I recently hopped on the Lookout podcast to talk about digital non-public networks (VPNs) and how they have been extended outside of their first use situation of connecting remote laptops to your corporate network. Even in this new world in which people are employing personal products and cloud applications, VPN proceeds to be the go-to remedy for distant accessibility and cloud entry. Just after my discussion with Hank Schless, I was impressed to set some additional ideas about VPN on paper.
When most businesses have been compelled to change to remote operate past calendar year, they necessary a fast-correct remedy that would permit their remote personnel to access function assets securely. For quite a few, this resolution arrived in the form of VPNs. Having said that, VPNs ended up not made for the bring your have system (BYOD) and cloud app use circumstances.
While VPNs are able to present distant obtain, it might arrive as a shock that they drop brief when it arrives to security. This is simply because VPNs had been crafted for when only a compact part of your workforce wanted to perform from home. They also place much too a lot have faith in on the system and the consumer. But now, as do the job from anywhere continues, it is important to rethink how to give entry for your complete firm in a secure manner.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
What are the worries of a remote-to start with workforce?
When they first debuted twenty several years back, VPNs were being the de-facto process for connecting distant workers to an organization’s info center when laptops turned popular. Back again then, personal computers nevertheless used modems and services like iPass for connectivity. A VPN ran about prime of providers like iPass to build a “private network” and preserve the transmission secure.
But given that then, the technological landscape has modified dramatically. In a number of approaches, they were created to address yesterday’s difficulties.
Now, the widespread adoption of cloud applications usually means the way we store and obtain get the job done information is fully various. On any specified working day, I will link to an internal progress procedure, obtain files on Google Workspace, send Slack messages to coworkers and use Zoom to go to conferences. I can accomplish all of these equally very easily on my smartphone and my laptop.
Quite a few Lookout prospects might have a identical working experience that also includes accessing programs on AWS or Azure, these types of as SAP S/4HANA. As we get the job done remotely, we have turn out to be accustomed to seamlessly accessing what we need to have wherever it is and to perform from any product of our deciding on.
A different sizeable challenge introduced on by this new atmosphere is that businesses do not have the necessary visibility into their complex IT environments.
Unlike back again in the working day, wherever you’d only be employing work-issued units on corporation-managed networks, staff members are accessing do the job assets using equipment, networks and program that your IT staff has no management more than or may even be unaware of. This has significantly elevated the attack area of your group.
Why are VPNs insufficient for the modern perform ecosystem?
One of the largest issues with VPNs is that they give full network accessibility to whoever and whatever is linked. And it really is not just the device related, anything which is on that device’s network is also supplied access. So whether it is really a piece of malware, or a compromised account, there is certainly practically nothing to quit them from moving laterally across your infrastructure and resulting in harm.
VPNs also have a terrible keep track of file when it comes to consumer encounter. When direct accessibility to the cloud is out there almost everywhere, anticipating your staff members to initially indication into a VPN to go to these cloud apps places a highway bump into their workflows. Assume of it like forcing someone to vacation from Boston to New York City by using Los Angeles — inefficient. If you’ve ever expert sluggish page loading times or snail-paced downloads even though on a VPN, then it is probable due to your targeted traffic getting pressured to get an inefficient route.
What’s the substitute?
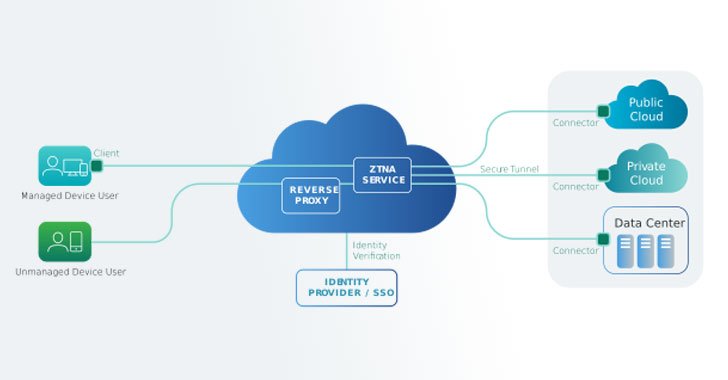
To tackle these new problems and for the motives mentioned earlier mentioned, VPNs don’t slash it when it comes to supplying your distant workers protected entry to what they have to have. Secure obtain systems like Zero Believe in network obtain (ZTNA) or cloud obtain security broker (CASB) select up exactly where VPNs go away off.
These protected accessibility provider edge (SASE) technologies give granular obtain to only the applications and info that your personnel want when continually checking user and unit habits to modify access dependent on risk dynamically. This signifies that the risk of lateral motion is substantially diminished, the connectivity concerning the user and the app is effective, and the security of the relationship goes very well past encrypting site visitors amongst two points.
ZTNA provides seamless relationship to your apps devoid of placing your facts at risk
Soon after all these many years of connecting your personnel to your group, they deserve their praise where by it truly is owing. But the troubles they were being created to deal with back then are no for a longer time pertinent. Your firm is now going through the challenge of enabling your personnel with the flexibility and overall flexibility to work with purposes in the cloud from anyplace whilst safeguarding your facts. Transferring absent from technology like VPNs to upcoming-era alternatives like ZTNA is a good commence.
Learn how you can augment your VPN deployment and safeguard your business by examining out the Lookout Protected Obtain Assistance Edge alternative.
Notice — This write-up is prepared and contributed by Sundaram Lakshmanan, CTO of SASE Products and solutions.
Identified this posting intriguing? Stick to THN on Facebook, Twitter and LinkedIn to study much more exceptional information we publish.
Some components of this write-up are sourced from:
thehackernews.com

 NCSC Cyber Essentials overhaul takes effect
NCSC Cyber Essentials overhaul takes effect