SideWinder, a prolific nation-state actor mainly acknowledged for concentrating on Pakistan armed forces entities, compromised the formal website of the Countrywide Electric Energy Regulatory Authority (NEPRA) to provide a customized malware called WarHawk.
“The newly found out WarHawk backdoor has various destructive modules that deliver Cobalt Strike, incorporating new TTPs this kind of as KernelCallBackTable injection and Pakistan Regular Time zone look at in order to make certain a victorious marketing campaign,” Zscaler ThreatLabz said.
The threat team, also termed APT-C-17, Rattlesnake, and Razor Tiger, is suspected to be an Indian point out-sponsored group, even though a report from Kaspersky previously this May perhaps acknowledged prior indicators that led to the attribution have since disappeared, generating it challenging it to backlink the danger cluster to a distinct country.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Much more than 1,000 attacks are explained to have been released by the team given that April 2020, an indicator of SideWinder’s newfound aggression because it commenced functions a ten years ago in 2012.
The intrusions have been major not only with regard to their frequency but also in their persistence, even as the team usually takes edge of a substantial arsenal of obfuscated and recently-formulated parts.
In June 2022, the danger actor was uncovered leveraging an AntiBot script that is made to filter their victims to examine the client browser environment, especially the IP deal with, to assure the targets are positioned in Pakistan.
The September marketing campaign spotted by Zscaler involves the use of a weaponized ISO file hosted on NEPRA’s internet site to activate a killchain that prospects to the deployment of the WarHawk malware, with the artifact also acting as a decoy to hide the malicious activity by exhibiting a authentic advisory issued by the Cabinet Division of Pakistan on July 27, 2022.
WarHawk, for its part, masquerades as authentic applications such as ASUS Update Set up and Realtek Hd Audio Manager to entice unsuspecting victims into execution, resulting the exfiltration of system metadata to a tough-coded remote server, though also acquiring further payloads from the URL.
This contains a command execution module that’s liable for the execution of procedure instructions on the contaminated machine acquired from the command-and-handle server, a file manager module that recursively enumerates information present in various drives, and an upload module that transmits documents of fascination to the server.

Also deployed as a next-stage payload employing the aforementioned command execution module is a Cobalt Strike Loader, which validates the host’s time zone to confirm it matches the Pakistan Common Time (PKT), failing which the approach is terminated.
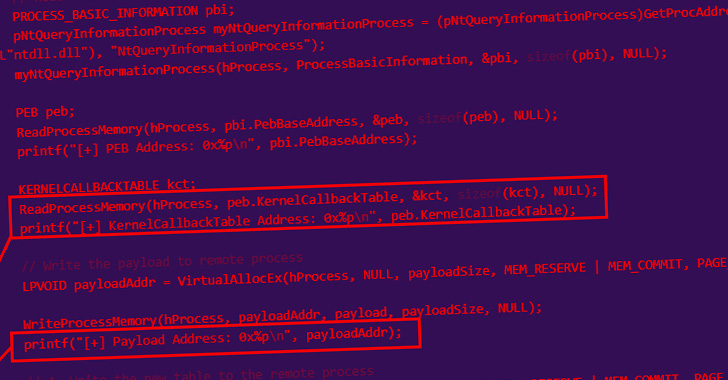
Pursuing the anti-anThe loader injects shellcode into a notepad.exe course of action utilizing a system identified as KernelCallbackTable system injection, with the malware author lifting resource code from a technological compose-up published in April 2022 by a researcher who goes by the on the internet alias Capt. Meelo.
The shellcode then decrypts and hundreds Beacon, the default malware payload made use of by Cobalt Strike to build a connection to its command-and-control server.
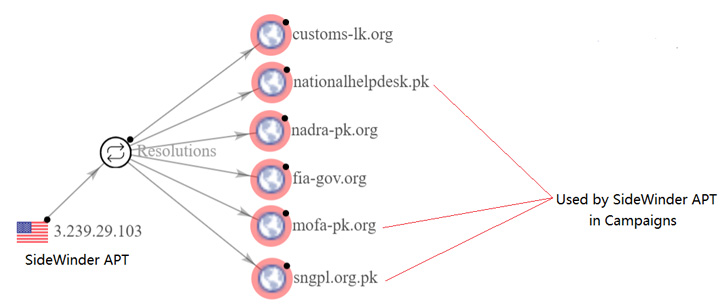
Per the cybersecurity company, the attack campaign’s connections to the SideWinder APT stem from the reuse of network infrastructure that has been recognized as employed by the group in prior espionage-centered functions versus Pakistan.
“The SideWinder APT Team is continually evolving their techniques and introducing new malware to their arsenal in buy to have out effective espionage attack campaigns in opposition to their targets,” the scientists concluded.
Located this article appealing? Adhere to THN on Facebook, Twitter and LinkedIn to examine a lot more exceptional material we publish.
Some parts of this article are sourced from:
thehackernews.com

 CISA Warns of Daixin Team Hackers Targeting Health Organizations With Ransomware
CISA Warns of Daixin Team Hackers Targeting Health Organizations With Ransomware