A new destructive campaign has been spotted having benefit of Windows event logs to stash chunks of shellcode for the 1st time in the wild.
“It permits the ‘fileless’ previous stage trojan to be concealed from plain sight in the file method,” Kaspersky researcher Denis Legezo claimed in a specialized write-up revealed this week.
The stealthy an infection process, not attributed to a identified actor, is considered to have commenced in September 2021 when the supposed targets have been lured into downloading compressed .RAR files containing Cobalt Strike and Silent Crack.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The adversary simulation software program modules are then utilized as a launchpad to inject code into Windows process processes or dependable programs.
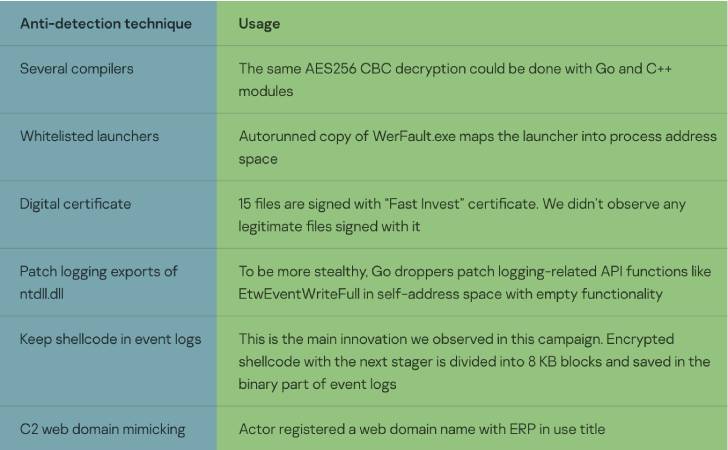
Also notable is the use of anti-detection wrappers as aspect of the toolset, suggesting an endeavor on the portion of the operators to fly beneath the radar.
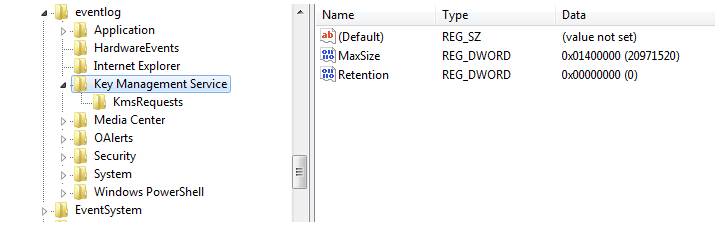
Just one of the critical procedures is to keep encrypted shellcode that contains the following-phase malware as 8KB pieces in party logs, a in no way-before-noticed method in real-entire world attacks, that’s then merged and executed.
The remaining payload is a set of trojans that hire two various conversation mechanisms — HTTP with RC4 encryption and unencrypted with named pipes — which make it possible for it to operate arbitrary commands, obtain data files from a URL, escalate privileges, and take screenshots.
A different indicator of the risk actor’s evasion tactics is the use of facts gleaned from first reconnaissance to produce succeeding phases of the attack chain, together with the use of a remote server that mimics reputable software package applied by the target.
“The actor driving this marketing campaign is pretty capable,” Legezo said. “The code is fairly unique, with no similarities to acknowledged malware.”
The disclosure will come as Sysdig scientists demonstrated a way to compromise go through-only containers with fileless malware that is executed in-memory by leveraging a critical flaw in Redis servers.
Uncovered this post attention-grabbing? Abide by THN on Fb, Twitter and LinkedIn to browse far more special written content we put up.
Some areas of this post are sourced from:
thehackernews.com


 QNAP Releases Firmware Patches for 9 New Flaws Affecting NAS Devices
QNAP Releases Firmware Patches for 9 New Flaws Affecting NAS Devices