Bolstering password insurance policies in your corporation is an important component of a robust cybersecurity method. Cybercriminals are utilizing compromised accounts as just one of their favorite methods to infiltrate small business-critical environments as we’ve viewed in new information, these attacks can be dangerous and financially impactful.
Regretably, account compromise is a very effective attack approach and calls for significantly fewer energy than other attack vectors.
One particular of the essential forms of password defense suggested by noted cybersecurity requirements is breached password detection. Hackers usually use recognized breached password lists in credential stuffing or password spraying attacks.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Right here are some critical criteria to look at when your sysadmins are assessing breached password safety answers.
Breached password suggestions
In the last handful of several years, password security recommendations have progressed earlier the classic recommendations with regards to password security.
Firms have used Microsoft Energetic Directory for a long time to carry out password insurance policies in the firm. Common Energetic Listing password procedures contain nominal password configuration configurations.
Underneath is an example of the options presented with a regular Energetic Listing Password Plan:
- Implement password heritage
- Optimum password age
- Least password age
- Least password size
- Minimum amount password size audit
- Password ought to fulfill complexity demands
- Store password using reversible encryption
By default, Active Directory Password Procedures do not involve a option to employ breached password defense.
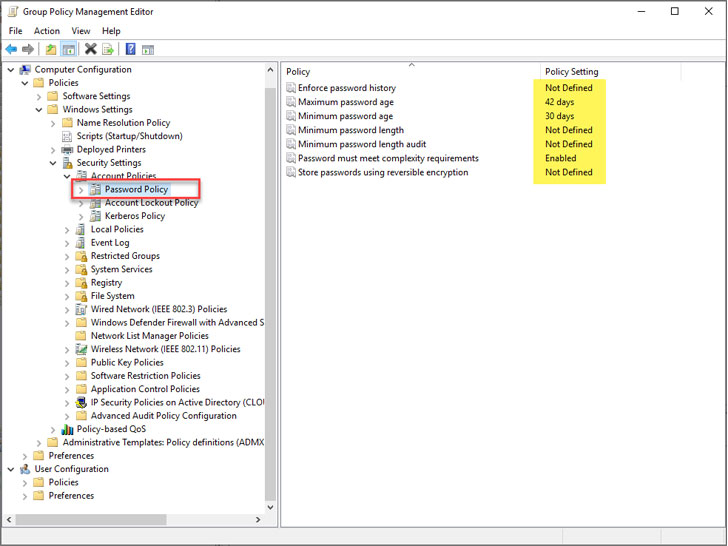 Energetic Listing Password Plan settings
Energetic Listing Password Plan settings
Why is it crucial for organizations to get started thinking about breached password security? Let us appear at most effective practice recommendations from primary authorities in cybersecurity direction.
New password coverage suggestions
As mentioned, standard password guidelines created utilizing Lively Directory are constrained in characteristics and abilities. These make it possible for developing basic password policies with normal size, complexity, age, and other specifications. However, there is no way to use native features to employ breached password safety.
Even though there is a suggests for applying a password filter .dll in Energetic Directory to provision password dictionary security, this is a manual procedure relying on the enhancement of customized password filter .dll information.
New password plan guidance from major cybersecurity authorities this kind of as the National Institute of Criteria and Technology (NIST) endorse breached password security. The NIST Unique Publication 800-63B SP 800-63B Area 5.1.1.2 paragraph 9 states:
“Verifiers Need to NOT impose other composition rules (e.g., necessitating mixtures of various character sorts or prohibiting consecutively recurring figures) for memorized techniques. Verifiers Need to NOT have to have memorized strategies to be modified arbitrarily (e.g., periodically). However, verifiers SHALL pressure a modify if there is evidence of compromise of the authenticator.”
Essentially, NIST’s steerage endorses that companies need to power a password change if there is proof of a breach. For enterprises to have evidence of a password breach, they must have a way to observe the password landscape for breached passwords. In addition to checking for passwords to turn out to be breached, as customers pick new passwords, the new password options want to be checked.
Assessing breached password detection expert services
Breached password detection is a proposed most effective practice for an further layer of cyberattack prevention. Contemplate the subsequent functions as should-haves to pay out near notice to when choosing a remedy:
An important consideration organizations need to have to make when selecting a third-party breached password answer is deployment simplicity. Seem for options that are very easily deployed employing present Active Directory infrastructure. Methods that are tricky to deploy will probable direct to configuration issues and problems with implementation and time to benefit. Glance for alternatives that make use of current Energetic Listing infrastructure alongside with Group Plan that allows speedily generating use of existing policies and infrastructure.
1 — Proactive checking
One of the important needs for breached password defense is proactive checking. Companies will need a remedy that checks a password throughout the password set operation and proactively displays the password landscape to obtain passwords that may well turn out to be breached. This performance allows to make certain passwords that may possibly not be breached during development, but become breached later on, are correctly identified and can be remediated.
2 — Proactive password adjustments
Dovetailing into the proactive checking of breached passwords in the environment, companies will need to glimpse for a breached password protection alternative that proactively requires conclusion-buyers to adjust their password if these turn out to be breached. This feature will help ensure any passwords that develop into breached in the surroundings are remediated as immediately as probable.
3 — Breached password database dimension
Maintain in brain that all breached password safety expert services are not equivalent in the amount of breached passwords checked. Breached password databases may change in between distinctive services. The more extensive the breached password databases, the greater for preserving towards breached passwords. If the quantity of breached passwords isn’t transparently communicated, talk to the vendor straight how numerous are integrated in their backend lists.
4 — Integration with current Energetic Directory password insurance policies
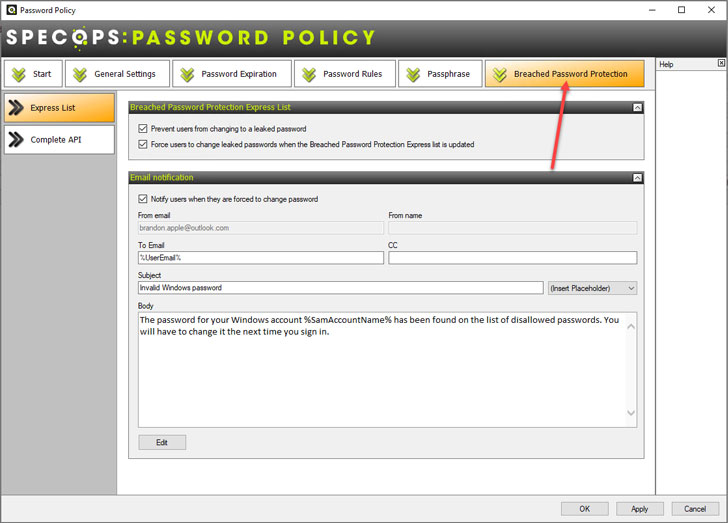 Specops Breached Password Safety
Specops Breached Password Safety
Look for a breached password safety resolution that can combine with existing Lively Listing password insurance policies. It means you can leave GPO assignments in location that assign many password guidelines to specific end users and will support to reduce “reinventing the wheel.”
Specops Breached Password Safety
The Specops Password Policy solution makes it possible for companies to have highly effective breached password protection as aspect of the environment’s password security. Features contain all the top specifications, like:
Making use of Specops Password Coverage with Breached Password Safety, you can very easily rollout breached password security using GPO-centered Energetic Listing Password Guidelines that are presently in put.
To delve into the Specops Password Plan with Breached Password Defense, get started a free of charge trial at any time.
Found this write-up attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to study more distinctive information we post.
Some sections of this posting are sourced from:
thehackernews.com

 Weekly threat roundup: Windows, Chrome, VMware
Weekly threat roundup: Windows, Chrome, VMware