The genuine command-and-regulate (C2) framework recognised as Sliver is attaining far more traction from threat actors as it emerges as an open up resource choice to Cobalt Strike and Metasploit.
The results occur from Cybereason, which in-depth its internal workings in an exhaustive examination last 7 days.
Sliver, formulated by cybersecurity firm BishopFox, is a Golang-dependent cross-platform post-exploitation framework that’s created to be utilized by security specialists in their pink group functions.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Its myriad features for adversary simulation – like dynamic code generation, in-memory payload execution, and procedure injection – have also produced it an interesting instrument for menace actors on the lookout to get elevated obtain to the goal system on gaining an initial foothold.
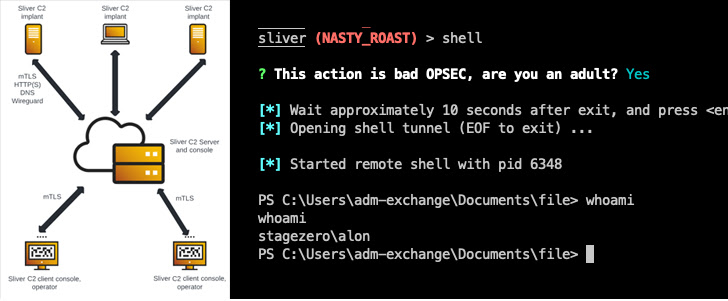
In other words, the program is employed as a 2nd-phase to conduct following ways of the attack chain just after currently compromising a device working with 1 of the original intrusion vectors such as spear-phishing or exploitation of unpatched flaws.
“Silver C2 implant is executed on the workstation as stage two payload, and from [the] Sliver C2 server we get a shell session,” Cybereason scientists Loïc Castel and Meroujan Antonyan explained. “This session supplies multiple methods to execute commands and other scripts or binaries.”
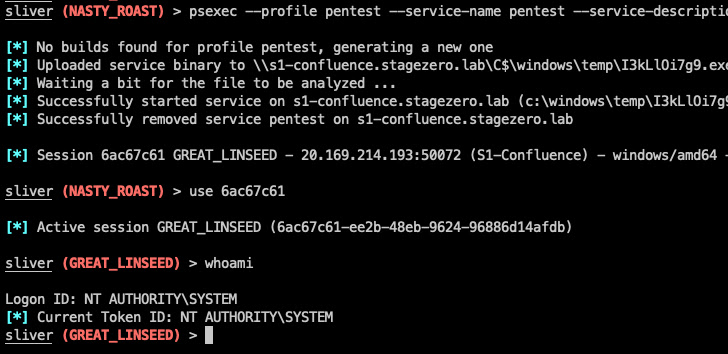
A hypothetical attack sequence comprehensive by the Israeli cybersecurity firm displays that Sliver could be leveraged for privilege escalation, subsequent it up by credential theft and lateral motion to in the long run acquire in excess of the domain controller for the exfiltration of delicate facts.
Sliver has been weaponized in modern many years by the Russia-linked APT29 group (aka Cozy Bear) as very well as cybercrime operators like Shathak (aka TA551) and Exotic Lily (aka Projector Libra), the latter of which is attributed to the Bumblebee malware loader.
That said, Sliver is considerably from the only open resource framework to be exploited for destructive finishes. Past thirty day period, Qualys disclosed how many hacking teams, which include Turla, Vice Society, and Wizard Spider, have utilized Empire for article-exploitation and to extend their foothold in victim environments.
“Empire is an spectacular post exploitation framework with expansive capabilities,” Qualys security researcher Akshat Pradhan said. “This has led to it turning into a repeated preferred toolkit of numerous adversaries.”
Observed this article exciting? Follow us on Twitter and LinkedIn to examine additional distinctive content material we put up.
Some areas of this report are sourced from:
thehackernews.com


 New Government Cyber Advice for £100bn UK Charity Sector
New Government Cyber Advice for £100bn UK Charity Sector