The risk actor regarded as SideWinder has additional a new customized resource to its arsenal of malware that is currently being made use of in phishing attacks towards Pakistani general public and private sector entities.
“Phishing inbound links in email messages or posts that mimic reputable notifications and solutions of authorities companies and companies in Pakistan are main attack vectors of the gang,” Singapore-headquartered cybersecurity business Group-IB claimed in a Wednesday report.
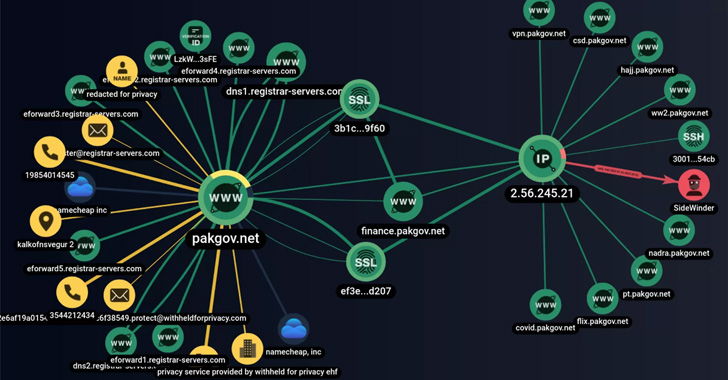
SideWinder, also tracked below the monikers Hardcore Nationalist, Rattlesnake, Razor Tiger, and T-APT-04, has been energetic considering that at least 2012 with a main concentration on Pakistan and other Central Asian nations around the world like Afghanistan, Bangladesh, Nepal, Singapore, and Sri Lanka.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Past thirty day period, Kaspersky attributed to this group about 1,000 cyber attacks that took position in the earlier two many years, while calling out its persistence and advanced obfuscation strategies.
The threat actor’s modus operandi entails the use of spear-phishing email messages to distribute malicious ZIP archives made up of RTF or LNK data files, which download an HTML Application (HTA) payload from a remote server.
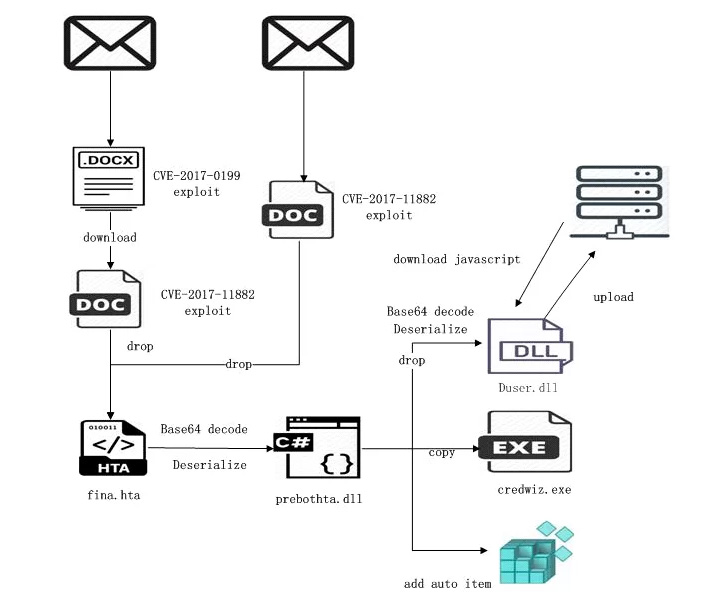
This is achieved by embedding fraudulent inbound links that are created to mimic genuine notifications and products and services of federal government businesses and companies in Pakistan, with the team also placing up lookalike sites posing as governing administration web sites to harvest person qualifications.
The customized resource determined by Group-IB, dubbed SideWinder.AntiBot.Script, acts as a site visitors route procedure diverting Pakistani customers clicking on the phishing one-way links to rogue domains.
Ought to a consumer whose client’s IP address differs from Pakistan’s tap on the hyperlink, the AntiBot script redirects to an reliable doc positioned on a reputable server, indicating an try to geofence its targets.

“The script checks the client browser setting and, dependent on a number of parameters, decides regardless of whether to issue a malicious file or redirect to a legitimate useful resource,” the researchers stated.
Of particular point out is a phishing link that downloads a VPN software called Secure VPN (“com.securedata.vpn”) from the official Google Engage in shop in an try to impersonate the genuine Protected VPN application (“com.securevpn.securevpn”).
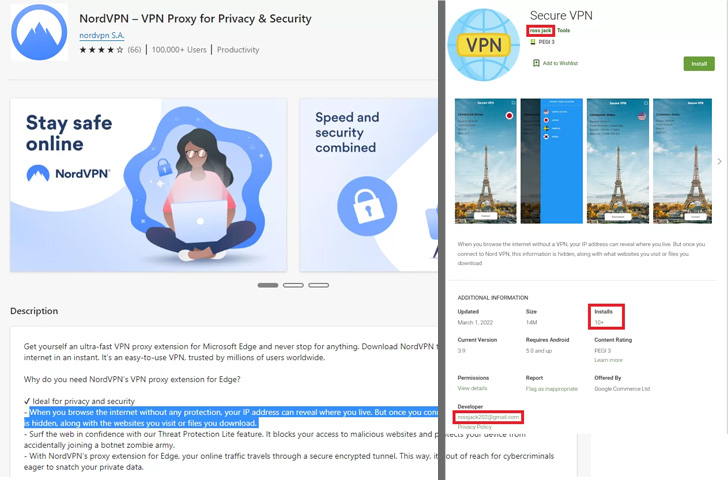
When the specific intent of the pretend VPN application remains unclear, this is not the initially time SideWinder has sneaked past Google Enjoy Shop protections to publish rogue applications beneath the pretext of utility software.
In January 2020, Craze Micro in depth 3 destructive apps that ended up disguised as photography and file manager applications that leveraged a security flaw in Android (CVE-2019-2215) to obtain root privileges as nicely as abuse accessibility service permissions to harvest sensitive details.
Uncovered this write-up interesting? Follow THN on Facebook, Twitter and LinkedIn to browse extra exclusive content we post.
Some parts of this posting are sourced from:
thehackernews.com

 DOJ Seizes 3 Web Domains Used to Sell Stolen Data and DDoS Services
DOJ Seizes 3 Web Domains Used to Sell Stolen Data and DDoS Services