Every single SaaS application user and login is a prospective threat whether or not it truly is bad actors or prospective disgruntled former associates, id administration and entry command is very important to prevent unwanted or mistaken entrances to the organization’s details and techniques.
Because enterprises have thousands to tens of countless numbers of users, and hundreds to countless numbers of different applications, making certain every entrance point and consumer job is secure is no quick feat. Security groups will need to check all identities to be certain that consumer action fulfills their organization’s security guidelines.
Identity and Obtain Administration (IAM) methods administer user identities and regulate obtain to organization means and purposes. As identities turned the new perimeter, making absolutely sure this spot is ruled by the security staff is important.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Gartner has recently named a new security discipline named Identity Menace Detection and Response (ITDR) that incorporates detection mechanisms that examine suspicious posture modifications and things to do, and responds to attacks to restore the integrity of the identity infrastructure.
ITDR incorporates solid SaaS Security IAM Governance methodologies and very best methods that are identified in SaaS Security Posture Administration alternatives (SSPM), enabling security groups to attain ongoing and consolidated visibility of consumer accounts, permissions, and privileged pursuits across the SaaS stack, this sort of as:
- Determining who is accessing what and when, and with the ideal degrees of privileges
- Forensics similar to user steps, focusing on privileged consumers
- Roles’ continuous and automated discovery and consolidation
- Job appropriate-sizing by revoking unnecessary or unwanted access
Whether you are a CISO, IT or on the Governance, Risk and Compliance (GRC) group, this post will include the part of Identification and Accessibility Management Governance as element of the organization’s SaaS security application.
Learn how to apply IAM governance in your SaaS Security.
What is IAM Governance
IAM Governance permits the security staff to act upon arising issues by offering frequent checking of the company’s SaaS Security posture as nicely as its implementation of entry control.
There are a couple critical avoidance domains wherever an SSPM, like Adaptive Shield, can control Identity and Accessibility Management Governance: 1) Misconfigurations 2) Vulnerabilities 3) Publicity.
Misconfigurations
IAM controls have to have to be adequately configured on a constant basis. The IAM configurations ought to be monitored for any suspicious variations and assure that the appropriate techniques are taken to examine and remediate when suitable.
For instance, an corporation can permit MFA throughout the business and not demand it. This hole in policy enforcement can leave the business at risk — and an SSPM can notify the security group about this hole.
Vulnerabilities
The SSPM solution can make use of patching or compensating controls to deal with normally exploited vulnerabilities in the identification infrastructure these types of as the SaaS user’s device. For case in point, a privileged CRM user can current a higher risk to the firm if their machine is vulnerable. To remediate potential threats that stem from devices, security teams need to have to be in a position to correlate SaaS app people, roles, and permissions with their linked devices’ hygiene. This conclude-to-stop tactic allows a holistic zero-trust solution to SaaS security.
Another critical vulnerability stems from authentication protocols that the password entry is confined to a solitary-factor authentication technique, this sort of as with legacy protocols like IMAP, POP, SMTP and Messaging API (MAPI). An SSPM can establish where by these protocols are in spot across the organization’s SaaS stack.
Publicity
The SSPM helps to cut down the attack area by figuring out and mitigating destinations of exposure. For illustration, removing unwanted or abnormal privileges or enabling an external admin for a enterprise-critical application. (See figure 1.)
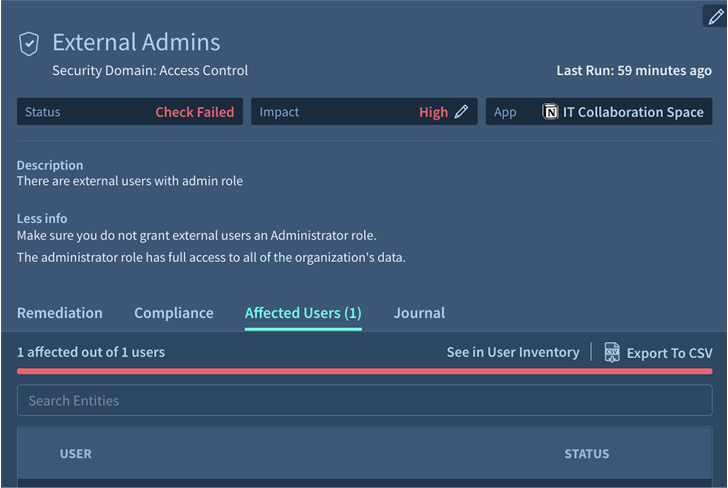 Figure 1. Adaptive Shield’s security test for exterior admins
Figure 1. Adaptive Shield’s security test for exterior admins
Also, 3rd party application access, also identified as SaaS-to-SaaS obtain can go away an business exposed. Consumers connect 1 app to another application to possibly deliver improved features or user’s information (e.g contacts, documents, calendar, and many others). This connection boosts workflow efficiency and as a outcome, employees’ workspaces are linked to multitudes of different apps. However, the security team is most usually in the dark about which apps have been linked to their organization’s ecosystem, unable to keep track of or mitigate any threats.
Wrap-Up
IAM is a method for hardening access regulate, whereas IAM Governance in SSPMs provide continuous monitoring of these options to make certain security teams have total visibility and manage of what’s occurring in the domain.
Get a stay demo to discover how to gain Id and Accessibility Governance for your SaaS stack.
Found this short article attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to go through a lot more special information we post.
Some components of this short article are sourced from:
thehackernews.com


 OPERA1ER APT Hackers Targeted Dozens of Financial Organizations in Africa
OPERA1ER APT Hackers Targeted Dozens of Financial Organizations in Africa