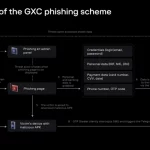
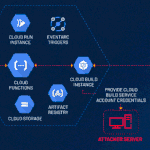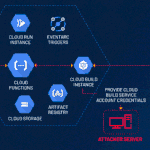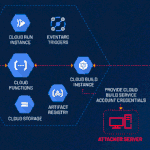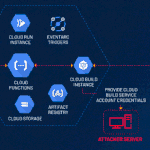
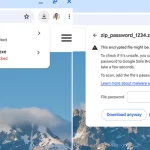
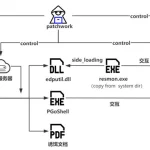
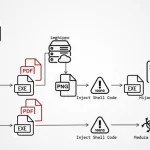
A Spanish-speaking cybercrime group named GXC Team has been observed bundling phishing kits with malicious Android applications, taking malware-as-a-service (MaaS) offerings to the next …
Spanish Hackers Bundle Phishing Kits with Malicious Android AppsRead More