Being familiar with the connection in between GRC and cybersecurity
When conversing about cybersecurity, Governance, Risk, and Compliance (GRC) is often thought of the least enjoyable part of business protection. On the other hand, its importance can’t be overlooked, and this is why.
Whilst cybersecurity focuses on the technological facet of guarding systems, networks, gadgets, and details, GRC is the resource that will enable the complete business fully grasp and connect how to do it.
What does it necessarily mean?

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
GRC instruments like StandardFusion enable providers define and implement the finest tactics, strategies, and governance to make sure everyone understands the dangers linked with their actions and how they can impact enterprise security, compliance, and achievement.
In straightforward text, GRC is the medium for creating consciousness close to cybersecurity’s greatest methods to reduce challenges and attain business aims.
Why is cybersecurity additional applicable than ever right before
Cybersecurity aims to safeguard sensitive company information, intellectual property, personalized and overall health info, and other enterprise methods from cyber-attacks and threats. However, this undertaking has turn out to be significantly more durable above the earlier few many years.
Why is that?
Nicely, since of the at any time-increasing world connectivity, new hybrid function products, the popularization of cloud providers, and the evolution of technology, among the other people. Although all of these are fantastic from a organization viewpoint, they introduce new hazards and difficulties.
This is the real truth:
Cybersecurity has constantly been a critical part of companies having said that, in present-day technological and interconnected landscape, they can not exist with no it, at minimum in the prolonged expression.

Comprehension the principles of GRC
Governance, Risk, and Compliance (GRC) is a organization technique for managing a company’s general governance, business risk management, and regulatory compliance.
From a cybersecurity standpoint, GRC is a structured strategy to aligning IT (folks and functions) with business enterprise objectives even though properly taking care of threats and meeting regulatory requires.
In this context, to attain business targets and optimize the company’s bottom line, businesses need to comply with the most effective tactics and strategies. This is why GRC exists… to mitigate any menace to productiveness and the firm’s price by developing specifications, guidelines, laws, and processes.
Far more importantly, GRC aids construct have confidence in in the group. This have confidence in comes from enhanced efficiencies, improved conversation, employees’ self confidence to share facts, and increased small business results.
That’s not all.
GRC empowers corporations to produce a lifestyle of worth, giving all people the instruction and company to recognize how they can secure the business’s benefit, name and make much better selections.
The important job of GRC in cybersecurity
Corporations should align persons, programs, and systems with small business aims to realize sound and efficient cybersecurity. This indicates anyone must know and get the proper actions when executing their duties — it really is all about recognition and know-how.
Governance, Risk, and Compliance is the very best device to build an built-in procedure that focuses on attaining objectives even though addressing dangers and acting with integrity.
GRC is essential simply because it supports cybersecurity with vital organization routines, these kinds of as:
- Standardizing the most effective practices for absolutely everyone to act with integrity and security.
- Assigns roles and duties to business enterprise models and people, enhancing interaction.
- Assisting with the implementation of facts manipulation techniques.
- Unifies vocabulary across departments and groups.
- Supporting inside audits and encourages ongoing command checking.
- Aiding with risk mitigation internally and externally
- Supporting conference sector and federal government rules.
GRC also supplies a framework to combine security and privacy with the organization’s overall targets. Why is this significant? For the reason that it permits firms to make knowledgeable selections pertaining to data security threats immediately even though mitigating the risk of compromising privacy.
The part of GRC in cybersecurity – technical advantages
The pursuing are some of the important positive aspects GRC features cybersecurity:
3rd-party vendor variety: A lot of organizations will use a third-party scorecard to acquire simple facts about opportunity distributors. This information and facts incorporates: Corporate name, financials, network security, history of cyber breaches, geographic spot, and more. A strong GRC product would help IT and security teams choose and vet likely third-party distributors. More importantly, GRC will aid the development of vendor assessments and mitigation tactics.
Risk mitigation: IT can use GRC to have an understanding of the scope of cybersecurity and doc the strengths and constraints of the present security application. GRC permits organizations to define and act on distinct types of threats, possible damages, mitigation plans, and risk remedies.
Regulatory compliance: GRC is very important in holding compliance in the loop as new regulations evolve around the world. In addition, it delivers these evolving modifications to the security team’s focus ahead of time, supplying time to plan and answer. All round, GRC will help build and handle the guidelines, regulations, and specifications to satisfy the frequently-updated business enterprise and field regulations.
Audit help: Modern corporations extend their methods and protocols to give evidence and audit product to their auditors. Ensuring procedures and best tactics are nicely documented will display that the house is held in order. Critical audit materials could consist of: Incident response, cybersecurity recognition teaching, internal management test benefits, cybersecurity compliance assessments, and far more. GRC can help craft and retain a solitary supply of reality for compliance that will allow everybody to be on the proper site.
Information privacy: GRC allows organizations stay on best of the at any time-shifting landscape of privacy rules. How? by letting the IT workforce to assure that the appropriate security, logging, geographic storage, and so on. are in spot to protect customers’ and employees’ details.
Visibility: GRC’s built-in technique allows corporations to get visibility into every single component of their security compliance packages. This is very important as it allows unique models, managers, and personnel to see the major photograph and make info-travel and educated selections.
In summary:
A nicely-planned GRC plan enables businesses to:
- Obtain and retain high-good quality data
- Increase final decision generating
- Promote collaboration
- Enhance accountability
- Make a potent lifestyle
- Improve performance and agility
- Present visibility
- Lowers expenses by supporting acceptable investments
- Boost integration
- Guard the firm’s benefit and status
GRC and Cybersecurity: Why do corporations need to have an integrated solution?
Integrating GRC and cybersecurity is imperative for organizations that want to develop a lengthy-phrase, prosperous security tactic. Apart from speedier interaction, congruent metrics, collaboration, and conclusion-building, the integration of GRC and cybersecurity provides other distinctive advantages.
An built-in solution minimizes manual input and the possible for human mistake, lessening expenses and giving corporations a lot more time to produce extra price for the company.
Extra importantly, a sturdy integration aids the board to obviously and comprehensively visualize the organization’s security posture. By being familiar with the cross-purposeful posture, business enterprise directors can convey to far better security stories to convey belief to prospects and empower staff.
To sum up:
GRC and cybersecurity work hand in hand towards a decreased-risk potential and worth creation, — they are not able to exist without having each individual other. When cybersecurity aims to guard programs, networks, and facts (from a specialized standpoint), GRC communicates the best strategy and procedures to attain so.
With an built-in solution, businesses will:
- Improve efficiencies
- Enrich security posture
- Tell much better security stories
- Improve visibility throughout the board
- Raise aid from leadership
- Stay away from compliance/regulatory fines
- IT and security groups set the tone for the complete company
- Hand in hand toward a lower-risk potential
Empowering cybersecurity via GRC – methodology
The OCEG has created this Capability Design (Pink Reserve) as an open up-resource methodology that merges the sub-disciplines of governance, risk, audit, compliance, ethics/tradition, and IT into a unified method.
Organizations can evolve this conventional to address particular predicaments, from tiny tasks to group-huge rollouts. Some illustrations are:
- Anti-corruption initiatives
- Business enterprise continuity
- 3rd-party administration
The product is key to framing discussions about GRC abilities with the board, senior executives, and managers. Also, businesses could use this GRC Capacity Model with far more specific purposeful frameworks, these types of as: ISO, COSO, ISACA, IIA, NIST, and many others.
The GRC Capability Model encourages organizations to doc best practices to:
- Unify vocabulary throughout disciplines
- Outline frequent components and things
- Determine typical data demands
- Standardize methods for factors like policies and instruction
- Detect communication for absolutely everyone included.
Now, let us see how it will work.
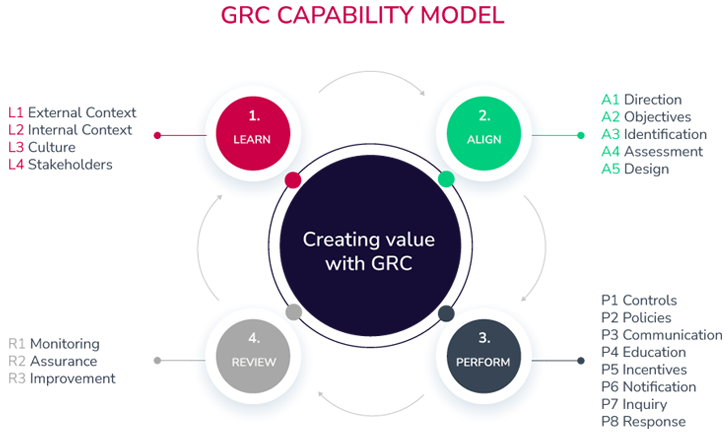
The Capacity Product has 4 components:
1. Find out
The key idea here is to detect the company society, stakeholders, and organization’s business enterprise practices to effectively guideline their targets, tactic, and aims.
As a process, it would appear like this:
- Finding out organization plans and targets
- Comprehension strategic targets
- Getting knowledgeable of the present-day and potential compliance things to do
- Connecting with the key stakeholders
2. Align
This step focuses on unifying system with targets and steps with techniques. The goal right here is to have an integrated solution the place senior management is engaged and supports the procedure of selection-making.
In very simple text, this course of action requires:
- Align business targets with the strategy
- Align executives with stakeholders’ expectations
- Align source allocation arranging with aims
3. Execute
Right after aligning business aims and aims, it can be time to conduct. This step defines employing acceptable controls and procedures, stopping and remediating undesired risks, and monitoring to detect issues as soon as feasible.
4. Evaluate
As a last action, it can be imperative to overview the style and operational overall performance of the latest tactic and actions. Much more importantly, this phase encourages companies to review objectives to regularly improve the built-in GRC routines.
What is the objective of this model?
To build a regular and integral improvement process to achieve exceptional functionality and produce value for the business.
Get your no cost session with StandardFusion and discover how you can design and style an built-in GRC application to reinforce your cybersecurity and protect your organization’s price.
Uncovered this post attention-grabbing? Observe THN on Facebook, Twitter and LinkedIn to study far more distinctive content we publish.
Some parts of this article are sourced from:
thehackernews.com


 LofyGang Distributed ~200 Malicious NPM Packages to Steal Credit Card Data
LofyGang Distributed ~200 Malicious NPM Packages to Steal Credit Card Data