In a sign that danger actors constantly shift ways and update their defensive measures, the operators of the SolarMarker facts stealer and backdoor have been located leveraging stealthy tricks to set up extended-expression persistence on compromised techniques.
Cybersecurity organization Sophos, which spotted the new conduct, explained that the remote accessibility implants are even now being detected on targeted networks even with the marketing campaign witnessing a decrease in November 2021.
Boasting of details harvesting and backdoor abilities, the .NET-based malware has been connected to at minimum three distinct attack waves in 2021. The 1st established, claimed in April, took advantage of search engine poisoning methods to trick business gurus into visiting sketchy Google web-sites that installed SolarMarker on the victim’s equipment.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Then in August, the malware was noticed concentrating on health care and education and learning sectors with the goal of accumulating credentials and delicate facts. Subsequent infection chains documented by Morphisec in September 2021 highlighted the use of MSI installers to be certain the supply of the malware.
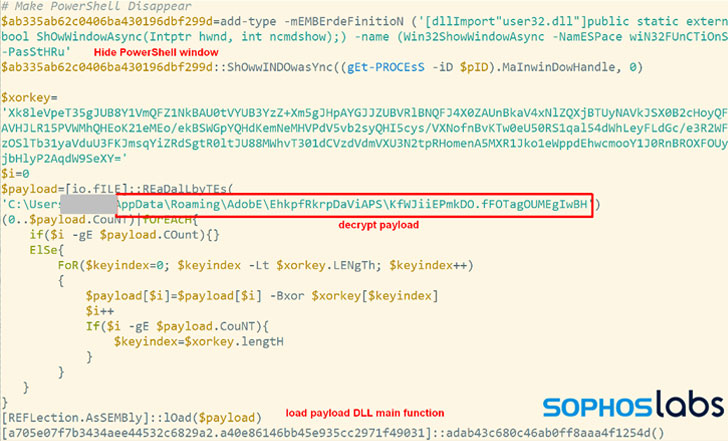
The SolarMarker modus operandi commences with redirecting victims to decoy websites that fall the MSI installer payloads, which, even though executing seemingly legit set up courses such as Adobe Acrobat Pro DC, Wondershare PDFelement or Nitro Pro, also launches a PowerShell script to deploy the malware.
“These Search engine optimisation efforts, which leveraged a combination of Google Teams discussions and deceptive web web pages and PDF files hosted on compromised (usually WordPress) web sites, were so productive that the SolarMarker lures had been ordinarily at or around the best of research final results for phrases the SolarMarker actors targeted,” Sophos researchers Gabor Szappanos and Sean Gallagher explained in a report shared with The Hacker News.
The PowerShell installer is intended to alter the Windows Registry and fall a .LNK file into Windows’ startup directory to set up persistence. This unauthorized modify outcomes in the malware receiving loaded from an encrypted payload hidden amongst what the researchers identified as a “smokescreen” of 100 to 300 junk data files made especially for this objective.
“Typically, one particular would expect this joined file to be an executable or script file,” the scientists comprehensive. “But for these SolarMarker strategies the linked file is a single of the random junk data files, and can not be executed itself.
What is actually extra, the one of a kind and random file extension utilised for the connected junk file is used to make a personalized file variety essential, which is ultimately used to execute the malware throughout method startup by jogging a PowerShell command from the Registry.
The backdoor, for its element, is at any time-evolving, featuring an array of functionalities that permit it to steal details from web browsers, aid cryptocurrency theft, and execute arbitrary commands and binaries, the benefits of which are exfiltrated again to a distant server.
“Yet another vital takeaway […], which was also seen in the ProxyLogon vulnerabilities targeting Trade servers, is that defenders must always examine no matter whether attackers have left one thing at the rear of in the network that they can return to later,” Gallagher claimed. “For ProxyLogon this was web shells, for SolarMarker this is a stealthy and persistent backdoor that according to Sophos telematics is nonetheless active months right after the marketing campaign finished.”
Located this short article intriguing? Comply with THN on Fb, Twitter and LinkedIn to read a lot more exceptional written content we put up.
Some components of this write-up are sourced from:
thehackernews.com



 QNAP ransomware victims dealt double blow as firmware update hampers decryption
QNAP ransomware victims dealt double blow as firmware update hampers decryption