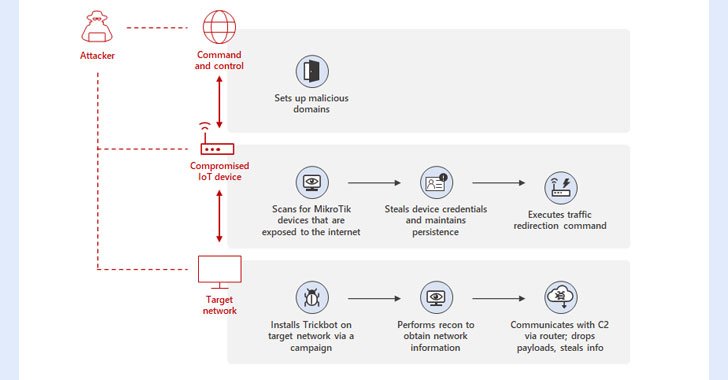
Microsoft on Wednesday in depth a earlier undiscovered system place to use by the TrickBot malware that will involve using compromised Internet of Matters (IoT) gadgets as a go-involving for creating communications with the command-and-manage (C2) servers.
“By applying MikroTik routers as proxy servers for its C2 servers and redirecting the targeted traffic as a result of non-conventional ports, TrickBot adds yet another persistence layer that will help malicious IPs evade detection by regular security programs,” Microsoft’s Defender for IoT Investigation Group and Menace Intelligence Centre (MSTIC) said.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
TrickBot, which emerged as a banking trojan in 2016, has advanced into a subtle and persistent threat, with its modular architecture enabling it to adapt its techniques to go well with distinctive networks, environments, and devices as very well as offer you entry-as-a-service for up coming-phase payloads like Conti ransomware.
The expansion to TrickBot’s capabilities arrives amid reports of its infrastructure likely offline, even as the botnet has continuously refined its characteristics to make its attack framework durable, evade reverse engineering, and maintain the security of its C2 servers.
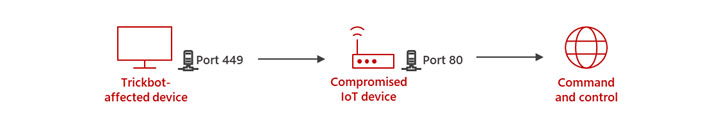
Specifically, the new method determined by MSTIC includes leveraging hacked IoT gadgets these kinds of as routers from MikroTik to “produce a line of conversation in between the TrickBot-influenced device and the C2 server.”
This also entails breaking into the routers by employing a blend of strategies, specifically default passwords, brute-power attacks, or exploiting a now-patched flaw in MikroTik RouterOS (CVE-2018-14847), adopted by switching the router’s password to preserve entry.
In the future stage, the attackers then issue a network tackle translation (NAT) command which is made to redirect traffic among ports 449 and 80 in the router, developing a route for the TrickBot-contaminated hosts to connect with the C2 server.
“As security answers for common computing products go on to evolve and improve, attackers will take a look at option strategies to compromise focus on networks,” the scientists claimed. “Attack makes an attempt from routers and other IoT equipment are not new, and getting unmanaged, they can conveniently be the weakest one-way links in the network.”
Observed this posting fascinating? Stick to THN on Facebook, Twitter and LinkedIn to browse additional special content material we article.
Some parts of this posting are sourced from:
thehackernews.com


 SentinelOne to acquire Attivo Networks for $617 million
SentinelOne to acquire Attivo Networks for $617 million