Cybersecurity researchers have learned an ongoing phishing marketing campaign that tends to make use of a unique attack chain to deliver the XWorm malware on focused systems.
Securonix, which is monitoring the action cluster under the name MEME#4CHAN, explained some of the attacks have primarily targeted production companies and health care clinics found in Germany.
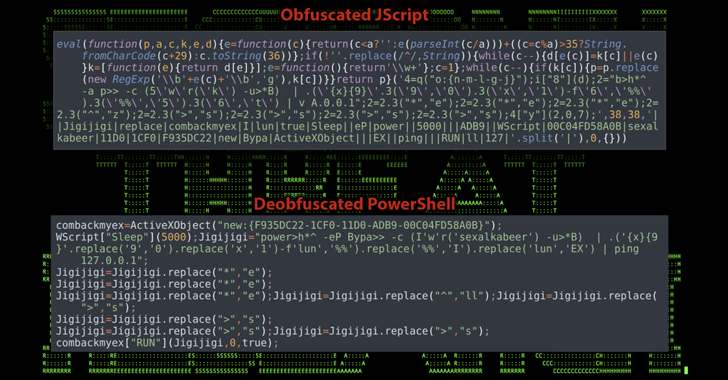
“The attack campaign has been leveraging rather uncommon meme-crammed PowerShell code, adopted by a heavily obfuscated XWorm payload to infect its victims,” security scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov claimed in a new assessment shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The report builds on latest results from Elastic Security Labs, which exposed the threat actor’s reservation-themed lures to deceive victims into opening malicious documents capable of delivering XWorm and Agent Tesla payloads.

The attacks begin with phishing attacks to distribute decoy Microsoft Term paperwork that, in its place of employing macros, weaponize the Follina vulnerability (CVE-2022-30190, CVSS score: 7.8) to drop an obfuscated PowerShell script.
From there, the threat actors abuse the PowerShell script to bypass Antimalware Scan Interface (AMSI), disable Microsoft Defender, establish persistence, and in the long run launch the .NET binary containing XWorm.
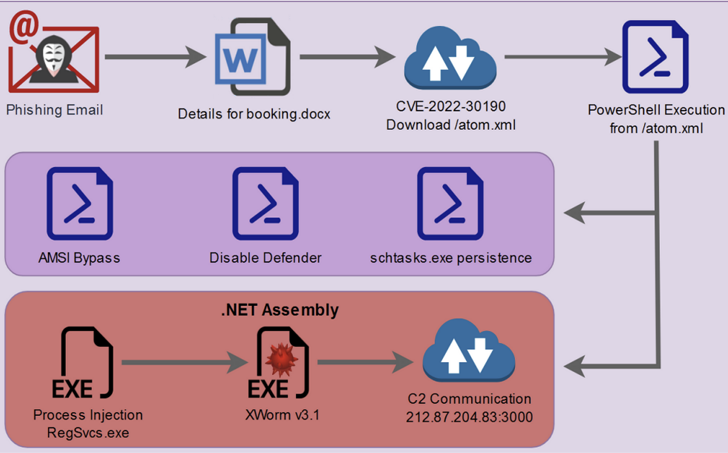
Curiously, just one of the variables in the PowerShell script is named “$CHOTAbheem,” which is probably a reference to Chhota Bheem, an Indian animated comedy adventure tv sequence.
“Based on a quick look at, it seems that the unique or team responsible for the attack could have a Middle Japanese/Indian history, despite the fact that the remaining attribution has not however been confirmed,” the scientists told The Hacker News, pointing out that these kinds of key phrases could also be made use of as a cover.
XWorm is a commodity malware that’s advertised for sale on underground community forums and will come with a huge vary of functions that permits it to siphon delicate data from contaminated hosts.
Upcoming WEBINARLearn to Stop Ransomware with True-Time Safety
Be part of our webinar and understand how to quit ransomware attacks in their tracks with actual-time MFA and service account protection.
Save My Seat!
The malware is also a Swiss Military knife in that it can conduct clipper, DDoS, and ransomware operations, spread by means of USB, and drop extra malware.
The exact origins of the menace actor are at present unclear, though Securonix said the attack methodology shares artifacts very similar to that of TA558, which has been observed placing the hospitality business in the earlier.
“Nevertheless phishing e-mails rarely use Microsoft Workplace documents given that Microsoft manufactured the decision to disable macros by default, right now we are seeing proof that it is however important to be vigilant about malicious document information, particularly in this circumstance in which there was no VBscript execution from macros,” the scientists stated.
Discovered this post exciting? Comply with us on Twitter and LinkedIn to browse a lot more exceptional articles we submit.
Some parts of this post are sourced from:
thehackernews.com

 PaperCut Software Flaw Sparks Ransomware Attacks, CISA Warns
PaperCut Software Flaw Sparks Ransomware Attacks, CISA Warns