Insider threats accounted for just about 35% of all unauthorized obtain cyber incidents in the third quarter of 2022, its greatest quarterly stage to day, Kroll has discovered in its Q3 2022 Threat Landscape report, posted on November 8, 2022.
In accordance to Kroll, the surge is predominantly because of to the phenomenon of the ‘great resignation’ in the wake of the COVID-19 pandemic and the shift to remote do the job.
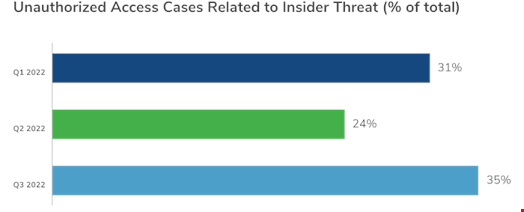 Insider threats represented 35% of all unauthorized obtain incidents in Q3 2022, when compared with 31% in Q1 and 24% in Q2. © Kroll
Insider threats represented 35% of all unauthorized obtain incidents in Q3 2022, when compared with 31% in Q1 and 24% in Q2. © Kroll

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“While usually a problem, the risk of insider danger is specially superior through the personnel termination course of action. Disgruntled employees may possibly seek out to steal data or firm insider secrets to publicly undermine an group, even though other personnel might find to shift around data–such as contacts lists and other proprietary documents–that they can leverage at their new businesses,” reads the report.
Insider threats require providers to rethink their security posture, Jaycee Roth, Kroll associate controlling director, argued in the report. “Unlike the standard instances in cybersecurity, where by you are defending the network from (at least in the first attack phase) external attackers, in an insider menace predicament, you are defending the small business from an individual on the inside of. This can be notably hard, as the person frequently will not elevate any purple flags and could have a substantial level of permissions and obtain rights.”
Laurie Iacono, a further Kroll affiliate managing director, stated, “To counter insider threat, companies should spend close interest to the entry legal rights they give to employees and constantly try to retain a ‘least-privilege’ ecosystem,”
“Monitoring for suspicious exercise – these types of as a specifically substantial details obtain or unknown USB device – is one more way to place likely compromises of security. Earlier mentioned all, apparent guidance to workforce on what is and is not permitted, mixed with speedy and economical IT and HR processes that do the job jointly in harmony, will show the greatest protection against insider danger turning into a trojan horse,” Iacono ongoing, talking through a push conference on Oct 8, 2022.
Uptick in Phishing and USB-Enabled Incidents
Total, the report demonstrates that cyber incidents involving unauthorized access slightly rose to 27% of all gatherings in Q3 2022, from 17% in Q1 and 26% in Q2. Email compromise arrived 1st, symbolizing a steady 30% share of all incidents.
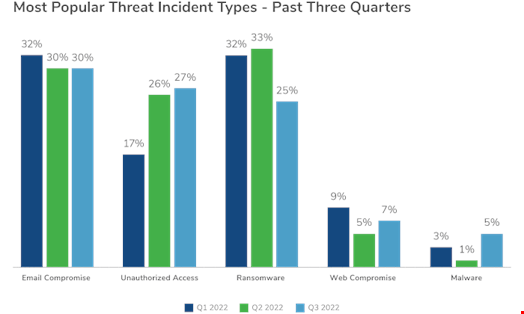 Though unauthorized obtain rose and ransomware dropped, email compromise stored a stable share of all incidents. © Kroll
Though unauthorized obtain rose and ransomware dropped, email compromise stored a stable share of all incidents. © Kroll
However, the share of ransomware incidents reduced from 32% in Q2 to 25% in Q3, partly because of to the Conti hacking group officially shutting down their actor-controlled web page on June 23. “The official launch of LockBit 3. dominated the ransomware headlines in the first component of Q3 [and the] incidence of LockBit cases enhanced significantly throughout the quarter,” notes the report.
Other findings incorporate an uptick in phishing and USB-based malware, two important vectors for danger actors to get qualifications for initial accessibility.
With regards to qualified industries, Kroll observed that professional providers overtook health care as the most specific sector all round in Q3, accounting for 21% of all scenarios, when compared with just 12% in Q2.
Manufacturing and economic providers adopted, with 12% and 11% of all cases, respectively. Health care targets dropped, accounting for only 9% of all situations, as opposed with 21% in Q2.
Listen to the IntoSecurity Podcast Episode 39 below to have an understanding of a lot more about insider threats and their influence on cybersecurity right now.
Some areas of this post are sourced from:
www.infosecurity-journal.com


 Majority of Security Managers Lack Threat Intelligence Skills
Majority of Security Managers Lack Threat Intelligence Skills