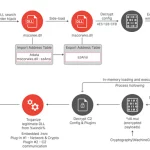
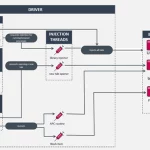
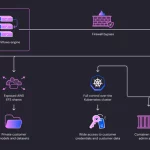
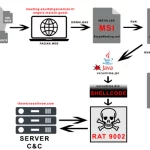
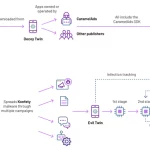
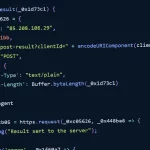
Several organizations operating within global shipping and logistics, media and entertainment, technology, and automotive sectors in Italy, Spain, Taiwan, Thailand, Turkey, and the U.K. have become …
APT41 Infiltrates Networks in Italy, Spain, Taiwan, Turkey, and the U.K.Read More