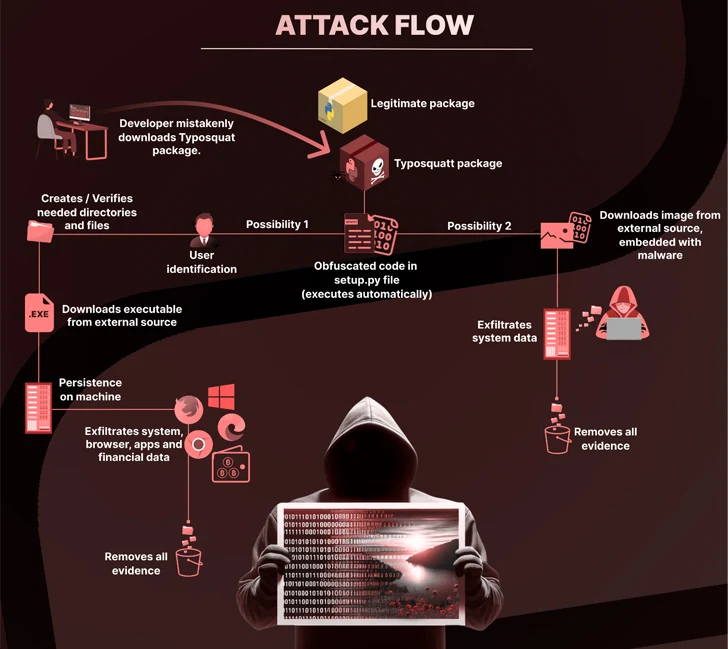
An mysterious threat actor has been noticed publishing typosquat deals to the Python Package Index (PyPI) repository for just about six months with an intention to produce malware able of attaining persistence, stealing delicate details, and accessing cryptocurrency wallets for money achieve.
The 27 offers, which masqueraded as well-liked legitimate Python libraries, captivated countless numbers of downloads, Checkmarx mentioned in a new report. A majority of the downloads originated from the U.S., China, France, Hong Kong, Germany, Russia, Eire, Singapore, the U.K., and Japan.
“A defining attribute of this attack was the utilization of steganography to conceal a malicious payload inside of an innocent-hunting image file, which increased the stealthiness of the attack,” the software source chain security firm reported.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Some of the deals are pyefflorer, pyminor, pyowler, pystallerer, pystob, and pywool, the final of which was planted on May perhaps 13, 2023.
A popular denominator to these deals is the use of the set up.py script to consist of references to other malicious deals (i.e., pystob and pywool) that deploy a Visible Simple Script (VBScript) in buy to obtain and execute a file named “Runtime.exe” to realize persistence on the host.

Embedded inside of the binary is a compiled file that is able of collecting info from web browsers, cryptocurrency wallets, and other applications.
An alternate attack chain observed by Checkmarx is explained to have hidden the executable code in just a PNG image (“uwu.png”), which is subsequently decoded and run to extract the community IP address and the universally exclusive identifier (UUID) of the impacted method.
Pystob and Pywool, in distinct, have been published underneath the guise of applications for API management, only to exfiltrate the info to a Discord webhook and attempt to retain persistence by putting the VBS file in the Windows startup folder.
“This marketing campaign serves as yet another stark reminder of the ever-current threats that exist in present-day electronic landscape, particularly in regions where collaboration and open exchange of code are foundational,” Checkmarx claimed.
The advancement will come as ReversingLabs uncovered a new wave of protestware npm packages that “cover scripts broadcasting messages of peace linked to the conflicts in Ukraine and in Israel and the Gaza Strip.”
One of the offers, named @snyk/sweater-comb (version 2.1.1), establishes the geographic locale of the host, and if it is really uncovered to be Russia, shows a information criticizing the “unjustified invasion” of Ukraine via a further module called “es5-ext”
Yet another offer, e2eakarev, has the description “free palestine protest package deal” in the package.json file, and carries out equivalent checks to see if the IP deal with resolves to Israel, and if so, log what is described as a “harmless protest message” that urges builders to raise awareness about the Palestinian wrestle.
It is really not just risk actors infiltrating open up-resource ecosystems. Previously this week, GitGuardian disclosed the presence of 3,938 overall distinctive strategies throughout 2,922 PyPI assignments, of which 768 unique secrets and techniques ended up observed to be legitimate.
This consists of AWS keys, Azure Lively Listing API keys, GitHub OAuth application keys, Dropbox keys, SSH keys, and qualifications involved with MongoDB, MySQL, PostgreSQL, Coinbase and Twilio.

What is actually a lot more, a lot of of these techniques were leaked extra than at the time, spanning several release variations, bringing the complete variety of occurrences to 56,866.
“Exposing secrets and techniques in open-source offers carries substantial dangers for builders and end users alike,” GitGuardian’s Tom Forbes mentioned. “Attackers can exploit this info to gain unauthorized entry, impersonate offer maintainers, or manipulate buyers by way of social engineering practices.”
The constant wave of attacks concentrating on the application offer chain has also prompted the U.S. govt to issue new direction this thirty day period for program builders and suppliers to maintain and give awareness about application security.
“It is suggested that acquisition organizations assign source chain risk assessments to their getting conclusions specified the modern higher profile computer software provide chain incidents,” the Cybersecurity and Infrastructure Security Company (CISA), Nationwide Security Agency (NSA), and the Workplace of the Director of Nationwide Intelligence (ODNI) stated.
“Software program builders and suppliers ought to increase their program advancement processes and lessen the risk of hurt to not just personnel and shareholders, but also to their customers.”
Found this post interesting? Adhere to us on Twitter and LinkedIn to examine a lot more exceptional material we article.
Some areas of this short article are sourced from:
thehackernews.com


 U.S. Cybersecurity Agencies Warn of Scattered Spider’s Gen Z Cybercrime Ecosystem
U.S. Cybersecurity Agencies Warn of Scattered Spider’s Gen Z Cybercrime Ecosystem