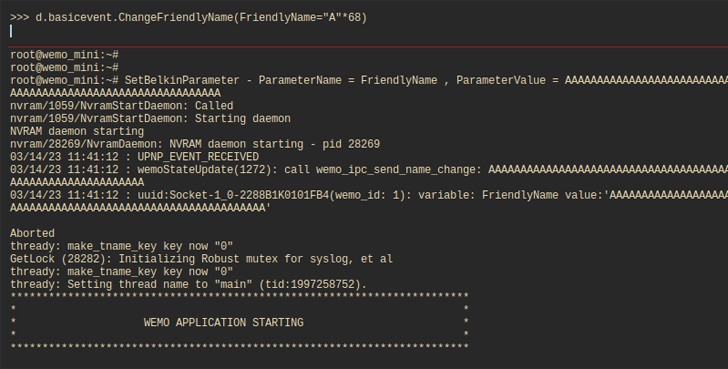
As a result, circumventing the character limit by making use of a Python module named pyWeMo can lead to a buffer overflow condition, which can then be reliably exploited to crash the machine or, alternatively, trick the code into managing destructive instructions and get around command.
Belkin, in response to the conclusions, has claimed that it does not plan to tackle the flaw owing to the truth that the gadget is reaching close-of-lifestyle (EoL) and has been replaced by newer versions.
“It appears that this vulnerability could be activated by means of the Cloud interface (this means, without the need of a direct relationship to the device),” the scientists cautioned.
In the absence of a resolve, people of Wemo Mini Good Plug V2 are suggested to keep away from exposing them directly to the internet and assure that correct segmentation actions are executed if they have been deployed in sensitive networks.
“This is what takes place when devices are delivered devoid of any on-gadget safety. If you only rely on responsive security patching, as most system brands do now, two items are certain: you will usually be a single action behind the attacker, and just one day the patches will end coming,” reported Igal Zeifman, vice president of advertising and marketing for Sternum.
Discovered this report appealing? Stick to us on Twitter and LinkedIn to examine more special articles we article.
Some parts of this write-up are sourced from:
thehackernews.com

 Cyber-Resilience Programs Failing on Poor Visibility
Cyber-Resilience Programs Failing on Poor Visibility