A new variant of the macOS malware tracked as UpdateAgent has been spotted in the wild, indicating ongoing makes an attempt on the portion of its authors to upgrade its functionalities.
“Probably one particular of the most identifiable functions of the malware is that it relies on the AWS infrastructure to host its different payloads and complete its an infection position updates to the server,” researchers from Jamf Menace Labs reported in a report.
UpdateAgent, initially detected in late 2020, has considering the fact that advanced into a malware dropper, facilitating the distribution of 2nd-phase payloads such as adware though also bypassing macOS Gatekeeper protections.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
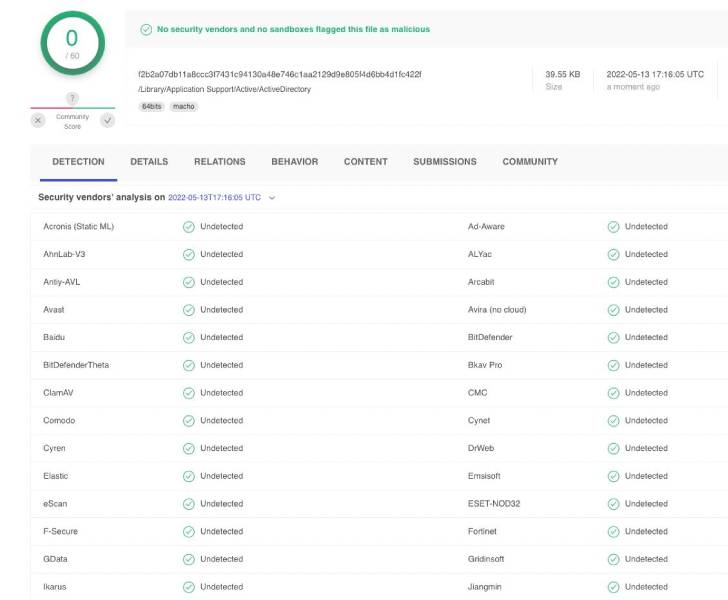
The recently identified Swift-dependent dropper masquerades as Mach-O binaries named “PDFCreator” and “ActiveDirectory” that, upon execution, create a link to a distant server and retrieve a bash script to be executed.

“The principal change [between the two executables] is that it reaches out to a distinct URL from which it must load a bash script,” the researchers mentioned.
These bash scripts, named “activedirec.sh” or “bash_qolveevgclr.sh”, consist of a URL pointing to Amazon S3 buckets to obtain and operate a next-phase disk image (DMG) file to the compromised endpoint.
“The ongoing development of this malware displays that its authors keep on to keep on being energetic, making an attempt to arrive at as numerous users as probable,” the researchers stated.
Discovered this write-up interesting? Observe THN on Facebook, Twitter and LinkedIn to study more unique material we submit.
Some areas of this posting are sourced from:
thehackernews.com


 Are You Investing in Securing Your Data in the Cloud?
Are You Investing in Securing Your Data in the Cloud?