An unofficial patch has been designed out there for an actively exploited security flaw in Microsoft Windows that would make it attainable for data files signed with malformed signatures to sneak earlier Mark-of-the-Web (MotW) protections.
The take care of, released by 0patch, comes weeks soon after HP Wolf Security disclosed a Magniber ransomware campaign that targets end users with bogus security updates which hire a JavaScript file to proliferate the file-encrypting malware.
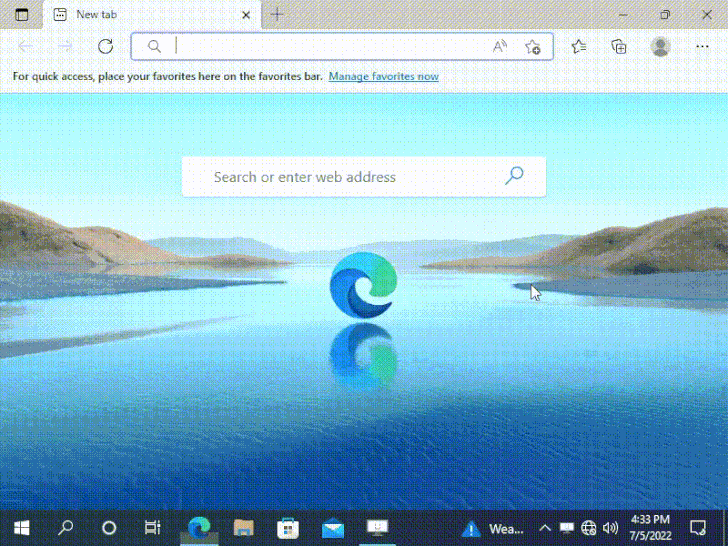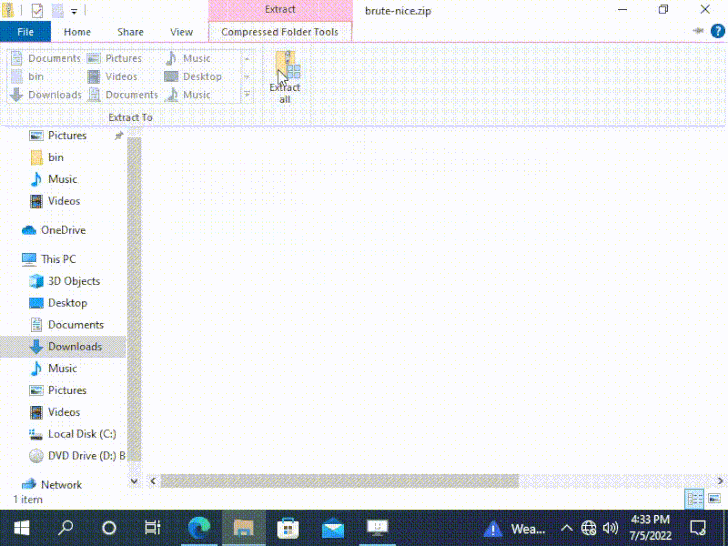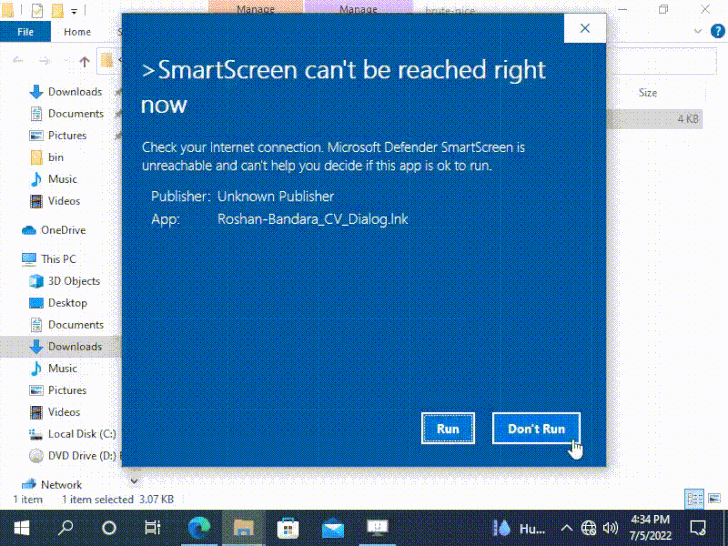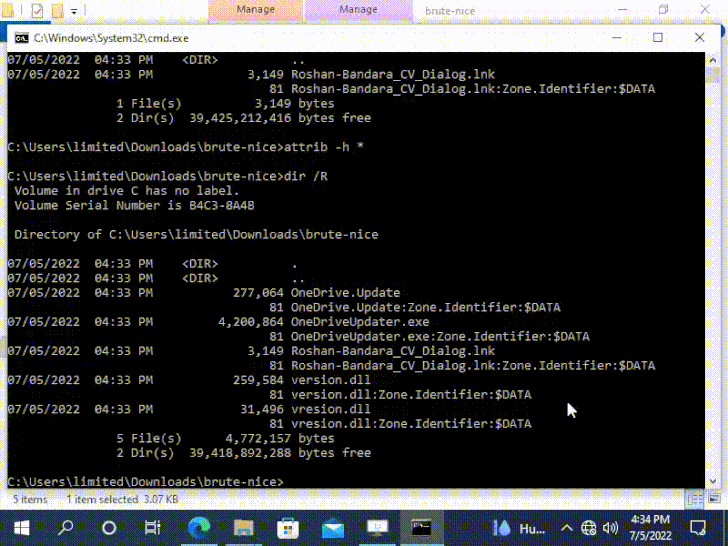
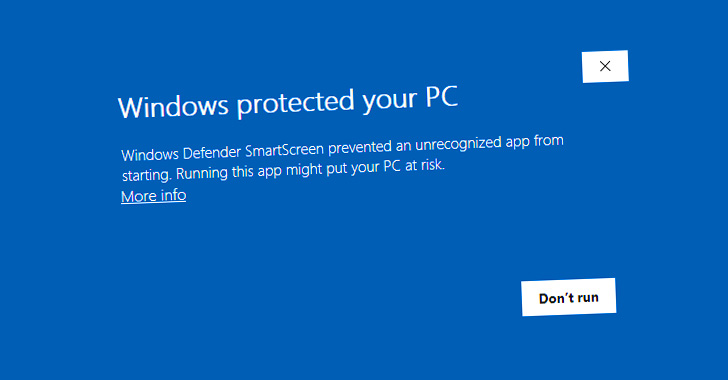
Even though data files downloaded from the internet in Windows are tagged with a MotW flag to prevent unauthorized actions, it has given that been observed that corrupt Authenticode signatures can be utilised to allow for the execution of arbitrary executables without the need of any SmartScreen warning.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Authenticode is a Microsoft code-signing technology that authenticates the identity of the publisher of a distinct piece of program and verifies whether the application was tampered with after it was signed and revealed.
“The [JavaScript] file in fact has the MotW but nonetheless executes without having a warning when opened,” HP Wolf Security researcher Patrick Schläpfer noted.
 Resource: Will Dormann Twitter
Resource: Will Dormann Twitter
“If the file has this malformed Authenticode signature, the SmartScreen and/or file-open up warning dialog will be skipped,” security researcher Will Dormann stated.
Now in accordance to 0patch co-founder Mitja Kolsek, the zero-working day bug is the end result of SmartScreen returning an exception when parsing the malformed signature, which is incorrectly interpreted as a selection to run the method alternatively than cause a warning.

Fixes for the flaw also occur a lot less than two months soon after unofficial patches had been transported for one more zero-working day MotW bypass flaw that came to light-weight in July and has considering that arrive underneath energetic attack, for each security researcher Kevin Beaumont.
The vulnerability, discovered by Dormann, relates to how Windows fails to set the MotW identifier to data files extracted from particularly crafted .ZIP information.
“Attackers thus understandably favor their destructive information not being marked with MOTW this vulnerability lets them to generate a ZIP archive this kind of that extracted malicious documents will not be marked,” Kolsek explained.
Identified this short article appealing? Stick to THN on Facebook, Twitter and LinkedIn to browse additional distinctive content we put up.
Some pieces of this write-up are sourced from:
thehackernews.com

 Most Online Shoppers Would Leave Retailer Following Breach
Most Online Shoppers Would Leave Retailer Following Breach