A amount of phishing strategies are leveraging the decentralized Interplanetary Filesystem (IPFS) network to host malware, phishing package infrastructure, and facilitate other attacks.
“Numerous malware households are presently getting hosted in IPFS and retrieved throughout the initial phases of malware attacks,” Cisco Talos researcher Edmund Brumaghin explained in an evaluation shared with The Hacker News.
The investigation mirrors similar results from Trustwave SpiderLabs in July 2022, which discovered a lot more than 3,000 e-mails containing IPFS phishing URLs as an attack vector, calling IPFS the new “hotbed” for hosting phishing sites.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
IPFS as a technology is equally resilient to censorship and takedowns, generating it a double-edged sword. Fundamental it is a peer-to-peer (P2P) network which replicates content material across all participating nodes so that even if information is eliminated from a person device, requests for the methods can still be served by way of other units.
This also can make it ripe for abuse by bad actors searching to host malware that can resist regulation enforcement makes an attempt at disrupting their attack infrastructure, like found in the case of Emotet last calendar year.
“IPFS is presently becoming abused by a range of menace actors who are utilizing it to host malicious contents as element of phishing and malware distribution campaigns,” Brumaghin earlier informed The Hacker Information in August 2022.
This consists of Dark Utilities, a command-and-management (C2) framework which is advertised as a way for adversaries to avail distant system entry, DDoS capabilities, and cryptocurrency mining, with the payload binaries supplied by the platform hosted in IPFS.
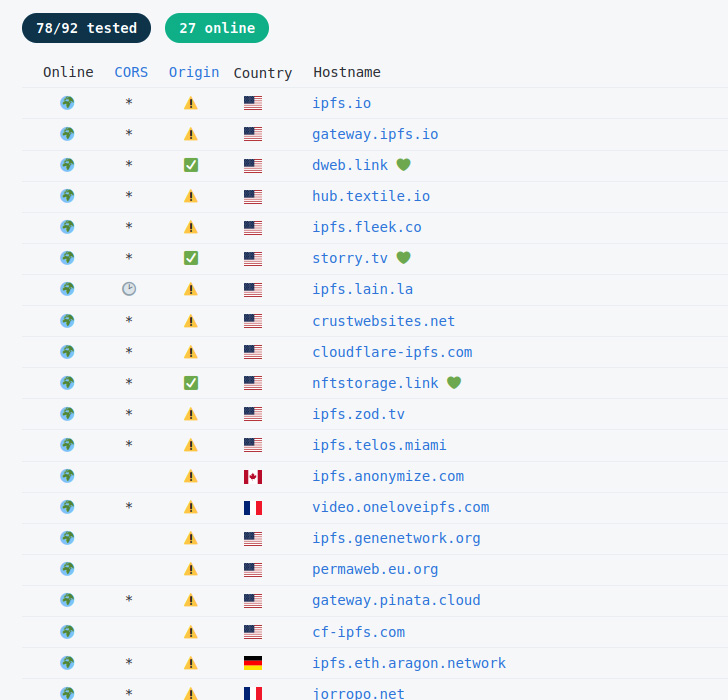
Moreover, IPFS has been put to use to serve rogue landing pages as section of phishing campaigns orchestrated to steal credentials and distribute a vast vary of malware comprising Agent Tesla, reverse shells, info wiper, and an details stealer referred to as Hannabi Grabber.
In a person malspam supply chain in depth by Talos, an email purporting to be from a Turkish money establishment urged the receiver to open up a ZIP file attachment that, when launched, labored as a downloader to retrieve an obfuscated model of Agent Tesla hosted in the IPFS network.

The destructive malware, for its part, normally takes the type of a batch file that deletes backups and recursively purges all directory contents. Hannabi Grabber is a Python-dependent malware that gathers sensitive data from the infected host, these as browser info and screenshots, and transmits it via a Discord Webhook.
The latest growth details to the escalating use by attackers of genuine choices this sort of as Discord, Slack, Telegram, Dropbox, Google Generate, AWS, and numerous other people to host malicious content or to direct people to it, generating phishing a person of the profitable key original entry vectors.
“We assume this action to go on to raise as much more danger actors understand that IPFS can be employed to facilitate bulletproof hosting, is resilient against written content moderation and regulation enforcement activities, and introduces difficulties for businesses making an attempt to detect and defend in opposition to attacks that may leverage the IPFS network,” Brumaghin reported.
Located this report fascinating? Observe THN on Facebook, Twitter and LinkedIn to read more unique articles we submit.
Some parts of this report are sourced from:
thehackernews.com

 Advanced RAT AgentTesla Most Prolific Malware in October
Advanced RAT AgentTesla Most Prolific Malware in October