Cybersecurity researchers right now uncovered a vast-ranging fraud targeting cryptocurrency customers that started as early as January final year to distribute trojanized programs to set up a previously undetected distant accessibility software on goal systems.
Identified as ElectroRAT by Intezer, the RAT is created from ground-up in Golang and made to target several functioning techniques these as Windows, Linux, and macOS.
The applications are developed utilizing the open-resource Electron cross-system desktop app framework.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“ElectroRAT is the most up-to-date case in point of attackers making use of Golang to produce multi-platform malware and evade most antivirus engines,” the scientists said.
“It is typical to see several information and facts stealers striving to acquire personal keys to access victims wallets. Nonetheless, it is uncommon to see tools composed from scratch and focusing on multiple operating techniques for these uses.”
The marketing campaign, initial detected in December, is believed to have claimed in excess of 6,500 victims dependent on the selection of one of a kind site visitors to the Pastebin internet pages made use of to identify the command and management (C2) servers.
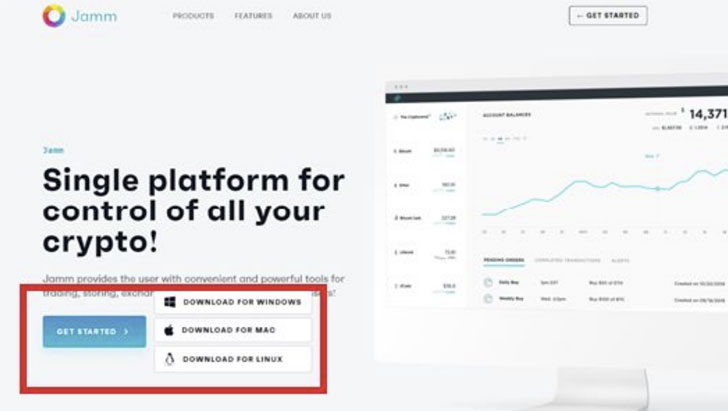
“Operation ElectroRAT” concerned the attackers creating three different tainted apps — every with a Windows, Linux, Mac variation — two of which pose as cryptocurrency trade management purposes by the identify of “Jamm” and “eTrade,” though a 3rd app called “DaoPoker” masquerades as a cryptocurrency poker system.
Not only are the malicious apps hosted on web-sites crafted precisely for this campaign, but the solutions are also advertised on Twitter, Telegram, and authentic cryptocurrency and blockchain-connected message boards these types of as “bitcointalk” and “SteemCoinPan” in an try to lure unsuspecting end users into downloading the tainted apps.
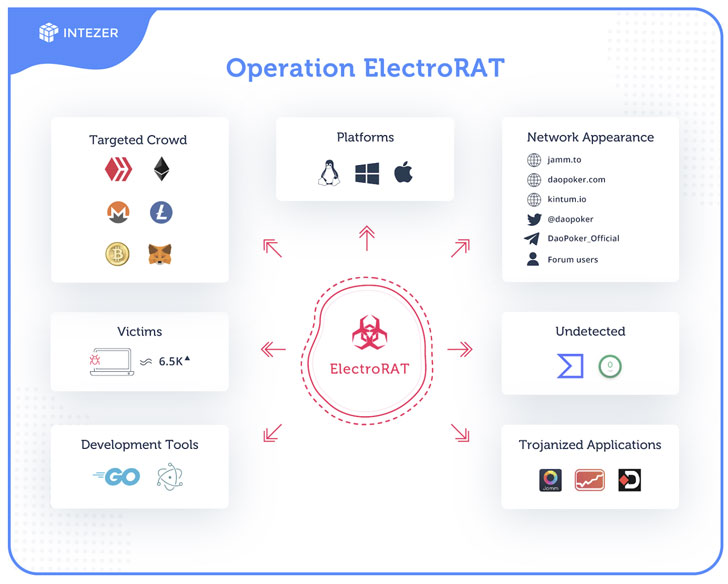
Once put in, the application opens a harmless-seeking user interface when in actuality, the ElectroRAT runs concealed in the track record as “mdworker,” which comes with intrusive capabilities to capture keystrokes, choose screenshots, upload files from disk, down load arbitrary documents, and execute malicious instructions received from the C2 server on the victim’s machine.
Curiously, an assessment of the Pastebin pages — which ended up revealed by a person named “Execmac” as early as January 8, 2020 — and these posted by the similar consumer prior to the campaign found C2 servers applied in conjunction with Windows malware like Amadey and KPOT, suggesting the attackers have pivoted from using effectively-recognized trojans to a new RAT able of concentrating on several operating techniques.
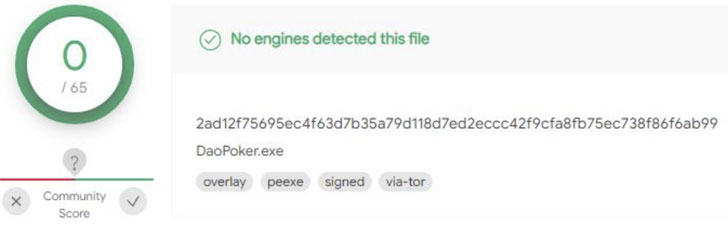
“Yet another motivating factor is this is an not known Golang malware, which has authorized the campaign to fly beneath the radar for a year by evading all antivirus detections,” the scientists said.
Users who have fallen target to this marketing campaign are urged to get rid of the system, delete all information linked to the malware, transfer the resources to a new wallet, and modify their passwords.
Discovered this short article fascinating? Stick to THN on Facebook, Twitter and LinkedIn to study a lot more exceptional material we put up.
Some areas of this article are sourced from:
thehackernews.com


 ElectroRAT Drains Cryptocurrency Wallet Funds of Thousands
ElectroRAT Drains Cryptocurrency Wallet Funds of Thousands