The Laptop or computer Emergency Reaction Crew of Ukraine (CERT-UA) has warned of phishing attacks that deploy an data-thieving malware identified as Jester Stealer on compromised devices.
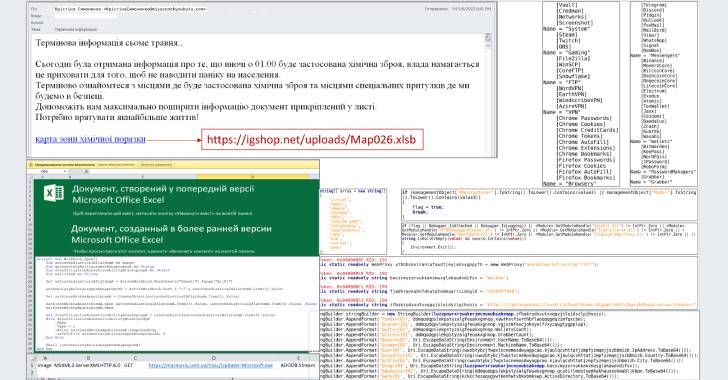
The mass email marketing campaign carries the topic line “chemical attack” and includes a backlink to a macro-enabled Microsoft Excel file, opening which potential customers to pcs acquiring infected with Jester Stealer.
The attack, which calls for prospective victims to permit macros immediately after opening the document, operates by downloading and executing an .EXE file that is retrieved from compromised web resources, CERT-UA thorough.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Jester Stealer, which was 1st documented by Cyble in February 2022, arrives with features to steal and transmit login credentials, cookies, and credit card facts together with data from passwords professionals, chat messengers, email consumers, crypto wallets, and gaming apps to the attackers.
“The hackers get the stolen info by means of Telegram applying statically configured proxy addresses (e.g., within just TOR),” the company said. “They also use anti-assessment strategies (anti-VM/debug/sandbox). The malware has no persistence system — it is deleted as soon as its operation is finished.”
The Jester Stealer campaign coincides with an additional phishing attack that CERT-UA has attributed to the Russian country-condition actor tracked as APT28 (aka Extravagant Bear aka Strontium).
The e-mail, titled “Кібератака” (this means cyberattack in Ukrainian), masquerade as a security notification from CERT-UA and come with a RAR archive file “UkrScanner.rar” attachment that, when opened, deploys a malware referred to as CredoMap_v2.
“As opposed to prior versions of this stealer malware, this one works by using the HTTP protocol for facts exfiltration,” CERT-UA pointed out. “Stolen authentication details will be sent to a web resource, deployed on the Pipedream platform, by means of the HTTP Post requests.”
The disclosures abide by equivalent conclusions from Microsoft’s Electronic Security Unit (DSU) and Google’s Threat Evaluation Group (TAG) about Russian state-sponsored hacking crews carrying out credential and data theft functions in Ukraine.
Uncovered this short article attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to browse additional exceptional content material we put up.
Some components of this write-up are sourced from:
thehackernews.com

 U.S. Offering $10 Million Reward for Information on Conti Ransomware Hackers
U.S. Offering $10 Million Reward for Information on Conti Ransomware Hackers