Times soon after Microsoft, Secureworks, and Volexity get rid of mild on a new spear-phishing activity unleashed by the Russian hackers who breached SolarWinds IT administration software program, the U.S. Department of Justice (DoJ) Tuesday said it intervened to get control of two command-and-control (C2) and malware distribution domains used in the marketing campaign.
The cour-approved area seizure took spot on Might 28, the DoJ said, adding the action was aimed at disrupting the threat actors’ comply with-on exploitation of victims as perfectly as block their capacity to compromise new systems. The office, having said that, cautioned that the adversary may well have deployed further backdoor accesses in the interim interval involving when the initial compromises transpired, and the seizures took area past 7 days.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“[The] action is a ongoing demonstration of the Department’s commitment to proactively disrupt hacking action prior to the conclusion of a criminal investigation,” reported Assistant Lawyer Typical John C. Demers for the Justice Department’s Countrywide Security Division. “Law enforcement continues to be an integral portion of the U.S. government’s broader disruption efforts in opposition to malicious cyber-enabled functions, even prior to arrest, and we will continue on to assess all probable prospects to use our one of a kind authorities to act towards this sort of threats.”
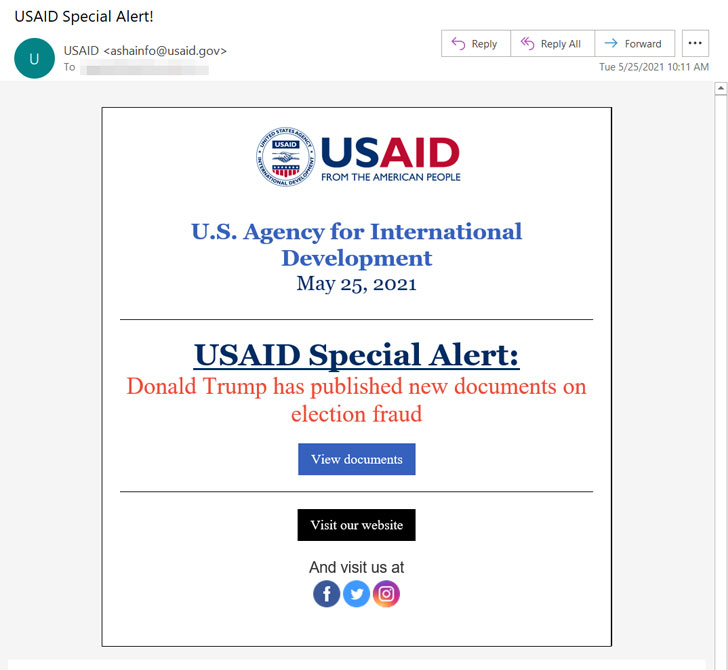
The two domains in dilemma — theyardservice[.]com and worldhomeoutlet[.]com — were being applied to connect and management a Cobalt Strike beacon known as NativeZone that the actors implanted on the target networks. The wide-scale marketing campaign, which was detected on May perhaps 25, leveraged a compromised USAID account at a mass email marketing and advertising organization identified as Consistent Contact to send phishing emails to approximately 3,000 email accounts at far more than 150 various corporations.
The moment the recipients clicked on the embedded connection in the email concept, a sub-area of theyardservice[.]com was employed to attain an initial foothold into the target device, exploiting to retrieve the Cobalt Strike backdoor to preserve persistent presence and possibly provide supplemental payloads. “The actors’ instance of the Cobalt Strike instrument obtained C2 communications through other subdomains of theyardservice[.]com, as effectively as the area worldhomeoutlet[.]com,” the DoJ said.
Microsoft attributed the ongoing intrusions to the Russian risk actor it tracks as Nobelium, and by the broader cybersecurity neighborhood under the monikers APT29, UNC2452 (FireEye), SolarStorm (Unit 42), StellarParticle (Crowdstrike), Dark Halo (Volexity), and Iron Ritual (Secureworks).
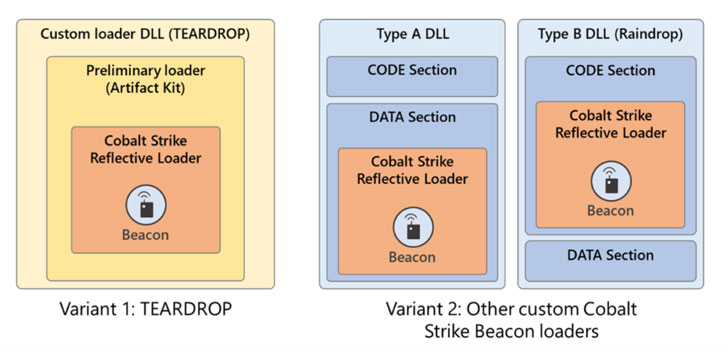
The company has because identified a few extra exceptional items of malware applied in the an infection chain, particularly BoomBox, EnvyScout, and VaporRage, incorporating to the attackers’ increasing arsenal of hacking tools such as Sunburst, Sunspot, Raindrop, Teardrop, GoldMax, GoldFinder, Sibot, and Flipflop, once once again demonstrating Nobelium’s operational security priorities when targeting perhaps high-risk and significant-visibility environments.
Whilst BoomBox is a downloader to attain a afterwards-phase payload from an actor-controlled Dropbox account, VaporRage is a shellcode loader used to down load, decode, and execute an arbitrary payload fully in-memory. EnvyScout, on the other hand, is a malicious dropper able of de-obfuscating and writing a malicious ISO file to disk and is sent in the variety of a malicious HTML attachment to spear-phishing e-mail.
The attacker’s observe of changing techniques various times more than the program of its newest marketing campaign underscores the common damage that could be inflicted on specific victims, federal government companies, non-governmental corporations, and private corporations, not to mention replicate on its pattern of setting up accessibility on one process or account and then working with it as a leaping-off place to get access to a lot of targets.
In “noticeably” differing from the SolarWinds hack by way of evolving its resources and tradecraft, the modus operandi enables a higher amount of stealth that will allow them to continue being undetected for extended periods of time, the researchers mentioned.
“Nobelium is an actor that operates with fast operational tempo, normally leveraging non permanent infrastructure, payloads, and approaches to obfuscate their actions,” Microsoft said. “This kind of design and style and deployment styles, which also involve staging of payloads on a compromised web page, hamper common artifacts and forensic investigations, allowing for special payloads to stay undiscovered.”
Found this posting interesting? Follow THN on Fb, Twitter and LinkedIn to read through additional unique information we publish.
Some sections of this report are sourced from:
thehackernews.com


 SolarWinds lawsuit claims private equity owners ‘sacrificed cybersecurity to boost short-term profits’
SolarWinds lawsuit claims private equity owners ‘sacrificed cybersecurity to boost short-term profits’