An Android banking trojan built to steal qualifications and SMS messages has been observed sneaking earlier Google Perform Keep protections to concentrate on end users of extra than 400 banking and economical applications from Russia, China, and the U.S.
“TeaBot RAT abilities are reached by way of the device screen’s dwell streaming (asked for on-need) in addition the abuse of Accessibility Products and services for distant interaction and key-logging,” Cleafy scientists said in a report. “This enables Threat Actors (TAs) to execute ATO (Account Takeover) straight from the compromised phone, also identified as ‘On-unit fraud.'”


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Also regarded by the identify Anatsa, TeaBot to start with emerged in Could 2021, camouflaging its destructive functions by posing as seemingly innocuous PDF document and QR code scanner apps that are dispersed by means of the formal Google Play Retail outlet in its place of third-party apps outlets or by way of fraudulent websites.
These apps, also recognised as dropper purposes, act as a conduit to deliver a next-phase payload that retrieves the malware pressure to consider manage of the infected units. In November 2021, Dutch security company ThreatFabric disclosed that it experienced discovered six Anatsa droppers on the Engage in Retail store considering the fact that June final year.
Then before this January, Bitdefender scientists identified TeaBot lurking in the official Android application market as a “QR Code Reader – Scanner App,” gaining extra than 100,000 downloads in just a span of a thirty day period before it was taken down.
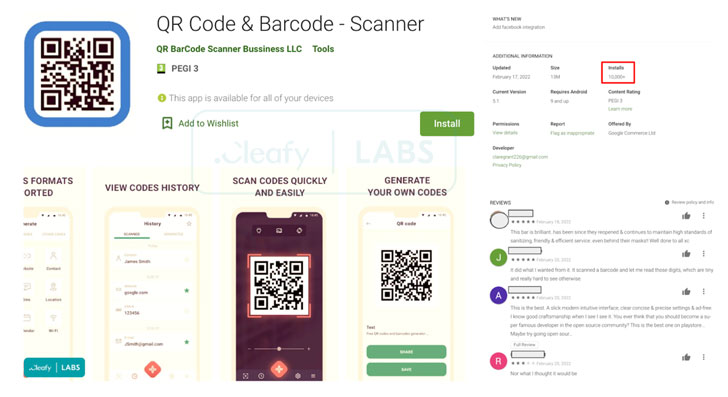
The hottest model of TeaBot dropper spotted by Cleafy on February 21, 2022, is also a QR code reader app named “QR Code & Barcode – Scanner” which has been downloaded around 10,000 occasions from the Play Retail store.
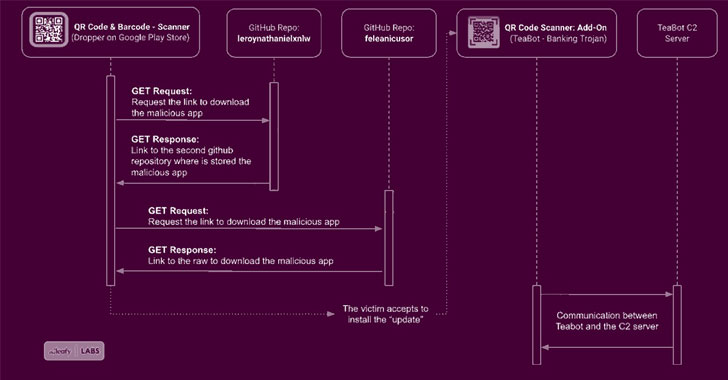
The moment installed the modus operandi is the exact: prompt consumers to settle for a phony incorporate-on update, which, in flip, potential customers to the set up of a second application hosted on GitHub that basically includes the TeaBot malware. It really is, even so, well worth noting that people need to have to make it possible for installs from not known sources for this attack chain to be prosperous.
The very last period of the infection includes the banking trojan searching for Accessibility Providers permissions to seize delicate info like login qualifications and two-factor authentication codes with the intention of getting over the accounts to have out on-unit fraud.
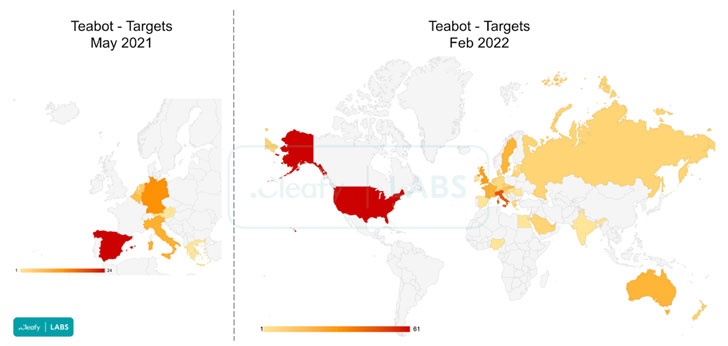
“In considerably less than a yr, the variety of programs specific by TeaBot have grown additional than 500%, going from 60 targets to around 400,” the scientists said, incorporating the malware now strikes many apps connected to personalized banking, insurance coverage, crypto wallets, and crypto exchanges.
Found this short article fascinating? Observe THN on Facebook, Twitter and LinkedIn to go through much more exceptional written content we submit.
Some components of this post are sourced from:
thehackernews.com


 RCE Bugs in Other Hugely Popular VoIP Apps: Patch Now!
RCE Bugs in Other Hugely Popular VoIP Apps: Patch Now!