A suspected state-aligned menace actor has been attributed to a new established of attacks exploiting the Microsoft Office “Follina” vulnerability to concentrate on federal government entities in Europe and the U.S.
Business security organization Proofpoint reported it blocked makes an attempt at exploiting the distant code execution flaw, which is remaining tracked CVE-2022-30190 (CVSS score: 7.8). No significantly less than 1,000 phishing messages made up of a lure doc had been despatched to the targets.
“This campaign masqueraded as a salary improve and used an RTF with the exploit payload downloaded from 45.76.53[.]253,” the company mentioned in a series of tweets.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The payload, which manifests in the form of a PowerShell script, is Base64-encoded and functions as a downloader to retrieve a second PowerShell script from a distant server named “vendor-notification[.]dwell.”
“This script checks for virtualization, steals facts from local browsers, mail clientele and file providers, conducts device recon and then zips it for exfil[tration] to 45.77.156[.]179,” the company additional.
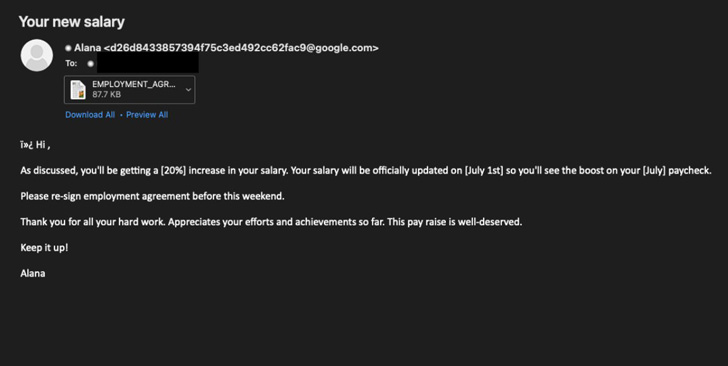
The phishing campaign has not been linked to a previously recognised team, but mentioned it was mounted by a country-state actor based mostly on the specificity of the concentrating on and the PowerShell payload’s extensive-ranging reconnaissance abilities.
The growth follows active exploitation tries by a Chinese danger actor tracked as TA413 to produce weaponized ZIP archives with malware-rigged Microsoft Phrase documents.

The Follina vulnerability, which leverages the “ms-msdt:” protocol URI plan to remotely get management of concentrate on units, stays unpatched, with Microsoft urging buyers to disable the protocol to stop the attack vector.
“Proofpoint continues to see specific attacks leveraging CVE-2022-30190,” Sherrod DeGrippo, vice president of threat exploration, explained in a statement shared with The Hacker Information.
“The considerable reconnaissance done by the next PowerShell script demonstrates an actor fascinated in a big variety of software program on a target’s pc. This, coupled with the tight focusing on of European government and neighborhood U.S. governments led us to suspect this marketing campaign has a point out aligned nexus.”
Found this write-up appealing? Comply with THN on Fb, Twitter and LinkedIn to read through more exceptional articles we submit.
Some pieces of this post are sourced from:
thehackernews.com


 Atlassian Releases Patch for Confluence Zero-Day Flaw Exploited in the Wild
Atlassian Releases Patch for Confluence Zero-Day Flaw Exploited in the Wild