Graphic supply: z3r00t
The U.S. Cybersecurity and Infrastructure Security Company on Monday extra two security flaws, like the lately disclosed distant code execution bug affecting Zyxel firewalls, to its Regarded Exploited Vulnerabilities Catalog, citing proof of lively exploitation.
Tracked as CVE-2022-30525, the vulnerability is rated 9.8 for severity and relates to a command injection flaw in pick versions of the Zyxel firewall that could permit an unauthenticated adversary to execute arbitrary commands on the underlying working method.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Impacted gadgets incorporate –
- USG FLEX 100, 100W, 200, 500, 700
- USG20-VPN, USG20W-VPN
- ATP 100, 200, 500, 700, 800, and
- VPN series
The issue, for which patches have been launched by the Taiwanese business in late April (ZLD V5.30), became general public awareness on Might 12 adhering to a coordinated disclosure process with Fast7.
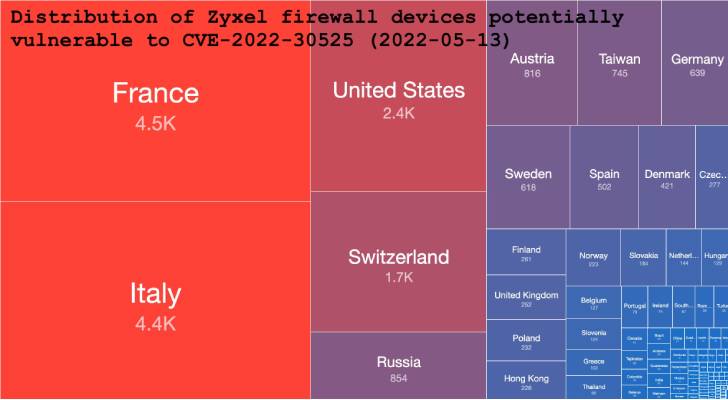 Supply: Shadowserver
Supply: Shadowserver
Just a working day afterwards, the Shadowserver Basis stated it began detecting exploitation attempts, with most of the susceptible appliances found in France, Italy, the U.S., Switzerland, and Russia.

Also extra by CISA to the catalog is CVE-2022-22947, another code injection vulnerability in Spring Cloud Gateway that could be exploited to make it possible for arbitrary distant execution on a remote host by usually means of a specifically crafted request.
The vulnerability is rated 10 out of 10 on the CVSS vulnerability scoring technique and has given that been resolved in Spring Cloud Gateway variations 3.1.1 or later on and 3..7 or afterwards as of March 2022.
Discovered this report exciting? Comply with THN on Fb, Twitter and LinkedIn to examine far more special content material we submit.
Some pieces of this report are sourced from:
thehackernews.com

 US Manufacturing Giant Parker Hit by Conti Ransomware Gang
US Manufacturing Giant Parker Hit by Conti Ransomware Gang