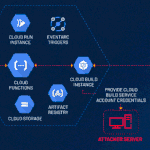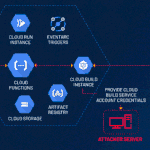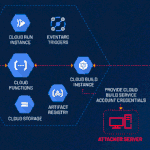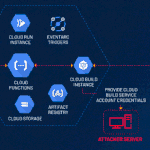
Spanish Hackers Bundle Phishing Kits with Malicious Android Apps
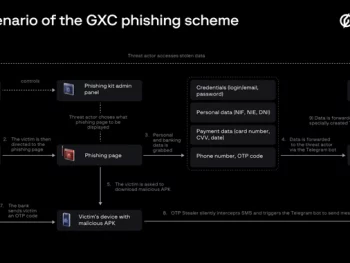
A Spanish-speaking cybercrime group named GXC Team has been observed bundling phishing kits with malicious Android applications, taking malware-as-a-service (MaaS) offerings to the next level. Singaporean cybersecurity company Group-IB, which has been tracking the e-crime actor…
Spanish Hackers Bundle Phishing Kits with Malicious Android AppsRead More

Offensive AI: The Sine Qua Non of Cybersecurity
“Peace is the virtue of civilization. War is its crime. Yet it is often in the furnace of war that the sharpest tools of peace are forged.” – Victor Hugo. In 1971, an unsettling message started…

U.S. DoJ Indicts North Korean Hacker for Ransomware Attacks on Hospitals
The U.S. Department of Justice (DoJ) on Thursday unsealed an indictment against a North Korean military intelligence operative for allegedly carrying out ransomware attacks against healthcare facilities in the country and funneling the payments to orchestrate…
U.S. DoJ Indicts North Korean Hacker for Ransomware Attacks on HospitalsRead More
Ongoing Cyberattack Targets Exposed Selenium Grid Services for Crypto Mining
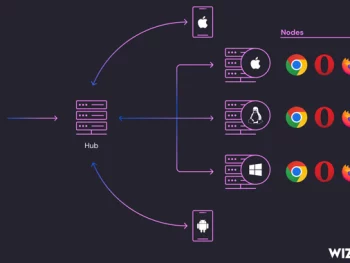
Cybersecurity researchers are sounding the alarm over an ongoing campaign that’s leveraging internet-exposed Selenium Grid services for illicit cryptocurrency mining. Cloud security Wiz is tracking the activity under the name SeleniumGreed. The campaign, which is targeting…
Ongoing Cyberattack Targets Exposed Selenium Grid Services for Crypto MiningRead More

CrowdStrike Warns of New Phishing Scam Targeting German Customers
CrowdStrike is alerting about an unfamiliar threat actor attempting to capitalize on the Falcon Sensor update fiasco to distribute dubious installers targeting German customers as part of a highly targeted campaign. The cybersecurity company said it…
CrowdStrike Warns of New Phishing Scam Targeting German CustomersRead More

Critical Flaw in Telerik Report Server Poses Remote Code Execution Risk
Progress Software is urging users to update their Telerik Report Server instances following the discovery of a critical security flaw that could result in remote code execution. The vulnerability, tracked as CVE-2024-6327 (CVSS score: 9.9), impacts…
Critical Flaw in Telerik Report Server Poses Remote Code Execution RiskRead More
Get the latest news
Subscribe now and get the latest cyber security news in your email.