CVEs or Program vulnerabilities contains only a element of security challenges in the IT security landscape. Attack surfaces are significant with quite a few security hazards that have to be dealt with equally as software package vulnerabilities to lower risk exposure and reduce cyberattacks at scale.
A software vulnerability is a weak spot in an operating program or application that can be exploited by an attacker to invade an IT network. When publicly disclosed, these software vulnerabilities are normally assigned a CVE identifier. CVE is a well-known term when referring to a vulnerability, and 50 to 60 CVEs are learned each and every day on average.
Evidently, vulnerabilities are rising quickly, hard IT security teams. On top of that, in excess of 40% of learned vulnerabilities have no CVE identifier assigned and can be conveniently exploited by cybercriminals. These vulnerability loopholes allow for unauthorized obtain to the network, resulting in ransomware and malware attacks.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
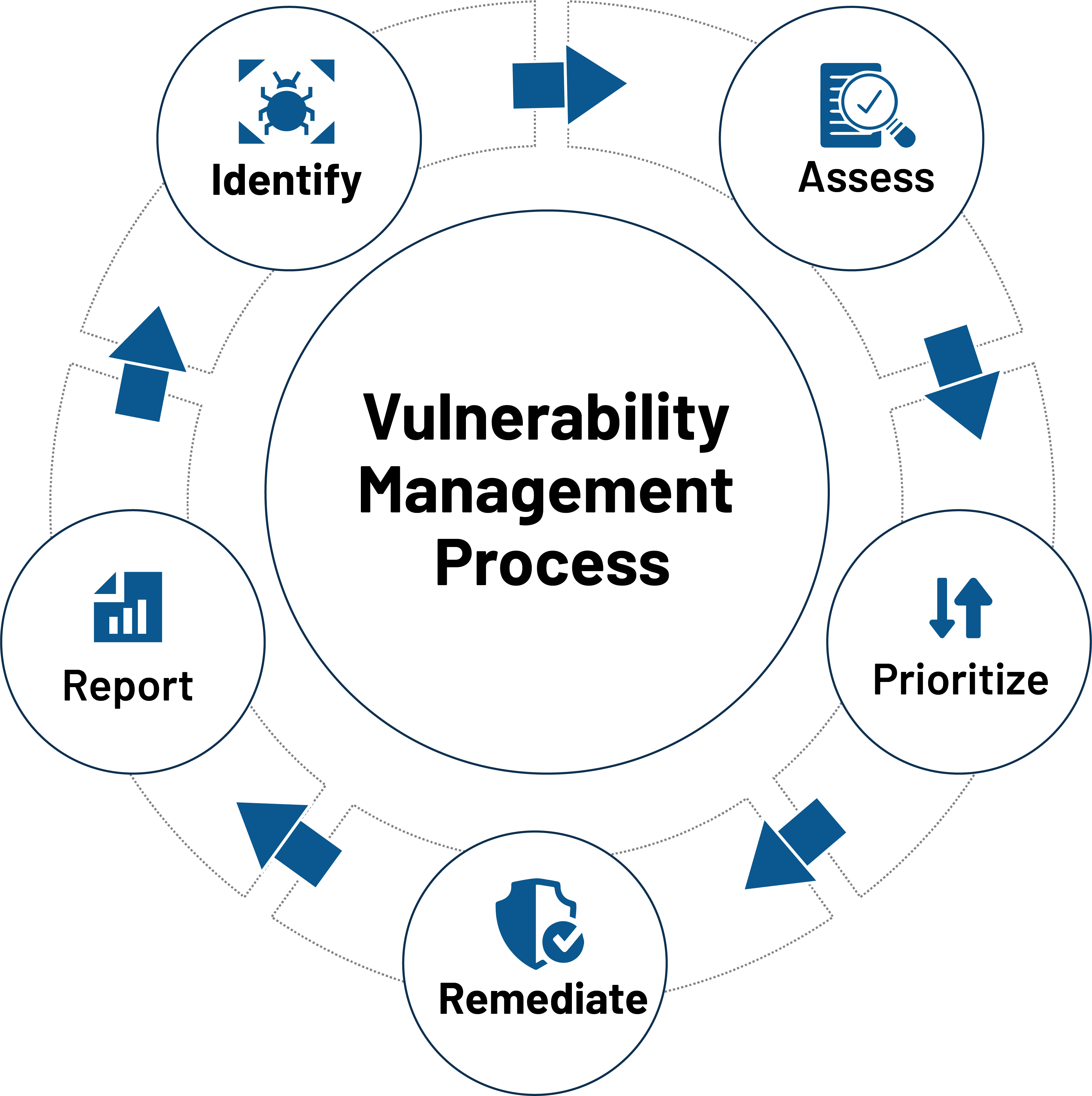
IT Security teams have to employ a seamless vulnerability management procedure to stop cyber attacks. They need to repeatedly establish the vulnerabilities in their network, assess them thoroughly, prioritize them based on their severity, remediate them with suitable patches, and report all the info for strategic assessment.
It is obvious that CVEs or software program vulnerabilities are a critical security loophole, but are these the only kind of vulnerabilities attackers’ glance out for? To respond to this, we have to have to rethink vulnerabilities from the standpoint of an entire attack surface.
Are Software Vulnerabilities the Only Vulnerability in the Attack Floor?
CVEs or software vulnerabilities lead only to a element of security threats in the IT vulnerability landscape. The attack surface includes a lot of vulnerabilities from a misconfigured firewall policy, unavailability of antivirus, unauthorized apps, lack of visibility over scheduled tasks, undesirable expert services and ports, concealed belongings, and publicly discoverable information to various security control deviations and anomalies.
All these vulnerabilities and security pitfalls are as threatening as a software program vulnerability and can simply open up gateways for an array of cyberattacks. IT security groups need to look over and above CVEs and computer software vulnerabilities and start out handling these security threats to achieve a potent security posture and overcome attacks.
Leading Security Risks in the IT Security Landscape
In this article are the major security pitfalls that are as threatening as a software program vulnerability and need to have to be deemed as a vulnerability in the IT security landscape.
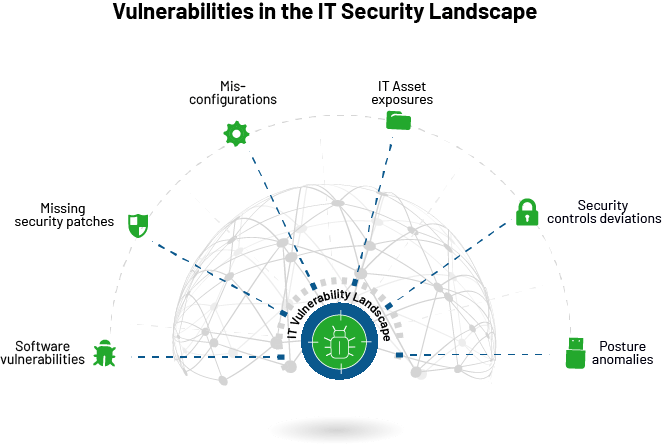
- Software program Vulnerabilities: Computer software vulnerabilities are an IT network’s most critical security pitfalls. Whilst they get a large amount of focus from security groups, they are nevertheless widespread in big quantities within a regular IT infrastructure. Whilst taking care of the other security threats, IT security teams should bring in a steady and automatic method to quickly detect and remediate software program vulnerabilities.
- Misconfigurations: Security misconfigurations are inaccurately configured configurations that leave an organization’s IT infrastructure at risk. Although security misconfigurations are not a section of an application or an operating program, they control the options that make programs and working systems run. For instance, a weak procedure password or weak encryption is a security misconfiguration that can open doorways for several attacks, which include brute pressure attacks.
- IT Asset Exposures: IT security teams need to have finish and ongoing visibility more than the IT infrastructure. Any destructive entry of IT assets will disrupt security to a big extent. For instance, applying unauthorized purposes or units will cause a substantial menace to an organization’s security, inviting attacks like info thefts. Similarly, shadow IT, finish-of-everyday living and close-of-support software, and unwanted ports and solutions must be determined in the network and labored on.
- Lacking security patches: Missing patches are one of the critical security threats in an IT network. A lot of attacks, which include the notorious WannaCry ransomware, ended up owing to a lacking patch that was not used on time. Apart from repairing vulnerabilities, patches enjoy an important function in trying to keep methods stable, up-to-day, and safe from cyberattacks. It is vital to patch all running programs and third-party purposes continuously to safeguard your network from probable attacks.
- Deviation in security controls: A lot of security controls need to be implemented in a gadget for sufficient security. If these security controls are not configured adequately, they could possibly direct to security mishaps. For instance, crucial security controls like antivirus and firewall really should generally be enabled. Any error in these options or even if they are accidentally disabled, it serves as an alarming security loophole in an IT network.
Like the higher than security risks, security deviations and posture anomalies are current in an IT infrastructure that are as alarming as a software package vulnerability. Attack surface reduction cannot be obtained only by running CVEs. All the vulnerabilities and security dangers mentioned over will have to be managed rigorously to lessen attack surfaces and battle cyberattacks.
Again, opting for distinct alternatives to control all these vulnerabilities and security threats will only make chaos and complexities. IT security groups should really begin searching for a alternative that mechanically detects and remediates vulnerabilities, IT asset exposures, misconfigurations, security control deviations, and posture anomalies from a single spot. Only a software that treats all these vulnerabilities similarly can satisfy today’s IT security requires and pave the way for a threat-cost-free IT landscape.
[FREE On-demand Event: Join Keeper Security’s Zane Bond in a Threatpost roundtable and learn how to securely access your machines from anywhere and share sensitive documents from your home office. WATCH HERE.]Some elements of this short article are sourced from:
threatpost.com


 Hackers Opting New Attack Methods After Microsoft Blocked Macros by Default
Hackers Opting New Attack Methods After Microsoft Blocked Macros by Default