
Menace searching is the course of action of wanting for malicious exercise and its artifacts in a laptop or computer technique or network. Risk looking is carried out intermittently in an setting regardless of no matter if or not threats have been discovered by automatic security methods. Some menace actors may well stay dormant in an organization’s infrastructure, extending their entry when waiting around for the suitable chance to exploit found weaknesses.
Consequently it is essential to conduct menace looking to discover malicious actors in an environment and prevent them right before they attain their supreme purpose.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
To correctly execute danger hunting, the menace hunter should have a systematic strategy to emulating probable adversary behavior. This adversarial habits establishes what artifacts can be searched for that indicate ongoing or previous malicious exercise.
MITRE ATT&CK
More than the several years, the security community has observed that menace actors have frequently utilized quite a few practices, procedures, and procedures (TTPs) to infiltrate and pivot throughout networks, elevate privileges, and exfiltrate private details. This has led to the growth of a variety of frameworks for mapping the activities and approaches of menace actors. One illustration is the MITRE ATT&CK framework.
MITRE ATT&CK is an acronym that stands for MITRE Adversarial Techniques, Approaches, and Popular Knowledge (ATT&CK). It is a nicely-documented information base of actual-entire world risk actor steps and behaviors. MITRE ATT&CK framework has 14 methods and quite a few tactics that recognize or show an attack in progress. MITRE makes use of IDs to reference the tactic or approach utilized by an adversary.
The Wazuh unified XDR and SIEM platform
Wazuh is an open up supply unified XDR and SIEM system. The Wazuh alternative is built up of a one common agent that is deployed on monitored endpoints for menace detection and automated response. It also has central elements (Wazuh server, indexer, and dashboard) that review and visualize the security occasions facts collected by the Wazuh agent. It safeguards on-premises and cloud workloads.
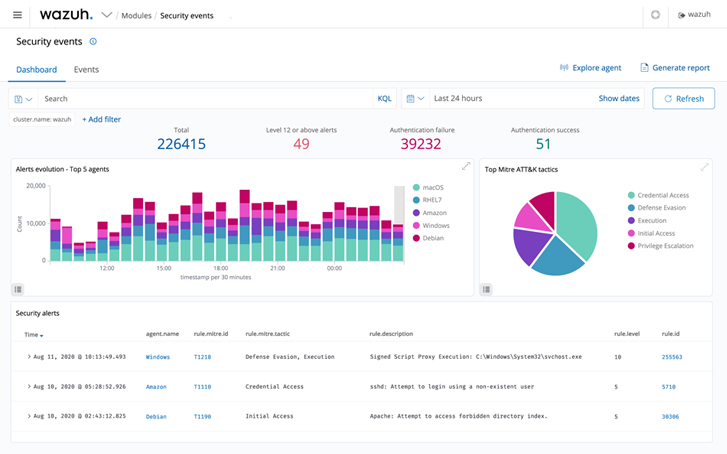 Figure 1: Wazuh security celebration dashboard
Figure 1: Wazuh security celebration dashboard
Menace searching with Wazuh
Danger hunters use a variety of equipment, processes, and approaches to look for for malicious artifacts in an surroundings. These include things like but are not limited to applying resources for security monitoring, file integrity checking, and endpoint configuration evaluation.
Wazuh gives sturdy abilities like file integrity checking, security configuration assessment, risk detection, automatic response to threats, and integration with solutions that offer threat intelligence feeds.
Wazuh MITRE ATT&CK module
Wazuh comes with the MITRE ATT&CK module out-of-the-box and danger detection regulations mapped against their corresponding MITRE approach IDs. This module has 4 elements which are:
a. The intelligence part of the Wazuh MITRE ATT&CK module: Incorporates comprehensive info about threat groups, mitigation, program, ways, and tactics used in cyber attacks. This component will help danger hunters to recognize and classify distinct TTPs that adversaries use.
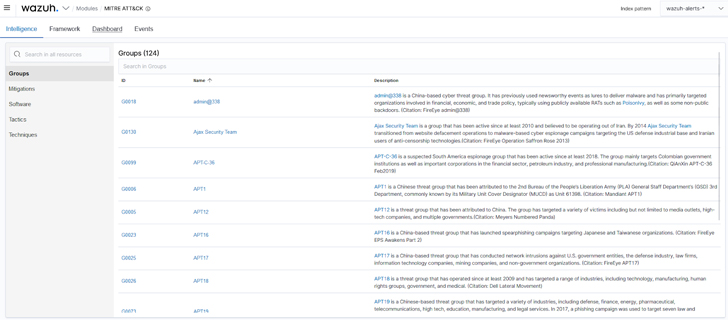 Figure 2: Wazuh MITRE ATT&CK Intelligence
Figure 2: Wazuh MITRE ATT&CK Intelligence
b. The framework element of the Wazuh MITRE ATT&CK module: Helps risk hunters slender down threats or compromised endpoints. This part works by using specific approaches to see all the functions connected to that technique and the endpoints wherever these activities occurred.
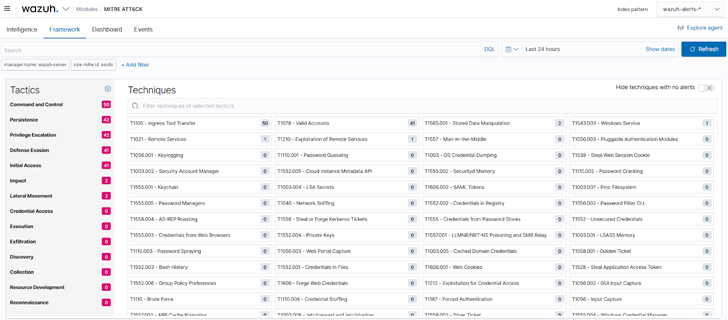 Figure 3: Wazuh MITRE ATT&CK framework
Figure 3: Wazuh MITRE ATT&CK framework
c. The dashboard component of the MITRE ATT&CK module: Assists to summarize all events into charts to aid risk hunters in having a swift overview of MITRE relevant actions in an infrastructure.
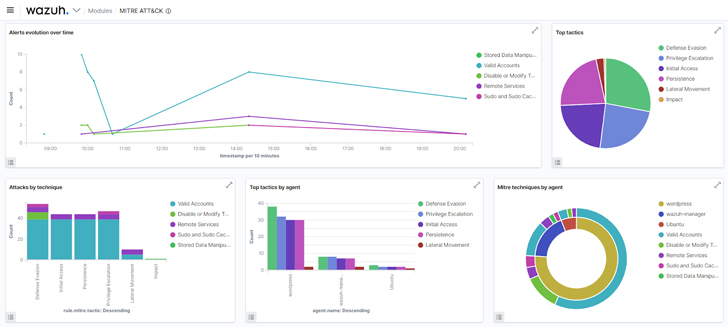 Determine 4: Wazuh MITRE ATT&CK dashboard
Determine 4: Wazuh MITRE ATT&CK dashboard
d. The Wazuh MITRE ATT&CK gatherings part: Shows functions in actual-time, with their respective MITRE IDs, to far better have an understanding of every single claimed alert.
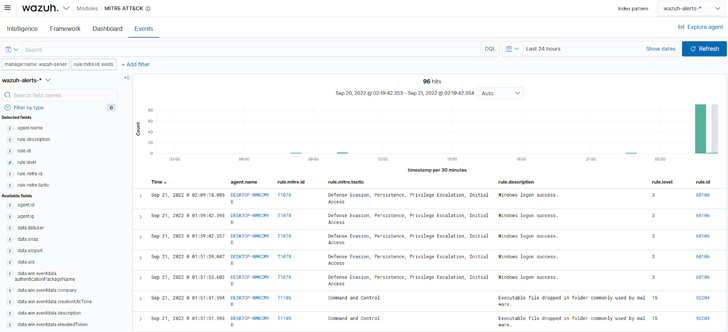 Figure 5: Wazuh MITRE ATT&CK gatherings
Figure 5: Wazuh MITRE ATT&CK gatherings
Wazuh principles and decoders
Wazuh has out-of-the-box policies and decoders to parse security and runtime knowledge generated from diverse resources. Wazuh supports policies for diverse systems (e.g., Docker, CISCO, Microsoft Exchange), which have been mapped to their correct MITRE IDs. Users can also develop custom made policies and decoders and map every rule with its acceptable MITRE tactic or technique. This blog site publish shows an case in point of leveraging MITRE ATT&CK and Wazuh customized guidelines to detect an adversary.
Security Configuration Assessment (SCA) module
The Wazuh SCA module performs periodic scans in endpoints to detect method and application misconfigurations. It can also be made use of to scan for indicators of compromise, like destructive documents and folders that have been created by malware. Analyzing program inventories, companies, misconfigurations, and alterations in the configuration on an endpoint can assistance threat hunters detect attacks underway.
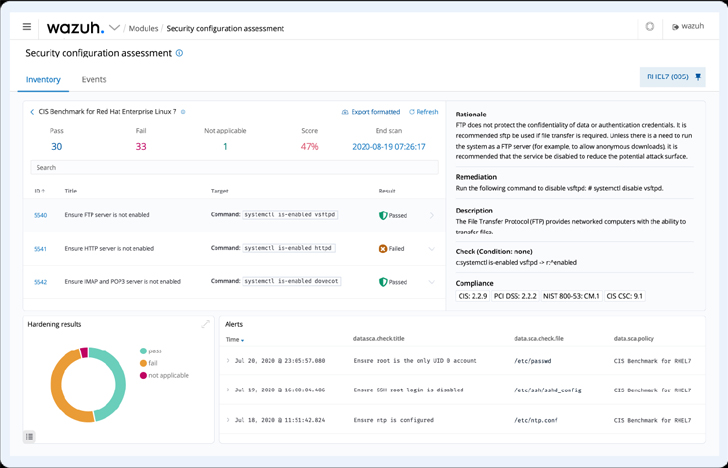 Determine 6: Wazuh SCA dashboard
Determine 6: Wazuh SCA dashboard
Integration with danger intelligence alternatives
Owing to its open up source mother nature, Wazuh provides an possibility to combine with danger intelligence APIs and other security answers. Wazuh integrates with open up resource risk intelligence platforms like Virustotal, URLHaus, MISP, and AbuseIPDB to title a several. Dependent on the integration, relevant alerts look in the Wazuh dashboard. Specific information and facts, such as IP addresses, file hashes, and URLs, can be queried applying filters on the Wazuh dashboard.
File integrity checking
File integrity checking (FIM) is applied to monitor and audit sensitive data files and folders on endpoints. Wazuh offers an FIM module that screens and detects changes in specified directories or information on an endpoint’s filesystem. The FIM module can also detect when data files released to endpoints match hashes of regarded malware.
Wazuh archives
Wazuh archives can be enabled to gather and store all security gatherings ingested from monitored endpoints. This element assists risk hunters by providing them with details that can be utilized to build detection policies and keep in advance of risk actors. Wazuh archives are also useful in meeting regulatory compliance where by audit log historical past is required.
Summary
The MITRE ATT&CK framework will help to effectively classify and determine threats in accordance to found TTPs. Wazuh utilizes its committed MITRE ATT&CK components to show data about how security details from endpoints correspond to TTPs. The risk looking abilities of Wazuh aid cybersecurity analysts to detect clear cyber attacks as perfectly as fundamental compromises to infrastructure.
Wazuh is a free of charge and open resource system that can be employed by companies with cloud and on-premises infrastructure. Wazuh has a person of the fastest-rising open source local community in the environment, where by discovering, discussions, and aid is provided at zero charge. Look at out this documentation to get started out with Wazuh.
Observed this short article appealing? Observe THN on Facebook, Twitter and LinkedIn to browse more distinctive material we post.
Some components of this short article are sourced from:
thehackernews.com


 Russian Duo Indicted Over E-Book Piracy
Russian Duo Indicted Over E-Book Piracy