A new malware able of managing social media accounts is being dispersed by Microsoft’s official application shop in the type of trojanized gaming apps, infecting additional than 5,000 Windows equipment in Sweden, Bulgaria, Russia, Bermuda, and Spain.
Israeli cybersecurity firm Examine Place dubbed the malware “Electron Bot,” in reference to a command-and-management (C2) domain made use of in current campaigns. The id of the attackers is not known, but evidence indicates that they could be dependent out of Bulgaria.
“Electron Bot is a modular Search engine marketing poisoning malware, which is utilised for social media advertising and simply click fraud,” Check out Point’s Moshe Marelus explained in a report published this week. “It is largely dispersed by means of the Microsoft store platform and dropped from dozens of contaminated programs, largely game titles, which are continually uploaded by the attackers.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The very first indicator of destructive exercise commenced as an advert clicker marketing campaign that was found out in October 2018, with the malware hiding in plain sight in the form of a Google Photos app, as disclosed by Bleeping Pc.
In the many years considering that, the malware is said to have gone through various iterations that equip the malware with new attributes and evasive abilities. In addition to working with the cross-platform Electron framework, the bot is made to load payloads fetched from the C2 server at operate time, making it hard to detect.
“This allows the attackers to modify the malware’s payload and change the bots’ habits at any offered time,” Marelus stated.
Electron Bot’s core functionality is to open up a hidden browser window in purchase to carry out Search engine optimisation poisoning, deliver clicks for ads, direct site visitors to material hosted on YouTube and SoundCloud, and boost unique goods to deliver gains with ad clicking or maximize store score for higher product sales.
On top of that, it also comes with features that can handle social media accounts on Fb, Google and Sound Cloud, like registering new accounts, signing in, as very well as commenting and liking other posts to maximize sights.
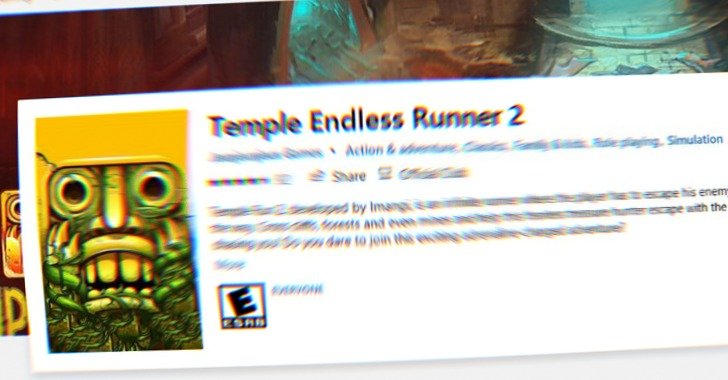
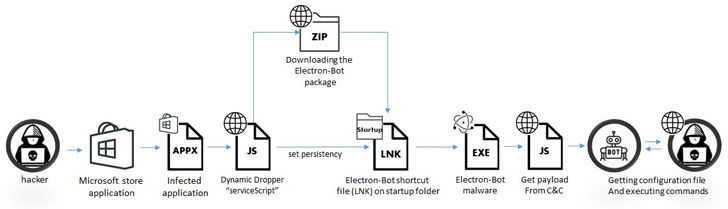
The attack sequence receives induced when users download just one of the infected apps (e.g., Temple Countless Runner 2) from the Microsoft retailer that, when released, masses the recreation but also stealthily drops and installs the future phase dropper by means of JavaScript.
Alongside the way, there are ways to detect prospective risk detection software program from corporations this kind of as Kaspersky Lab, ESET, Norton Security, Webroot, Sophos, and F-Secure just before the dropper proceeds to fetch the true bot malware.
The list of activity publishers that pushed the malware-laced applications is as follows –
- Lupy games
- Ridiculous 4 games
- Jeuxjeuxkeux online games
- Akshi video games
- Goo Game titles
- Bizzon Situation
“As the bot’s payload is loaded dynamically at every run time, the attackers can modify the code and change the bot’s conduct to large risk,” Marelus mentioned. “For example, they can initialize another next stage and drop a new malware this kind of as ransomware or a RAT. All of this can take place without having the victim’s know-how.”
Observed this write-up interesting? Adhere to THN on Facebook, Twitter and LinkedIn to read through far more exclusive information we post.
Some sections of this report are sourced from:
thehackernews.com


 Russia-Ukraine War: Phishing, Malware and Hacker Groups Taking Sides
Russia-Ukraine War: Phishing, Malware and Hacker Groups Taking Sides