1000’s of Citrix Application Delivery Controller (ADC) and Gateway endpoints continue to be susceptible to two critical security flaws disclosed by the enterprise in excess of the previous handful of months.
The issues in question are CVE-2022-27510 and CVE-2022-27518 (CVSS scores: 9.8), which were being addressed by the virtualization services supplier on November 8 and December 13, 2022, respectively.
Though CVE-2022-27510 relates to an authentication bypass that could be exploited to obtain unauthorized entry to Gateway person abilities, CVE-2022-27518 concerns a remote code execution bug that could enable the takeover of affected methods.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Citrix and the U.S. National Security Agency (NSA), before this thirty day period, warned that CVE-2022-27518 is staying actively exploited in the wild by risk actors, which includes the China-joined APT5 point out-sponsored team.
Now, in accordance to a new investigation from NCC Group’s Fox-IT study staff, hundreds of internet-dealing with Citrix servers are however unpatched, generating them an beautiful concentrate on for hacking crews.
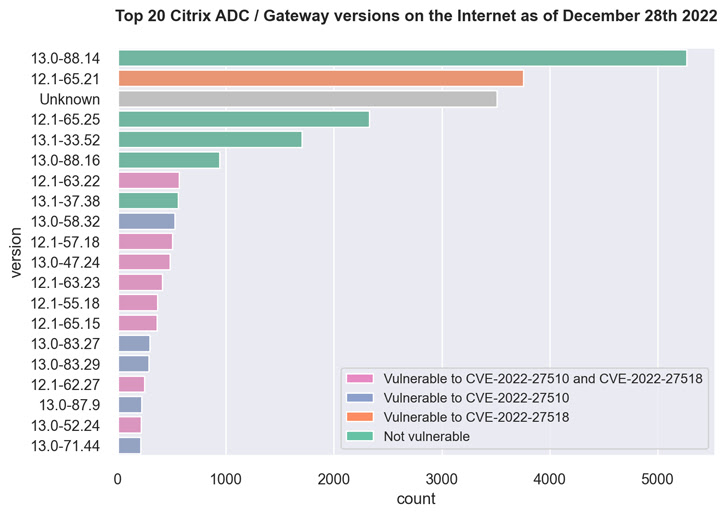
This contains in excess of 3,500 Citrix ADC and Gateway servers running variation 12.1-65.21 that are susceptible to CVE-2022-27518, as perfectly as much more than 500 servers running 12.1-63.22 that are vulnerable to both of those flaws.
A the vast majority of the servers, amounting to no significantly less than 5,000, are working 13.-88.14, a model which is immune to CVE-2022-27510 and CVE-2022-27518.
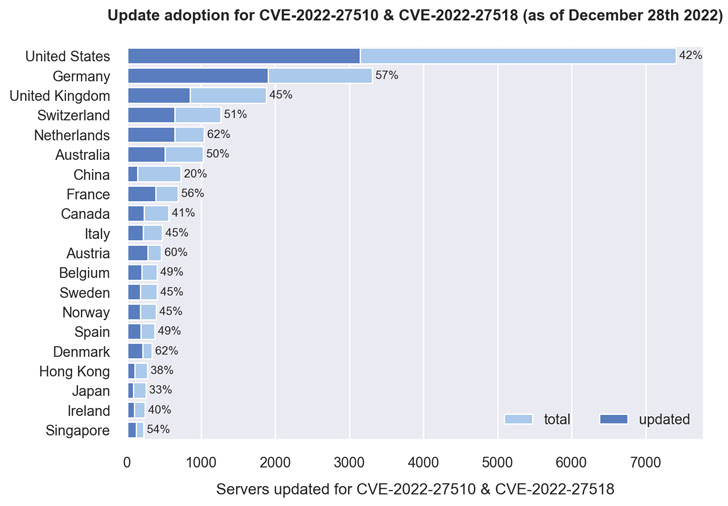
A nation-smart breakdown exhibits that more than 40% of servers situated in Denmark, the Netherlands, Austria, Germany, France, Singapore, Australia, the U.K., and the U.S. have been up to date, with China faring the worst, where only 20% of almost 550 servers have been patched.
Fox-IT explained it was capable to deduce the variation facts from an MD5-like hash price present in the HTTP reaction of login URL (i.e., “ns_gui/vpn/index.html”) and mapping it to their respective versions.
Identified this report attention-grabbing? Abide by us on Twitter and LinkedIn to read additional special content material we article.
Some elements of this post are sourced from:
thehackernews.com


 New Malvertising Campaign via Google Ads Targets Users Searching for Popular Software
New Malvertising Campaign via Google Ads Targets Users Searching for Popular Software