A zero-click distant code execution (RCE) bug in Microsoft Groups desktop applications could have allowed an adversary to execute arbitrary code by just sending a specially-crafted chat information and compromise a target’s process.
The issues had been noted to the Windows maker by Oskars Vegeris, a security engineer from Evolution Gaming, on August 31, 2020, just before they were being dealt with at the stop of Oct.
“No person conversation is necessary, exploit executes on viewing the chat concept,” Vegeris described in a specialized generate-up.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The consequence is a “full decline of confidentiality and integrity for conclude end users — access to personal chats, data files, inside network, non-public keys and personal facts outdoors MS Teams,” the researcher additional.
Worse, the RCE is cross-platform — affecting Microsoft Teams for Windows (v1.3.00.21759), Linux (v1.3.00.16851), macOS (v1.3.00.23764), and the web (teams.microsoft.com) — and could be created wormable, indicating it could be propagated by instantly reposting the malicious payload to other channels.
This also signifies the exploit can be handed on from a person account to a full group of people, therefore compromising an whole channel.
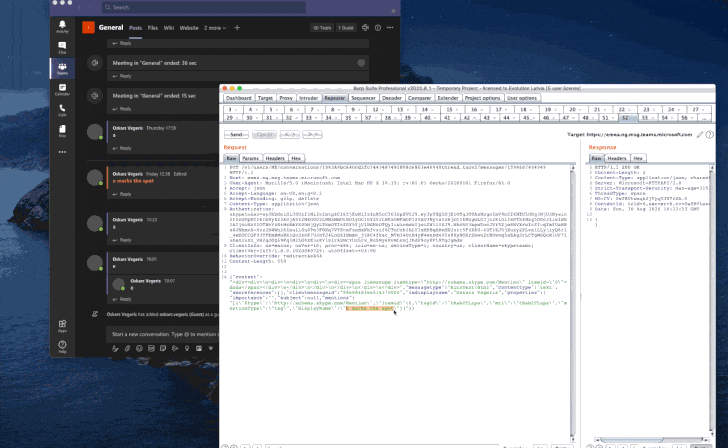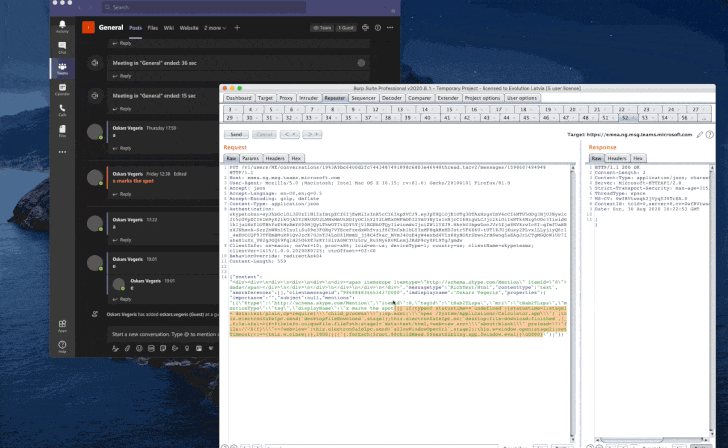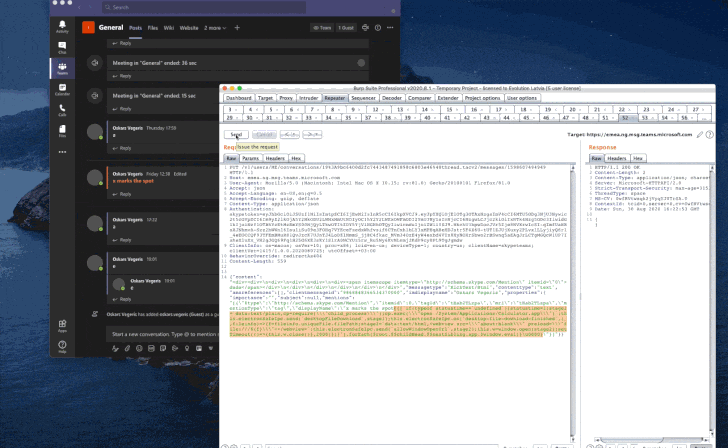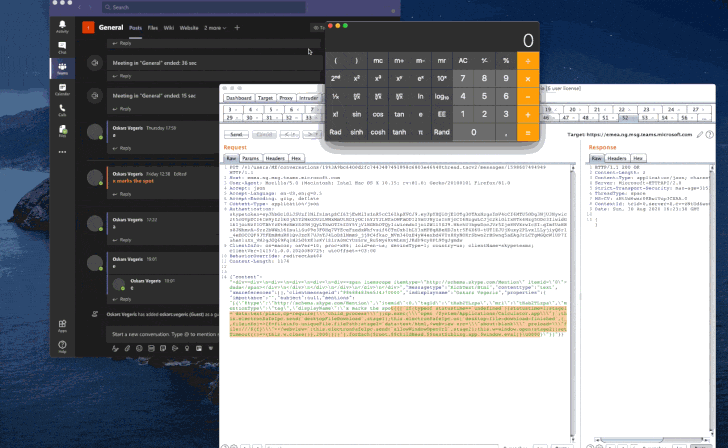
To accomplish this, the exploit chain strings jointly a cross-web site scripting (XSS) flaw existing in the Teams ‘@mentions’ operation and a JavaScript-based mostly RCE payload to submit a harmless-on the lookout chat information made up of a person mention either in the type of a direct concept or to a channel.
Simply just browsing the chat at the recipient’s end sales opportunities to the execution of the payload, allowing it to be exploited to log users’ SSO tokens to community storage for exfiltration and execute any command of the attacker’s preference.
This is not the 1st time these RCE flaws had been observed in Groups and other organization-centered messaging applications.
Chief amongst them is a separate RCE vulnerability in Microsoft Teams (CVE-2020-17091) that the enterprise patched as element of its November 2020 Patch Tuesday previous month.
Before this August, Vegeris also disclosed a critical “wormable” flaw in Slack’s desktop variation that could have allowed an attacker to consider around the technique by merely sending a malicious file to a further Slack person.
Then in September, networking devices maker Cisco patched a similar flaw in its Jabber video conferencing and messaging app for Windows that, if exploited, could make it possible for an authenticated, remote attacker to execute arbitrary code.
Observed this write-up fascinating? Abide by THN on Fb, Twitter and LinkedIn to read through much more exclusive material we submit.
Some sections of this article are sourced from:
thehackernews.com

 NSA Warns Russian Hacker Exploiting VMware Bug to Breach Corporate Networks
NSA Warns Russian Hacker Exploiting VMware Bug to Breach Corporate Networks