The North Korean-connected APT’s most recent campaign exhibits that it is shifting focus to goal the cryptocurrency and fiscal verticals.
The nation-condition danger operator Lazarus Team is getting tied to a current phishing campaign that specific admins at a cryptocurrency company through LinkedIn messages.
Researchers say that the just lately discovered a sequence of incident that have been aspect of a broader campaign focusing on corporations throughout the world by means of LinkedIn messages sent to targets’ personalized LinkedIn accounts. The goal of the campaign appears to be monetarily inspired, with the attackers harvesting qualifications important for accessing cryptocurrency wallets or on the net financial institution accounts.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Lazarus Group’s actions are a continued threat: the phishing campaign associated with this attack has been noticed continuing into 2020, raising the have to have for consciousness and ongoing vigilance amongst businesses functioning in the specific verticals,” stated researchers with F-Secure in a Tuesday article [PDF].
The attackers qualified procedure directors in an unnamed cryptocurrency organization with a phishing document, which was attached to a concept despatched to their personal LinkedIn accounts. The doc masqueraded as a authentic work ad for a job in a blockchain technology organization, which matched the employee’s capabilities, scientists mentioned.

As soon as the goal clicked on the malicious doc, the doc claimed to be protected by Standard Facts Security Regulation (GDPR) constraints, and that the consumer required to permit macros in Microsoft Term for even more accessibility. After the concentrate on enabled the macros, malicious embedded macro code would then execute. The macro in the document produces an LNK file that results in the execution of mshta.exe.
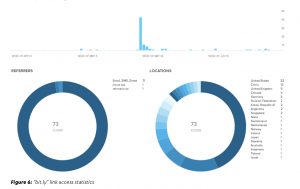
This then calls out to a “bit.ly” url created in early May possibly 2019, scientists mentioned. On further inspection of the hyperlink utilized in the phishing attack, researchers discovered that it was accessed 73 situations from at the very least 19 countries – together with the U.S., China and the Uk – foremost researchers to conclude that this is a “widely-targeted lure doc.”
The “bit.ly” website link then redirects to a domain that executes a VBScript to carry out checks on the host and gather even further facts, which is then sent to a next Command and Command (C2) area. This ultimately leads to the obtain and execution of a PowerShell script that retrieves a more payload from a third C2, researchers claimed.
 This payload ultimately downloads many primary implants on the victim’s technique, which have the talents to down load further information, decompress facts in memory, initiate C2 conversation, execute arbitrary commands, and steal qualifications from a number of sources (by using a personalized model of Mimikatz an open-source software that permits users to check out and conserve authentication credentials). The implants were also noticed becoming used to connect to the network backdoor implants on other focus on hosts, researchers stated.
This payload ultimately downloads many primary implants on the victim’s technique, which have the talents to down load further information, decompress facts in memory, initiate C2 conversation, execute arbitrary commands, and steal qualifications from a number of sources (by using a personalized model of Mimikatz an open-source software that permits users to check out and conserve authentication credentials). The implants were also noticed becoming used to connect to the network backdoor implants on other focus on hosts, researchers stated.
Scientists also designed note of different practices utilized by the APT to avoid detection. For instance, Lazarus Team disabled Windows Defender checking as one of their very first actions on each and every host they accessed. In spite of these makes an attempt to prevent detection, scientists observe that the big variety of commands executed by way of cmd.exe give blue groups “significant alternatives for detection.”
“One unique trait common across the the greater part of the commands executed by Lazarus Team was the appending of the string “2>&1″ to instructions which while utilised by some tooling should be anomalous when filtered by dad or mum little one procedure romantic relationship, and provide good detection possibilities,” they said.
Shift to Cryptocurrency
Lazarus Team, a.k.a. Hidden Cobra or APT 38, has been around considering that 2009. The APT has been linked to the highly destructive WannaCry attack that brought on thousands and thousands of bucks of economic harm in 2017, the SWIFT banking attacks, as well as the significant-profile attack against Sony Photographs Entertainment in 2014. Lazarus is also frequently evolving: In December, it was noticed hooking up with Trickbot operators, which run a powerful trojan that targets U.S. banking companies and other people. In May perhaps, it was seen adding macOS spyware to a two-issue authentication app and earlier in July, it added Magecart card-skimming code to its toolbag.
More not long ago it has debuted an sophisticated, multi-objective malware framework (MATA) that targets Windows, Linux and MacOS operating systems and has been linked to a recent pressure of ransomware, termed VHD.
However, this most recent campaign shows that the group is now also on the lookout to focus on companies in the financial and cryptocurrency verticals, scientists warn.
“It is F-Secure’s assessment that the group will continue to target companies in the cryptocurrency vertical although it continues to be these a rewarding pursuit, but may well also broaden to target source chain features of the vertical to raise returns and longevity of the campaign,” reported scientists.
It’s the age of distant performing, and firms are facing new and more substantial cyber-risks – whether or not it’s collaboration platforms in the crosshairs, evolving insider threats or issues with locking down a substantially broader footprint. Obtain out how to address these new cybersecurity realities with our complimentary Threatpost E-book, 2020 in Security: 4 Tales from the New Danger Landscape, introduced in conjunction with Forcepoint. We redefine “secure” in a get the job done-from-household world and offer compelling actual-environment greatest procedures. Click on listed here to download our Book now.


 Nearly Fifty percent of British isles IT Leaders Have Not Upgraded to Cloud Security
Nearly Fifty percent of British isles IT Leaders Have Not Upgraded to Cloud Security