A new variant of the Android banking trojan named Xenomorph has surfaced in the wild, the most up-to-date findings from ThreatFabric reveal.
Named “Xenomorph 3rd generation” by the Hadoken Security Team, the danger actor at the rear of the procedure, the current edition comes with new features that allow it to conduct economical fraud in a seamless way.
“This new edition of the malware provides a lot of new abilities to an presently function-abundant Android banker, most notably the introduction of a incredibly intensive runtime engine run by Accessibility products and services, which is utilized by actors to put into action a total ATS framework,” the Dutch security business reported in a report shared with The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Xenomorph very first arrived to light-weight a 12 months in the past in February 2022, when it was observed to goal 56 European financial institutions by means of dropper applications printed on the Google Engage in Keep.
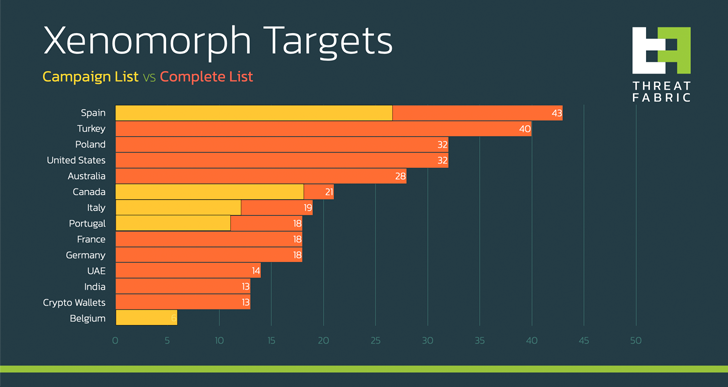
In distinction, the most up-to-date iteration of the banker – which has a committed web-site marketing its capabilities – is designed to concentrate on more than 400 banking and money establishments, which include several cryptocurrency wallets.
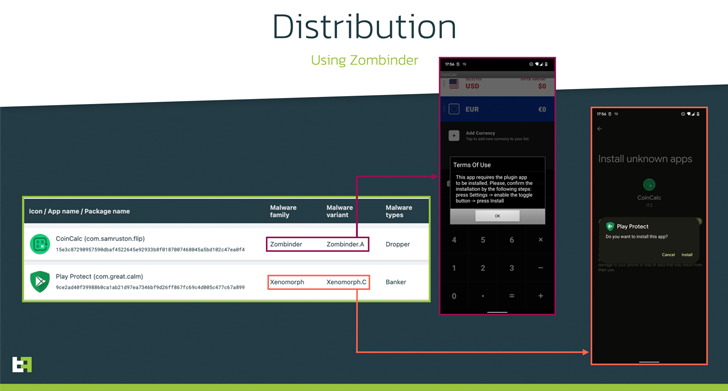
ThreatFabric claimed it detected samples dispersed by means of Discord’s Content material Delivery Network (CDN), a procedure that has witnessed a surge since 2020. Two of the Xenomorph-laced apps are shown below –
- Participate in Protect (com.great.relaxed)
- Participate in Defend (meritoriousness.mollah.presser)
“Xenomorph v3 is deployed by a Zombinder app ‘bound’ to a authentic currency converter, which downloads as an ‘update’ an application posing as Google Shield,” ThreatFabric stated.
Zombinder refers to an APK binding company marketed on the dark web considering that March 2022, wherein the malware is delivered by way of trojanized versions of legit applications. The providing has considering that been shut down.
Targets of the hottest campaign go further than its European target (i.e., Spain, Italy, and Portugal) to consist of Belgian and Canadian money entities.
WEBINARDiscover the Concealed Risks of Third-Party SaaS Applications
Are you aware of the challenges related with third-party app entry to your company’s SaaS applications? Sign up for our webinar to learn about the kinds of permissions being granted and how to minimize risk.
RESERVE YOUR SEAT
Xenomorph, like banking malware, is known to abuse Accessibility Services to conduct fraud through overlay attacks. It also packs in capabilities to routinely entire fraudulent transactions on infected products, a method identified as Automatic Transfer Program (ATS).
With banking companies going absent from SMS for two-factor authentication (2FA) to authenticator applications, the Xenomorph trojan incorporates an ATS module that will allow it to launch the application and extract the authenticator codes.
The Android malware even further offers of cookie-stealing features, enabling the menace actors to accomplish account takeover attacks.
“With these new attributes, Xenomorph is now able to fully automate the whole fraud chain, from an infection to funds exfiltration, earning it 1 of the most innovative and harmful Android Malware trojans in circulation,” the company said.
Found this report appealing? Follow us on Twitter and LinkedIn to study extra distinctive information we write-up.
Some pieces of this report are sourced from:
thehackernews.com


 UK’s New Privacy Bill Could Mean More Work for Firms
UK’s New Privacy Bill Could Mean More Work for Firms