State-sponsored actors backed by the Russian government consistently qualified the networks of various U.S. cleared protection contractors (CDCs) to get proprietary documents and other private information and facts pertaining to the country’s protection and intelligence systems and abilities.
The sustained espionage marketing campaign is mentioned to have commenced at minimum two many years in the past from January 2020, in accordance to a joint advisory released by the U.S. Federal Bureau of Investigation (FBI), National Security Agency (NSA), and Cybersecurity and Infrastructure Security Agency (CISA).
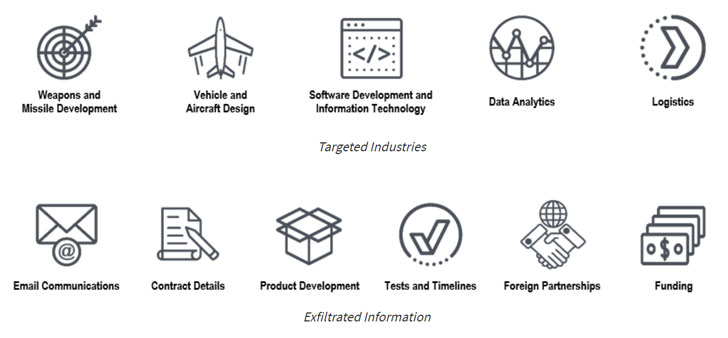
“These ongoing intrusions have enabled the actors to purchase delicate, unclassified information, as effectively as CDC-proprietary and export-managed technology,” the agencies mentioned. “The obtained facts provides important insight into U.S. weapons platforms development and deployment timelines, car or truck technical specs, and plans for communications infrastructure and info technology.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Compromised entities involve contractors that dabble in command, manage, communications, and overcome methods surveillance and reconnaissance weapons and missile progress car and aircraft style and design and program advancement, knowledge analytics, and logistics.
The risk actors depend on “widespread but successful” strategies to breach target networks this sort of as spear-phishing, credential harvesting, brute-drive attacks, password spray methods, and exploitation of regarded vulnerabilities in VPN products, right before shifting laterally to create persistence and exfiltrate info.
Some of the vulnerabilities leveraged by the attackers for initial accessibility and privilege escalation are as follows –
- CVE-2018-13379 (CVSS score: 9.8) – Path traversal vulnerability in Fortinet’s FortiGate SSL VPN
- CVE-2020-0688 (CVSS rating: 8.8) – Microsoft Exchange validation essential distant code execution vulnerability
- CVE-2020-17144 (CVSS score: 8.4) – Microsoft Trade distant code execution vulnerability
Numerous of the intrusions also include getting a foothold to company and cloud networks, with the adversaries retaining persistent access to the compromised Microsoft 365 environments for as lengthy as six months to continuously harvest e-mail and data.
“As CDCs uncover and patch identified vulnerabilities on their networks, the actors change their tradecraft to look for new implies of entry,” the organizations defined. “This activity necessitates CDCs retain continual vigilance for computer software vulnerabilities and out-of-date security configurations, in particular in internet-facing techniques.”
Among other malicious functions observed is the plan use of digital personal servers (VPSs) as an encrypted proxy and the use of authentic credentials to exfiltrate e-mail from the victim’s organization email technique. The advisory, having said that, does not solitary out any Russian point out actor by name.
“About the last a number of several years, Russian condition-sponsored cyber actors have been persistent in targeting U.S. cleared defense contractors to get at delicate information,” said Rob Joyce, director of NSA Cybersecurity. “Armed with insights like these, we can greater detect and defend vital property jointly.”
Identified this post fascinating? Stick to THN on Fb, Twitter and LinkedIn to study far more distinctive material we post.
Some areas of this write-up are sourced from:
thehackernews.com




 TrickBot Ravages Customers of Amazon, PayPal and Other Top Brands
TrickBot Ravages Customers of Amazon, PayPal and Other Top Brands