A zero-day distant code execution (RCE) vulnerability has occur to light in the Spring framework soon immediately after a Chinese security researcher briefly leaked a evidence-of-concept (PoC) exploit on GitHub just before deleting their account.
According to cybersecurity organization Praetorian, the unpatched flaw impacts Spring Core on Java Improvement Kit (JDK) variations 9 and later and is a bypass for an additional vulnerability tracked as CVE-2010-1622, enabling an unauthenticated attacker to execute arbitrary code on the goal system.
Spring is a software framework for constructing Java applications, including web apps on top rated of the Java EE (Business Version) system.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“In specific configurations, exploitation of this issue is straightforward, as it only calls for an attacker to deliver a crafted HTTP ask for to a vulnerable procedure,” researchers Anthony Weems and Dallas Kaman stated. “Even so, exploitation of unique configurations will call for the attacker to do added investigation to obtain payloads that will be productive.”
Additional specifics of the flaw, dubbed “SpringShell” and “Spring4Shell,” have been withheld to avoid exploitation tries and right until a deal with is in put by the framework’s maintainers, Spring.io, a subsidiary of VMware. It can be also however to be assigned a Widespread Vulnerabilities and Exposures (CVE) identifier.
It truly is worthy of noting that the flaw targeted by the zero-day exploit is different from two earlier vulnerabilities disclosed in the software framework this week, together with the Spring Framework expression DoS vulnerability (CVE-2022-22950) and the Spring Cloud expression source access vulnerability (CVE-2022-22963).
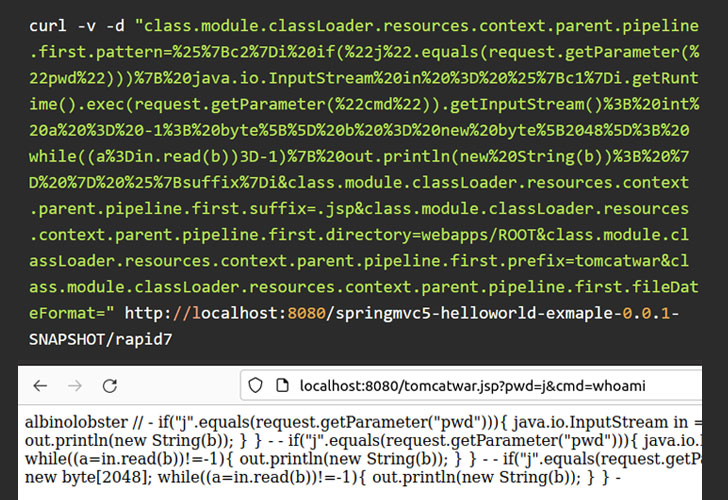
In the interim, the firm is recommending “creating a ControllerAdvice element (which is a Spring element shared across Controllers) and adding unsafe patterns to the denylist.”
Initial investigation of the new code execution flaw in Spring Main implies that its influence may not be severe. “[C]urrent info indicates in buy to exploit the vulnerability, attackers will have to find and discover web app instances that basically use the DeserializationUtils, something by now identified by builders to be harmful,” Flashpoint stated in an unbiased examination.
Irrespective of the public availability of PoC exploits, “it truly is now unclear which real-environment programs use the vulnerable operation,” Speedy7 stated. “Configuration and JRE edition may possibly also be considerable variables in exploitability and the chance of common exploitation.”
The Retail and Hospitality Information Sharing and Assessment Middle (ISAC) also issued a statement that it has investigated and verified the “validity” of the PoC for the RCE flaw, introducing it can be “continuing assessments to verify the validity of the PoC.”
“The Spring4Shell exploit in the wild seems to do the job in opposition to the inventory ‘Handling Sort Submission’ sample code from spring.io,” CERT/CC vulnerability analyst Will Dormann claimed in a tweet. “If the sample code is vulnerable, then I suspect there are without a doubt genuine-world applications out there that are susceptible to RCE.”
Located this report attention-grabbing? Abide by THN on Facebook, Twitter and LinkedIn to read through far more exceptional material we article.
Some parts of this report are sourced from:
thehackernews.com




 QNAP Warns of OpenSSL Infinite Loop Vulnerability Affecting NAS Devices
QNAP Warns of OpenSSL Infinite Loop Vulnerability Affecting NAS Devices