Luxury resorts in the Chinese exclusive administrative location of Macau ended up the target of a destructive spear-phishing marketing campaign from the 2nd fifty percent of November 2021 and via mid-January 2022.
Cybersecurity company Trellix attributed the marketing campaign with average self-confidence to a suspected South Korean state-of-the-art persistent danger (APT) tracked as DarkHotel, setting up on investigate previously posted by Zscaler in December 2021.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Believed to be energetic since 2007, DarkHotel has a background of striking “senior organization executives by uploading destructive code to their pcs through infiltrated lodge Wi-Fi networks, as effectively as as a result of spear-phishing and P2P attacks,” Zscaler scientists Sahil Antil and Sudeep Singh stated. Outstanding sectors targeted contain law enforcement, prescription drugs, and automotive brands.

The attack chains included distributing email messages directed to men and women in executive roles in the hotel, this sort of as the vice president of human means, assistant supervisor, and entrance office supervisor, indicating that the intrusions have been aimed at team who were in possession of access to the hotel’s network.
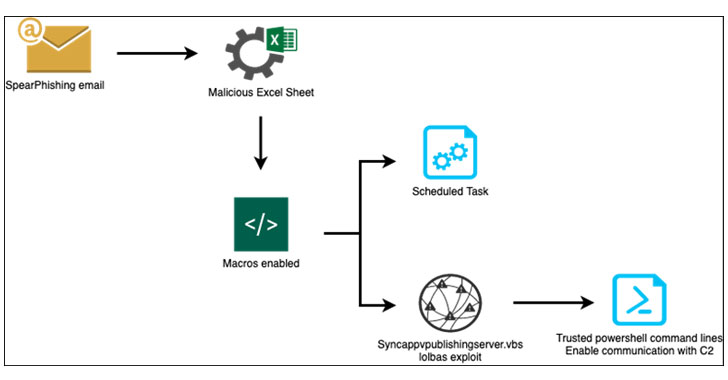
In 1 phishing entice despatched to 17 distinctive accommodations on December 7, the email purported to be from the Macau Federal government Tourism Workplace and urged the victims to open up an Excel file named “信息.xls” (“information.xls”). In a further case, the email messages have been faked to obtain information about people today keeping in the resorts.
The malware-laced Microsoft Excel file, when opened, tricked the recipients into enabling macros, triggering an exploit chain to gather and exfiltrate sensitive details from the compromised machines back again to a remote command-and-command (C2) server (“fsm-gov[.]com”) that impersonated the federal government web site for the Federated States of Micronesia (FSM).
“This IP was applied by the actor to drop new payloads as 1st levels to set up the target setting for program details exfiltration and possible future methods,” Trellix researchers Thibault Seret and John Fokker said in a report released very last 7 days. “All those payloads had been applied to goal key hotel chains in Macau, like the Grand Coloane Vacation resort and Wynn Palace.”
Also noteworthy is the actuality that the C2 server IP deal with has continued to stay active in spite of prior public disclosure and that it can be also becoming used to serve phishing web pages for an unrelated credential harvesting attack directed at MetaMask cryptocurrency wallet consumers.
The campaign is reported to have to fulfilled its inescapable conclusion on January 18, 2022 coinciding with the increase of COVID-19 instances in Macau, prompting the cancelation or postponement of global trade conferences that had been established to consider put in the targeted lodges.
“The group was making an attempt to lay the foundation for a potential campaign involving these distinct inns,” the researchers stated. “In this campaign, the COVID-19 constraints threw a wrench in the threat actor’s engine, but that isn’t going to mean they have abandoned this approach.”
Located this posting intriguing? Follow THN on Fb, Twitter and LinkedIn to study a lot more special content we article.
Some pieces of this posting are sourced from:
thehackernews.com




 Ugandan Writers Charged with Cyber Stalking President
Ugandan Writers Charged with Cyber Stalking President