3CX reported it is really working on a software update for its desktop application after various cybersecurity sellers sounded the alarm on what appears to be an active offer chain attack that’s utilizing digitally signed and rigged installers of the popular voice and online video conferencing software to focus on downstream prospects.
“The trojanized 3CX desktop app is the first stage in a multi-phase attack chain that pulls ICO files appended with Base64 knowledge from GitHub and eventually qualified prospects to a 3rd-stage infostealer DLL,” SentinelOne researchers said.
The cybersecurity company is monitoring the action under the name SmoothOperator, stating the menace actor registered a substantial attack infrastructure as significantly back again as February 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
3CX, the organization at the rear of 3CXDesktopApp, claims to have extra than 600,000 prospects and 12 million customers in 190 nations, some of which incorporate nicely-identified names like American Categorical, BMW, Honda, Ikea, Pepsi, and Toyota, amid other individuals.
Though the 3CX PBX consumer is accessible for numerous platforms, Sophos, citing telemetry information, pointed out that the attacks observed so considerably are confined to the Windows Electron client of the PBX phone procedure.
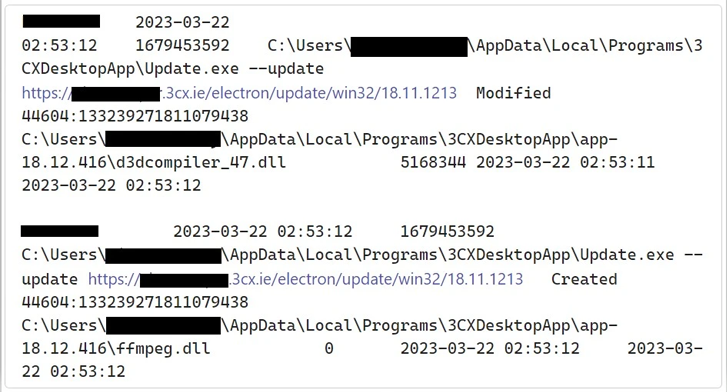
The an infection chain, in a nutshell, takes edge of the DLL aspect-loading strategy to load a rogue DLL (ffmpeg.dll) which is designed to retrieve an icon file (ICO) payload. The GitHub repository hosting the file has considering that been taken down.
The details stealer is capable of collecting technique details and delicate info stored in Google Chrome, Microsoft Edge, Brave, and Mozilla Firefox browsers.
Cybersecurity company CrowdStrike explained it suspects the attack to be joined to a North Korean nation-point out actor it tracks as Labyrinth Chollima (aka Nickel Academy), a sub-cluster within just the infamous Lazarus Team.
WEBINARDiscover the Concealed Potential risks of Third-Party SaaS Applications
Are you conscious of the threats linked with third-party app obtain to your firm’s SaaS applications? Be part of our webinar to discover about the styles of permissions staying granted and how to lower risk.
RESERVE YOUR SEAT
“The malicious activity involves beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a modest range of situations, hands-on-keyboard exercise,” CrowdStrike added.
In a forum publish, 3CX’s CEO Nick Galea reported it can be in the method of issuing a new develop about the upcoming couple of several hours, and mentioned that Android and iOS variations are not impacted. “Unfortunately this occurred since of an upstream library we use grew to become contaminated,” Galea mentioned, without the need of specifying much more facts.
In the interim, the corporation is urging its clients to uninstall the application and put in it yet again, or alternatively use the PWA consumer.
Discovered this article exciting? Observe us on Twitter and LinkedIn to read through more exclusive information we write-up.
Some areas of this short article are sourced from:
thehackernews.com


 Google Warns Against Commercial Spyware Exploiting Zero-Days
Google Warns Against Commercial Spyware Exploiting Zero-Days