Let us facial area it: we all use email, and we all use passwords. Passwords generate inherent vulnerability in the technique. The good results level of phishing attacks is skyrocketing, and possibilities for the attack have tremendously multiplied as lives moved on-line. All it usually takes is a person password to be compromised for all other end users to grow to be victims of a knowledge breach.
To deliver supplemental security, consequently, electronic identities depend on verification plasters. MFA (multi-factor authentication) frequently falls back again to information aspects these kinds of as password resets and OTP codes, but these are continue to vulnerable. As very long as credentials can be shared or intercepted, they can be misused.
What is essential is a paradigm shift – from understanding-based credentials to strong possession-factor security that can’t be compromised, together with other verification security this kind of as biometrics.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
A new possession-factor API now aims to do precisely that, changing knowledge-based credentials, by applying the SIM card for possession factor gadget binding and consumer authentication, hence decreasing the probability of phishing.
Phishing: a human dilemma
Phishing and other sorts of social engineering count on the human factor to be the weakest backlink in a breach. They make use of the effortless, credential-primarily based accessibility afforded to the normal person of a platform, by tricking individuals normal people into sharing qualifications. And it operates: 83% of businesses surveyed reported they professional a thriving email-dependent phishing attack in 2021.
Even 2FA codes are now targets
It truly is typical knowledge that passwords can be shared and, thus, effortlessly phished. But a lesser-identified actuality is that numerous forms of 2FA – such as the OTP or PIN code added in an exertion to strengthen the recognised weaknesses in passwords – are also phishable.
Even worse, criminals are now concentrating on these techniques especially: researchers recently located that in excess of 1,200 phishing kits built to steal 2FA codes are out in operation.
The reply to id and entry management, for that reason, is not to utilize more patches that destroy the user experience, as these don’t really hold attackers out. In its place, MFA demands a stronger, less complicated possession factor – with almost nothing to sort, this means practically nothing to phish.
Reason-designed MFA possession things include things like security dongles or tokens. But they are highly-priced, and not something the regular consumer will purchase. Much better security for every person can only do the job with gadgets that are commonly available, straightforward to use, uncomplicated to combine, and price-efficient.
Enter the SIM card. It is really inside everyone’s mobile phone, and is developed on cryptographic security when connecting to mobile network authentication.
Now, for the very first time, an API from tru.ID opens up SIM-centered cell network authentication to just about every company and app developer, which means you can leverage the security of the SIM card as a protected possession factor for MFA.
SIM-primarily based authentication: the new phishing-resistant possession factor
The SIM card has a large amount going for it. SIM cards use the identical highly secure, cryptographic microchip technology that is developed into every single credit rating card. It is tricky to clone or tamper with, and there is a SIM card in just about every cell phone – so each a single of your customers currently has this components in their pocket.
The mix of the mobile phone variety with its related SIM card id (the IMSI) is a combination which is hard to phish as it is really a silent authentication verify.
The consumer knowledge is excellent much too. Cellular networks routinely perform silent checks that a user’s SIM card matches their phone selection in buy to let them deliver messages, make calls, and use details – making sure genuine-time authentication without the need of demanding a login.
Right up until recently, it wasn’t probable for firms to system the authentication infrastructure of a cell network into an app as very easily as any other code. tru.ID helps make network authentication available to absolutely everyone.
Adding the tru.ID SDK into current account journeys that use the cellular phone variety right away permits possession-factor security for every single consumer. What’s more, with no extra input from the person, you will find no attack vector for malicious actors: SIM-dependent authentication is invisible, so there is certainly no credentials or codes to steal, intercept or misuse.
tru.ID does not accessibility the user’s SIM card. Rather, it verifies SIM card position right with the mobile operator in true-time. It checks that a phone quantity has not been assigned to an additional SIM and for current SIM alterations, assisting to reduce SIM swap fraud.
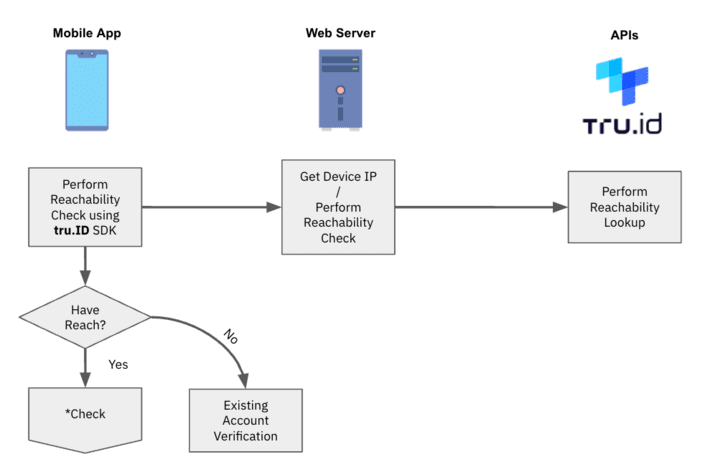
An case in point scenario to enable SIM-centered verification
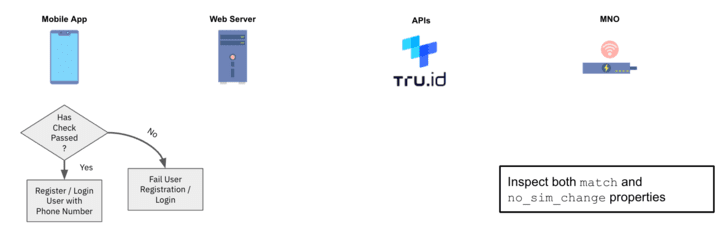
Even while there are a amount of procedures described in the state of affairs under, the end user of the technique has to do only a single detail – deliver their mobile phone variety.
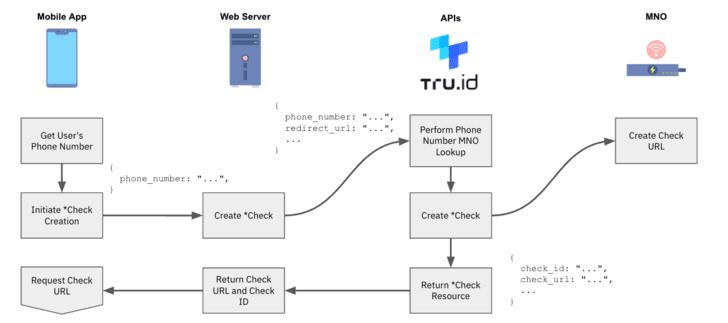
1 — Following the user gives their cellular amount, the tru.ID API performs a lookup for the phone number to identify which cell network operator (MNO) it is assigned to.
2 — tru.ID requests from the MNO a exclusive Test URL to begin the mobile authentication workflow.
3 — tru.ID shops the MNO’s Look at URL, and returns a tru.ID Check out URL to your web server for the mobile unit to open.
4 — The cellular application opens the tru.ID Test URL. It is chosen to use tru.ID SDKs for this because it forces the web request to be in excess of a mobile data session.
5 — The MNO will get the web ask for via a redirect from the tru.ID system.
6 — The last redirect normally takes the device to the web server’s redirect url endpoint. The body of this ask for will incorporate a ‘code’ and the ‘check_id’, and the web server submits this code to tru. ID’s API to finish the SubscriberCheck course of action.
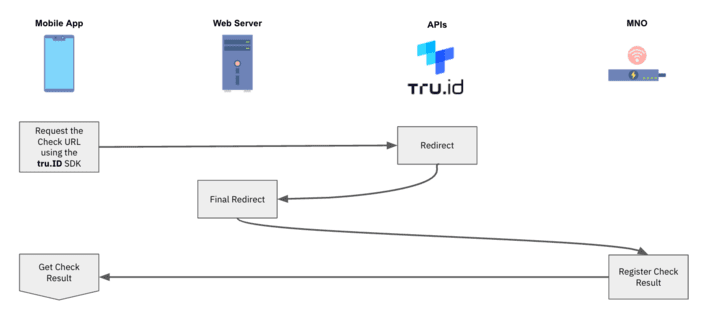
7 — The MNO then decides if the phone number involved with the authenticated mobile data session matches the phone amount affiliated with the asked for Verify URL. If it does, then the phone amount has been effectively confirmed.
8 — tru.ID performs a SIM card glimpse up and retailers the final result of its standing.
9 — On completion of the Look at URL ask for, and when the SIM card status has been retrieved, the cellular application can request the end result of the phone verification from the tru.ID API.
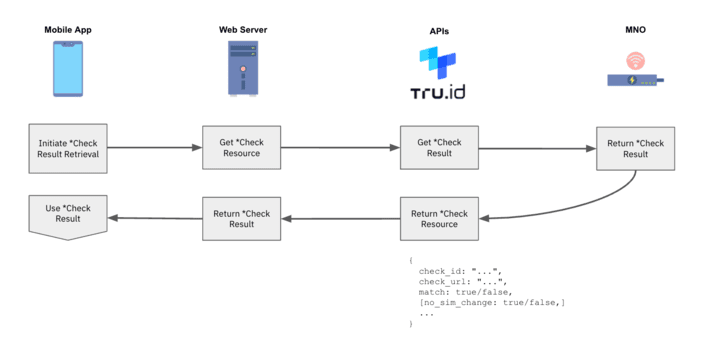
10 — Use the phone verification match and SIM card improve `no_sim_change` homes inside of your software logic.
How to get started out
With tru. ID’s developer system, you can start tests SIM-based authentication appropriate absent, for free, and make your first API simply call inside of minutes.
To find out how up coming-gen authentication can produce large security, minimal friction authentication experiences to your end users, basically ebook a no cost demo or check out tru.ID.
Discovered this write-up appealing? Adhere to THN on Facebook, Twitter and LinkedIn to go through additional unique content material we publish.
Some sections of this write-up are sourced from:
thehackernews.com


 New Chaos Ransomware Builder Variant “Yashma” Discovered in the Wild
New Chaos Ransomware Builder Variant “Yashma” Discovered in the Wild