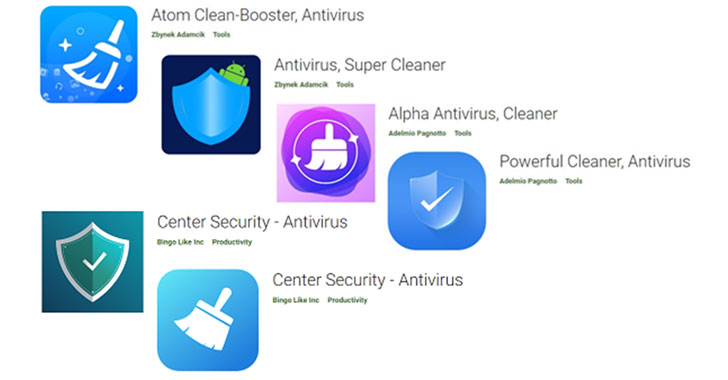
As a lot of as seven malicious Android apps learned on the Google Enjoy Retail outlet masqueraded as antivirus alternatives to deploy a banking trojan identified as SharkBot.
“SharkBot steals credentials and banking information,” Check out Issue researchers Alex Shamshur and Raman Ladutska mentioned in a report shared with The Hacker News. “This malware implements a geofencing element and evasion approaches, which will make it stand out from the rest of malwares.”


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Particularly, the malware is developed to dismiss buyers from China, India, Romania, Russia, Ukraine, and Belarus. The rogue applications are mentioned to have been mounted far more than 15,000 instances prior to their removing, with most of the victims positioned in Italy and the U.K.
The report enhances preceding findings from NCC Group, which located the bankbot posing as antivirus apps to carry out unauthorized transactions by using Automated Transfer Systems (ATS).

SharkBot can take benefit of the Accessibility Expert services permissions to existing phony overlay windows on major of genuine banking applications. Thus when unsuspecting buyers enter their usernames and passwords in the windows that mimic benign credential input forms, the captured knowledge is sent to a malicious server.
A single new noteworthy feature of SharkBot is its means to automobile reply to notifications from Fb Messenger and WhatsApp to distribute a phishing backlink to the antivirus app, thus propagating the malware in a worm-like vogue. A similar aspect was incorporated in FluBot earlier this February.
The most current conclusions come as Google took steps to banish 11 apps from the Play Keep on March 25 immediately after they had been caught incorporating an invasive SDK to discreetly harvest user data, such as exact area information, email and phone quantities, close by units, and passwords.
“What is actually also noteworthy right here is that the danger actors drive messages to victims made up of malicious backlinks, which potential customers to popular adoption,” Alexander Chailytko, cyber security, study and innovation manager at Check out Place Program, mentioned.
“All in all, the use of press-messages by the threat actors requesting an answer from consumers is an strange spreading method.”
Uncovered this posting exciting? Abide by THN on Fb, Twitter and LinkedIn to go through more distinctive content we post.
Some areas of this article are sourced from:
thehackernews.com


 Google will cull out-of-date Play store apps in bid to improve Android security
Google will cull out-of-date Play store apps in bid to improve Android security