Russian hacking on a laptop mockup with code sprawling more than the monitor
Cyber criminals are preying on moral hackers supporting the IT Army of Ukraine by deceiving them into downloading information and facts-thieving malware.
Opportunistic cyber criminals are posing as genuine representatives of the IT Army of Ukraine and pretending to offer them with applications to deliver distributed denial of service attacks (DDoS) that eventually change out to be malware, according to researchers at Cisco Talos.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The IT Army of Ukraine is a team that mobilise through the Telegram system and was originally assembled at the begin of the conflict by a Ukrainian Minister to recruit as quite a few supporters as attainable to fight Russia in cyber house.
The group at this time has additional than 300,000 associates and posts daily ‘hit lists’ – lists of concentrate on .ru URLs for tech-savvy supporters of Ukraine to knock offline. Latest targets include Russian electronic signature services and importers of technology for the Russian army.
Criminals are concentrating on these moral hackers applying Telegram channels that are seemingly similar to the real IT Army of Ukraine team, but are not authentic.
Cisco Talos
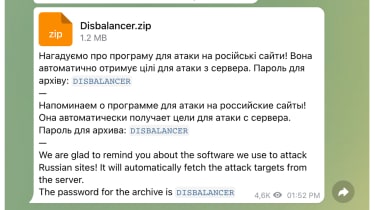
Cisco Talos researchers saw circumstances of adverts for inauthentic variations of legitimate DDoS applications, these as the authentic Disbalancer Liberator instrument, which when clicked infect the user’s program with information and facts-thieving malware that harvests credentials and cryptocurrency info.
The information and facts stealer gleans information from browsers these kinds of as Chrome and Firefox, and scans other locations on the file program for essential facts ahead of relaying it again to a Russian IP deal with.
“This is an case in point of one particular of the quite a few means opportunistic cybercriminals are making an attempt to get gain of the Russian invasion by exploiting sympathisers on each sides of the conflict,” the researchers stated.
“Such exercise could get the sort of themed email lures on news topics or donation solicitations, malicious backlinks purporting to host reduction cash or refugee aid web sites, malware masquerading as security defensive or offensive equipment, and more. Users must diligently inspect suspicious emails just before opening them and validate software package or other data files prior to downloading them.”
Cisco Talos explained evidence implies the menace actors powering the marketing campaign have been distributing infostealers since “at minimum November 2021” but have now pivoted to targeting hacktivists siding with Ukraine.
It also claimed it expects the information-stealing action to carry on and diversify as the world wide fascination in the conflict generates a potentially large pool of targets for risk actors to prey on.
Some sections of this posting are sourced from:
www.itpro.co.uk


 Multiple Security Flaws Discovered in Popular Software Package Managers
Multiple Security Flaws Discovered in Popular Software Package Managers