A team of teachers from Tel Aviv University have disclosed details of now-patched “serious” structure flaws in Android-dependent Samsung smartphones that could have resulted in the extraction of top secret cryptographic keys.
The shortcomings are the final result of an evaluation of the cryptographic structure and implementation of Android’s components-backed Keystore in Samsung’s Galaxy S8, S9, S10, S20, and S21 flagship units, scientists Alon Shakevsky, Eyal Ronen, and Avishai Wool claimed.
Trusted Execution Environments (TEEs) are a protected zone that offer an isolated ecosystem for the execution of Dependable Apps (TAs) to carry out security critical tasks to guarantee confidentiality and integrity.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

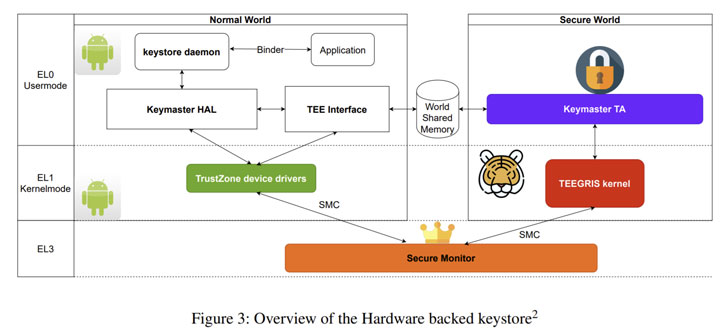
On Android, the hardware-backed Keystore is a technique that facilitates the creation and storage of cryptographic keys inside of the TEE, making them far more hard to be extracted from the system in a way that helps prevent the underlying working procedure from having immediate access.
Instead, the Android Keystore exposes APIs in the variety of Keymaster TA (trustworthy application) to conduct cryptographic operations within just this environment, together with protected vital technology, storage, and its use for electronic signing and encryption. On Samsung cell gadgets, the Keymaster TA runs in an ARM TrustZone-primarily based TEE.
Nevertheless, security flaws uncovered in Samsung’s implementation intended that they could deliver an adversary with root privileges a workable path to recuperate the components-secured non-public keys from the protected aspect. The checklist of issues determined is as underneath –
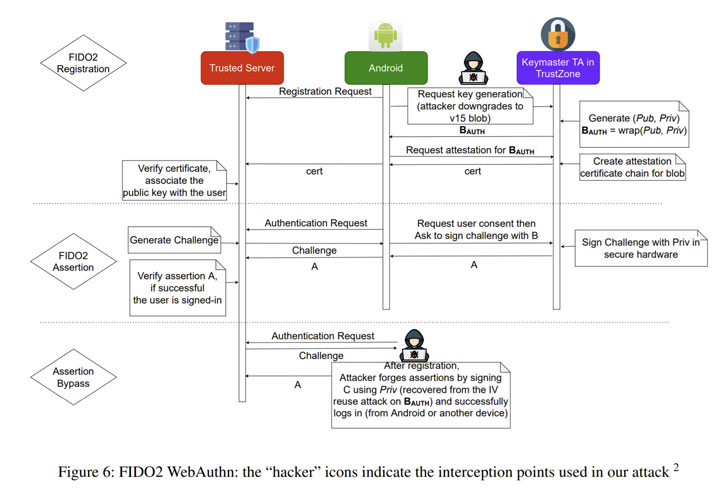
- Initialization Vector (IV) reuse in Keymaster TA (CVE-2021-25444) – An IV reuse vulnerability in Keymaster prior to SMR AUG-2021 Launch 1 lets decryption of customized keyblob with privileged process. (Impacts Galaxy S9, J3 Best, J7 Top, J7 Duo, TabS4, Tab-A-S-Lite, A6 In addition, and A9S)
- Downgrade attack in Keymaster TA (CVE-2021-25490) – A keyblob downgrade attack in Keymaster prior to SMR Oct-2021 Launch 1 permits [an] attacker to induce IV reuse vulnerability with privileged course of action. (Impacts Galaxy S10, S20, and S21)
In a nutshell, productive exploitation of the flaws towards the Keymaster TA could accomplish unauthorized entry to components-guarded keys and facts secured by the TEE. Implications of this kind of an attack could range from an authentication bypass to advanced attacks that can break elementary security ensures presented by cryptographic units.
Subsequent dependable disclosure in Might and July 2021, the issues have been dealt with through security updates shipped in August and Oct 2021 for the affected products. The findings are expected to be presented at the USENIX Security Symposium later this August.
“Suppliers like Samsung and Qualcomm preserve secrecy all over their implementation and design and style of [TrustZone operating systems] and Tas,” the researchers reported. “The style and implementation specifics ought to be properly audited and reviewed by independent researchers and ought to not depend on the problem of reverse engineering proprietary systems.”
Observed this post fascinating? Comply with THN on Fb, Twitter and LinkedIn to read through more unique material we put up.
Some sections of this posting are sourced from:
thehackernews.com



 Conti Group Suffers Massive Data Breach
Conti Group Suffers Massive Data Breach