U.S. cybersecurity and intelligence businesses have warned about China-dependent condition-sponsored cyber actors leveraging network vulnerabilities to exploit community and non-public sector companies since at the very least 2020.
The common intrusion strategies goal to exploit publicly discovered security flaws in network equipment these kinds of as Tiny Place of work/Residence Office environment (SOHO) routers and Network Hooked up Storage (NAS) products with the intention of attaining deeper access to victim networks.
In addition, the actors made use of these compromised units as route command-and-command (C2) visitors to split into other targets at scale, the U.S. Countrywide Security Company (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI) reported in a joint advisory.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The perpetrators, other than shifting their practices in reaction to public disclosures, are known to utilize a blend of open-source and custom made equipment for reconnaissance and vulnerability scanning as well as to obscure and mix their activity.
The attacks by themselves are facilitated by accessing compromised servers, which the agencies named hop factors, from China-centered IP addresses, working with them to host C2 domains, email accounts, and connect with the target networks.
“Cyber actors use these hop details as an obfuscation approach when interacting with victim networks,” the agencies observed, detailing the adversary’s sample of weaponizing flaws in telecommunications corporations and network service providers.
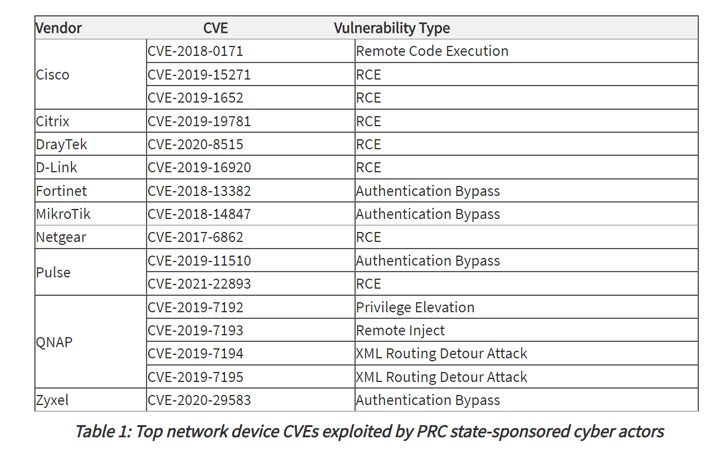
Upon attaining a foothold into the network by using an unpatched internet-dealing with asset, the actors have been noticed obtaining qualifications for user and administrative accounts, followed by managing router commands to “surreptitiously route, capture, and exfiltrate visitors out of the network to actor-controlled infrastructure.”
Past but not the very least, the attackers also modified or eliminated neighborhood log information to erase evidence of their action to even further conceal their existence and evade detection.

The companies did not solitary out a specific threat actor, but mentioned that the conclusions mirror Chinese condition-sponsored groups’ historical past of aggressively striking critical infrastructure to steal sensitive information, emerging important technologies, mental property, and individually identifiable information and facts.
The disclosure also comes fewer than a thirty day period after the cybersecurity authorities disclosed the most routinely exploited original access vectors to breach targets, some of which include misconfigured servers, weak password controls, unpatched application, and failure to block phishing makes an attempt.
“Entities can mitigate the vulnerabilities mentioned in this advisory by making use of the offered patches to their techniques, changing stop-of-lifetime infrastructure, and applying a centralized patch administration program,” the companies stated.
Observed this write-up interesting? Observe THN on Facebook, Twitter and LinkedIn to read extra exclusive articles we post.
Some elements of this posting are sourced from:
thehackernews.com

 FBI Seizes ‘SSNDOB’ ID Theft Service for Selling Personal Info of 24 Million People
FBI Seizes ‘SSNDOB’ ID Theft Service for Selling Personal Info of 24 Million People